- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Tunnel Monitoring Setup issue
- LIVEcommunity
- Discussions
- General Topics
- Re: Tunnel Monitoring Setup issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2021 09:12 PM
Hello,
I need to enable Tunnel Monitoring for S2S VPN between PA and Cisco ISR Router.
Since, we need to hide our local network behind one IP address given by client (172.x.x.x/32) so we have used that IP address as loopback interface.
There are 2 Tunnels to reach client's remote network and we are using Static route (Primary tunnel with Metric 9 and Secondary Tunnel with metric 10) for this.
Tunnel.1 and Tunnel.2 are configured with VR->Default and Security Zone->VPN without any IP address.
Proxy ID is configured with local address using the masked IP address (172.x.x.x/32) and customer LAN IP as remote address.
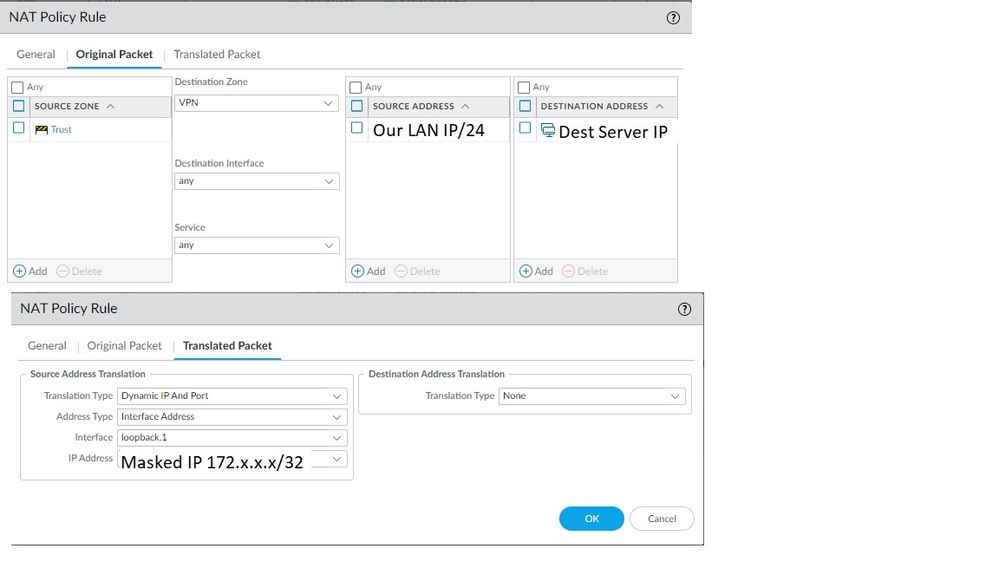
NAT is in place using SNAT like below.
Original Packet:
Source Zone->Trust, Destination Zone->VPN, Source Address->our local network, Destination Address->Customer LAN IP/remote address.
Translated Packet:
Translation Type: DIPP, Interface Address->Loopback Interface, IP Address->172.x.x.x/32
I am not sure what IP address to use as Destination IP in Tunnel monitoring. I understand that this IP will be the one that PAN will ping to verify that tunnel is up. I tried using remote proxyID (customer LAN IP), loopback IP, our local network IP but this causes ping dropouts/request timed out. I tried enabling Tunnel Monitoring in both the Tunnels as well as only one of them (Primary/Secondary).
Any help/suggestion please?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2021 10:49 PM
Hi @Connected123 ,
Having monitoring enabled on the Primary interface only should fulfilled your use case. This is because secondary tunnel routes will always have higher metric and so will be in standby state. Now once Primary tunnel monitoring fails, in that case only traffic will use secondary tunnel. Also it will again failback to Primary once Primary tunnel monitoring is restored. So as per my understanding, having monitoring enabled on primary tunnel should be enough.
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2021 09:16 PM
Hi @Connected123 ,
Here you need to use destination end Server IP address to ping from your side while monitoring. If destination side IP is not responding, you need to verify if destination side has allowed ping traffic via tunnel and/or destination server itself responds to ping.
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2021 10:11 PM
Thank you @SutareMayur for your reply.
Yes ping is allowed from Destination side as continuous ping from our local network to client Server IP is successful.
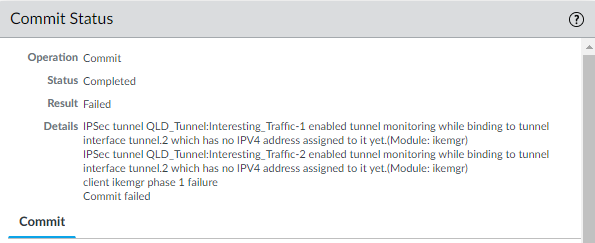
I tried using this Server IP in Tunnel monitoring but got this error message below.
This is simply because there is no IP address configured for the tunnel.1 and tunnel.2 Interfaces.
Only Loopback Interface has IP address as stated in my original post.
I am not sure what other IP I can use in tunnel monitoring. Any idea?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2021 11:11 PM
Hey, you need to configure IP address on your tunnel interface which will act as a source while pinging destination server. Now you can take any free IP from your LAN side to configure IP address on tunnel interface.
