- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
SSL Inbound // decrypt-unsuppot-pram
- LIVEcommunity
- Discussions
- General Topics
- Re: SSL Inbound // decrypt-unsuppot-pram
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
SSL Inbound // decrypt-unsuppot-pram
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2020 11:35 AM - edited 06-24-2020 11:37 AM
What can i do here..Is it something we have to fix on server side or firewall.
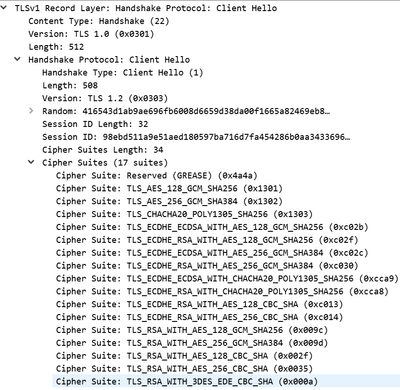
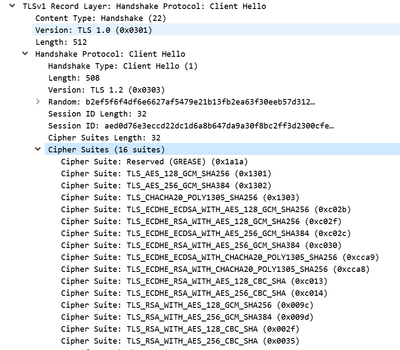
Not Working, Block sessions with unsupported cipher suites, Selected.
Protocols allowed min SSL3.0 to MAX
Working, with Block sessions with unsupported cipher suites, Un-selected.
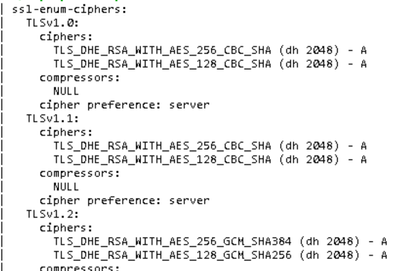
NMAP scan of server
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-24-2020 09:03 PM - edited 06-24-2020 09:05 PM
Was this ever working before or is this the first time you are attempting to decrypt this traffic? Setting up inbound decryption on the PFS ciphers is a bit different then it was previously because the firewall actually needs to proxy the connection instead of just decrypting the traffic in-line like it can with older ciphers.
Also just glancing at your cipher list you have a few being offered that the firewalls doesn't actively support. You'll want to check the available ciphers for your software release as this changes between most major releases and ensure that the firewall supports each being offered.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-25-2020 08:37 AM
@BPry Yes this is my first attempt at inbound decryption, i do have outbound working for few months now.
On comparison for what is supported for 9.0 and what the nmap shows me, i see quite few are common between them.
After enabling inbound inspection namp sees only 2, profile setting for now allows 3.0 to 1.2
So how do i proxy the connection, the only to configure is see is to have the cert on firewall, create decryption profile and attach to decryption policy. Policy/Profile don't seem to provide any option for proxy.
- 2930 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- web file blocking in Next-Generation Firewall Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Header Fields for Syslog for Rapid7 in Next-Generation Firewall Discussions
- Tunnel Traffic from ISP2 IP Working Despite Default Route on ISP1 – Need Insights? in Next-Generation Firewall Discussions
- Help Needed: NAT & Security Policy Configuration for Azure LB → Palo Alto → DMZ Webserver (Public IP) in VM-Series in the Public Cloud