- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
ssh (or any) threshold?
- LIVEcommunity
- Discussions
- General Topics
- Re: ssh (or any) threshold?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
ssh (or any) threshold?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2014 05:44 AM
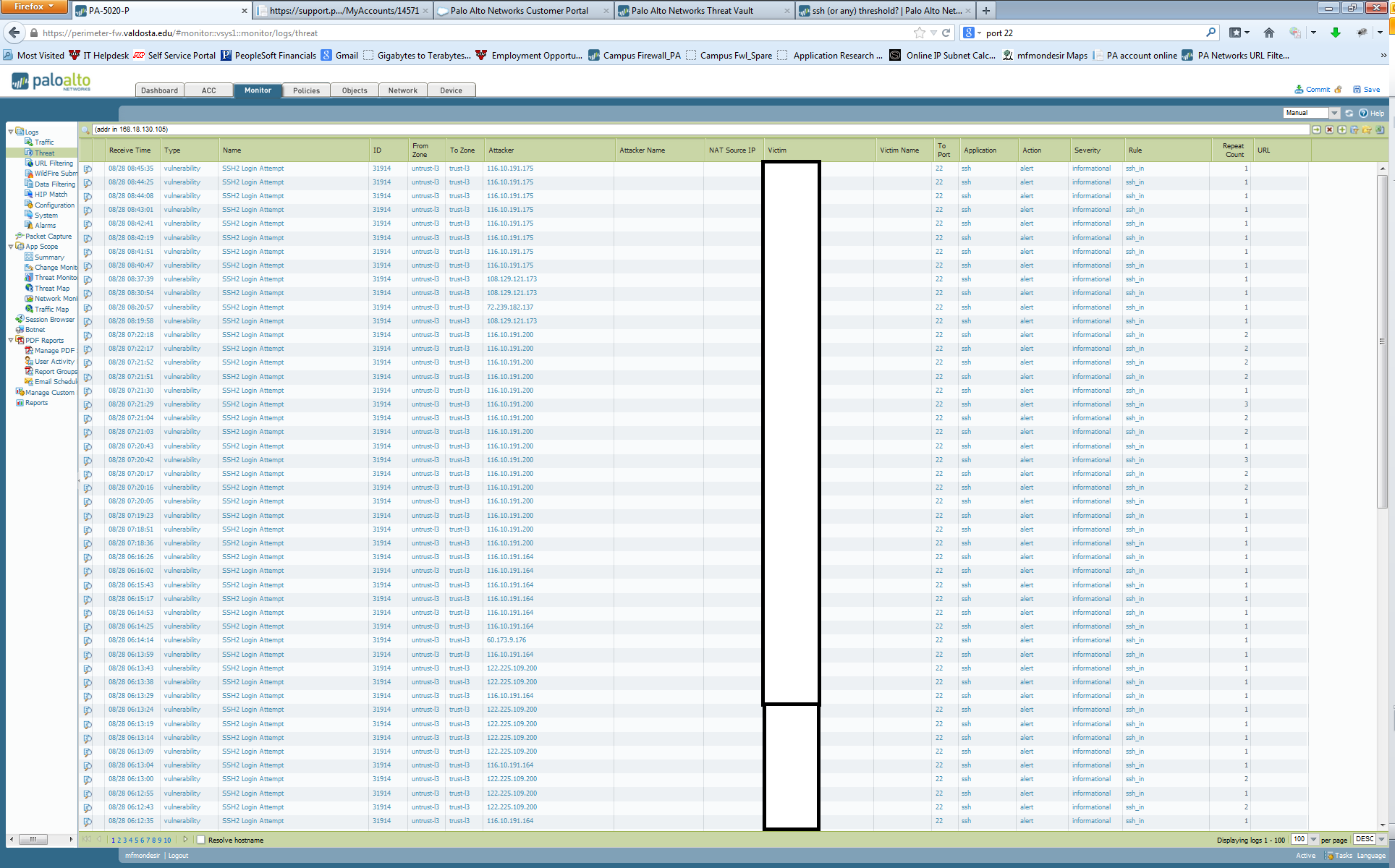
I'm experiencing a ton of hits over ssh to servers that must have ssh access. Is there a way to do threat assessment based on SSH, port etc – and then automatically shut the attack down? For example if a certain IP begins sending all that traffic on port 22 within a certain timeframe – we shutdown the traffic and blacklist the IP. What would be better is to limit this rule to a certain scope – say all of China and Korea where we know attacks tend to happen from – this will help keep down false positives.
thanks
//moe
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2014 06:00 AM
Hi
Are You sure that You have properly configured Threat prevention (enabled on policy that allowing ssh access to servers)?
Look https://threatvault.paloaltonetworks.com/Home/ThreatDetail/40015
there is an id40015 SSH User Authentication Brute-force Attempt signature exactly for Your case.
Regards
Slawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2014 06:14 AM
i believe so. the connections don't match that vulnerability, which i have "reset-both" assigned to it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2014 10:21 AM
Hi VSU,
Try with DOS Protection or Zone Protection. You should be able to cofigure values in it.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2014 12:01 PM
Hi VSU,
Following Signature will not trigger fo 10 attemts in 1 hour. Count is much higher than that. I guess its around 60 per minute as long as I know.
https://threatvault.paloaltonetworks.com/Home/ThreatDetail/40015
Regards,
Hardik Shah
- 5751 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- XSIAM Dashboard in Cortex XSIAM Discussions
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- IPSec HA Failover - Feature Request NSFR-I-26043 in General Topics
- XSIAM Pending Playbooks in Cortex XSIAM Discussions
- Alerting when Daily Ingestion Threshold reaches 80% in Cortex XSIAM Discussions