- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
smtp/pop3 over SSL - how to configure security rules?
- LIVEcommunity
- Discussions
- General Topics
- Re: smtp/pop3 over SSL - how to configure security rules?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-06-2013 11:37 PM
Hi
I moved my email serwer from untrust to DMZ. Everything almost is working fine, almost ...
This server has ftp and webmail function too, so my security rules looks:
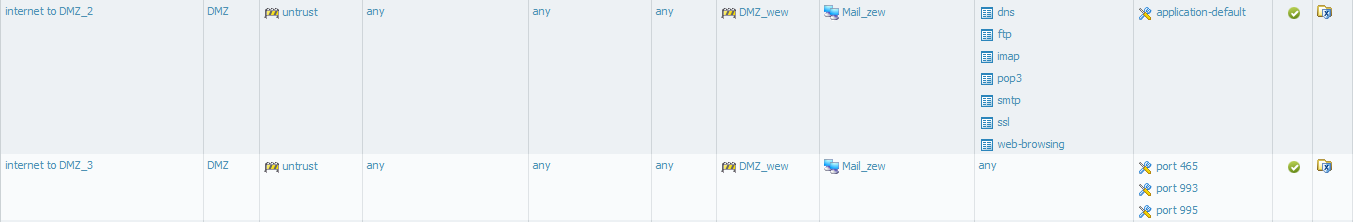
I checked on aplipedia for aplication smtp and pop3. Accroding to aplipedia smtp uses tcp/25,587 and pop3 tcp/110.
Thats true for on secure connections. But how _properly_ pass SSL traffic?
On my server I use ports 465 (smtp) 993 (imap) 995 (pop3) for secures connections.
I'd like to use aplications insted of services like I use now.
I do this as a temporary solution.
Please give my advice how to properly cinfigured security rules in such situations.
With Regards
Slawek
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2013 08:41 AM - last edited on 04-06-2023 08:03 AM by mgordon
Hell Slawek,
Some more investigation lead me to the following document which answers your scenario:
App-IDs for SSL-Secured Versions of Well-Known Services
Hope the above document helps you.
Thanks and regards,
Kunal Adak
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2013 07:23 AM
Hello Slawek,
Since according to applipedia, SMTP and POP3 are not incorporating SSL ports like 995 and 465, you can write a separate rule to include smtp and pop3 and have service as 'any' instead of application-default. In that way, you can make sure that your other applications ftp, dns and web-browsing are still riding on their default ports while allowing SMTP and POP3 on all ports.
Hope that helps.
Thanks and regards,
Kunal Adak
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2013 08:34 AM
Hi Kadak
Thank You for sugestion, I changed my policy.
But I have dubt that this is a right way to make workaround in _such_ simple problem.
I wonder that maybe will be better to change aplication definition and add there my ports. Port that I use are standart and many administrator use the same.
I sow many time on this forum and tech doc's that it's important to use aplication default in service field of policy - because using "any" could be "dangerous".
With Regards
SLawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2013 08:41 AM - last edited on 04-06-2023 08:03 AM by mgordon
Hell Slawek,
Some more investigation lead me to the following document which answers your scenario:
App-IDs for SSL-Secured Versions of Well-Known Services
Hope the above document helps you.
Thanks and regards,
Kunal Adak
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-07-2013 10:56 AM
Hi
Second point looks interesting:
"Create service objects for the SSL-variant ports, and allow 'ssl' App-ID in security policy on those services: SMTPS:TCP/465; IMAPS:TCP/993; POP3S:995; IMAPS:TCP/585."
Is my policy correct?
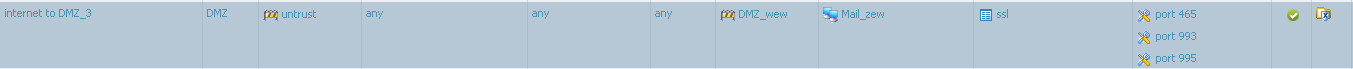
ie. "Port 465" has tcp/465 enabled.
Regards
SLawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2013 02:00 AM
The policy is correct. You allow all applications that are identified as SSL on the 3 ports 465,993,995 in your scenario.
There is no way to modify the app id because the traffic is encrypted. The system can not see what app is trying e.g. to use port 465. So there is only one app called SSL. The only way for the system to identify the app is to use ssl decryption policy. Then you would see which app is using this port.
HTH
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2013 05:30 AM
I understand your explanation.
In my opinion it is mistake to put only one 586port and 25 as a ports for smtp. Most of Us using also different ports too.
Using workaround that provice Kadak we have to make another policy that PA have to process, so we have two policy in every situation where is SSL traffic and regular trafic but on different ports (like in my scenario).
If this is Palo Alto vision - I can't do anything with it
I can't use decryption.
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-08-2013 06:02 AM
Which other way do you see to implement inspection of encrypted data flow?
Have you looked at the data flow chart explaining how the PA dataplane handels traffic? Maybe that helps to understand.
I don´t think there is another vendor that can identify an application that sends encrypted traffic without breaking the encryption. How should this work?
And the ports 25 and 586 are the default ports for smtp (see RFC5321). No matter which other ports you are using.
And there is no problem by creating more than one rule to handle traffic that can not be handled by only one rule. I also created some own services to handle traffic that is not caught by the app-default setting.
I don´t see the main problem you seem to have with the PA way.
cu
- 1 accepted solution
- 17343 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Problem with downloading PAN OS in General Topics
- New articles about how to create signatures without or with AI (ChatGPT/OpenAI) in Custom Signatures
- Security Policy with Destination Criteria in Strata Cloud Manager
- web file blocking in Next-Generation Firewall Discussions
- Palo alto type of license subscription in Next-Generation Firewall Discussions