NOTE- As you are doing source NAT while sending traffic over tunnel, make sure traffic going from tunnel interface IP should also NATed to desired IP in order to work it.
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2021 11:50 PM
Hi @SutareMayur
Thank you for your suggestion.
I have given dummy IPs to the two tunnel interfaces from our Local IPs (10.x.x.x/24) and made sure they are not referenced anywhere in the network.
Also, created NAT rule below as you mentioned. This has resulted in intermittent Ping request timed out and Tunnel Interface Status of one of the tunnels go down/red.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2021 10:15 AM
Hello,
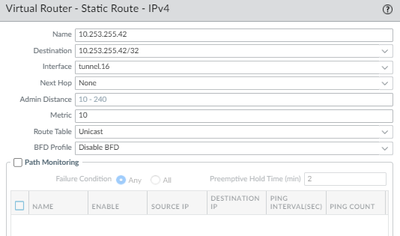
Make sure you have routing configured in your virtual router for the traffic to send down the VPN tunnel. i.e. 'Dest Server IP' interface would be the tunnel and next hop none:
Also make sure there are security policies to allow the traffic.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-27-2021 03:35 PM
Hi @OtakarKlier
Thank you for your response.
Yes both (VR Static route and Policy) are in place as you have mentioned. That is why ping is working but issue is as soon as Tunnel monitoring is enabled (configured as per the previous discussions here) ping drops out intermittently and Tunnel Interface status becomes Red.
Please help!
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2021 10:28 PM
Hi @SutareMayur and @OtakarKlier
I realized that IP addresses need to be added to the Tunnel Interfaces at both ends. Adding dummy IPs only to PA tunnel interfaces do not help with Tunnel monitoring. However, the issue is client end will NOT assign any IP address to the tunnel interfaces of their Cisco router.
In that case, I only have PBF option left to be configured. Is this right?
I tried Path Monitoring but even that requires to create a static route for each tunnel, with a next-hop of the other end of the tunnel subnet. The only accessible addresses via the VPN are 146.x.x.x/24. And this range is not assigned to any addresses on their router.
Thanks in advance
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2021 06:44 AM
Hi @Connected123 ,
I don’t think if tunnel interface IP should have at both ends. If you’re trying to initiate tunnel monitoring using any of the possibilities like tunnel monitoring profile or path monitoring on static route, you can setup it by configuring IP address on your side tunnel interface. And you need to setup monitoring where Palo Alto will check reachability to the destination end server. During this, your side Palo Alto will use tunnel interface IP as source while monitoring destination server’s reachability.
NOTE- In case you need monitoring from both ends to each other, In that case you would need IP address on both sides tunnel interfaces. Also if you are looking to monitor tunnel interface IP configured on peer end, in that case also you would need IP on tunnel interface at peer side. I guess above said scenario (in first para) should work for you because not necessarily every peer end will be always acting a route based VPN, it can be Policy based as well depending on the peer end vendor. Palo Alto always act as Route Based VPN.
Hope it helps!
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-02-2021 07:50 PM
Hi @SutareMayur
Thank you so much for your response.
Yes you are right, I don't need monitoring from both ends to each other.
What I did now is removed the loopback interface as previously configured and added the natt'ed IP address to tunnel.1.
I then selected a random IP address from the NATTed IP range (even though we are given only 172.x.x.x/32) and assigned it to tunnel.2.
I have only enabled Tunnel Monitor on tunnel.1 for the primary tunnel and can see monitor pkts sent increasing.
> show vpn flow tunnel-id 1 | match monitor
monitor: on
monitor status: up
monitor dest: 1.x.x.x
monitor interval: 3 seconds
monitor threshold: 5 probe losses
monitor bitmap: 11111
monitor packets sent: 23411
monitor packets recv: 23365
monitor packets seen: 0
monitor packets reply:0
Do I enable tunnel monitoring for tunnel.2 (secondary tunnel) as well?
Thanks in advance
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2021 10:49 PM
Hi @Connected123 ,
Having monitoring enabled on the Primary interface only should fulfilled your use case. This is because secondary tunnel routes will always have higher metric and so will be in standby state. Now once Primary tunnel monitoring fails, in that case only traffic will use secondary tunnel. Also it will again failback to Primary once Primary tunnel monitoring is restored. So as per my understanding, having monitoring enabled on primary tunnel should be enough.
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2021 12:15 AM
Thank you so much @SutareMayur for all your responses.
You helped me a lot from the beginning to the end of S2S setup.
Really appreciate for taking your time out and answering my questions.
Closing off this thread now.
- 1 accepted solution
- 11984 Views
- 11 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GlobalProtect Always-On (6.3.3-c711) – Users Stuck in “Connecting” State but Still Have Internet Access in General Topics
- Unable to establish tunnel during Service Connection configuration (Details Added with Screenshot) in Prisma Access Discussions
- "More runtime stats" not loading when Advanced routing is enabled in Next-Generation Firewall Discussions
- Limitations Observed with XQL Custom Widgets and Issue Visibility in Cortex XDR Discussions
- Tunnel Monitoring in Next-Generation Firewall Discussions