- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Unnown-TCP application "commvault"
- LIVEcommunity
- Discussions
- General Topics
- Re: Unnown-TCP application "commvault"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Unnown-TCP application "commvault"
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-19-2016 01:58 PM
Hi Guys,
I hope you guys can help with classifying unknown traffic.
I have read many forums for this topic none of which answer my specific question. I understand that should create a custom app if your application bespoke and it is unlikely that an APP-ID would be created.
However, I am expereincing an issue with an application called "commvault" the firewall already recognises this app, but my rule does not work as the traffic is being identified as "unknown-tcp" I do not understand if the firewall already reconises this app why is this being recognised as unknown. Can you also share with me the correct procedure of getting the traffic classified as "commvault" application?
I already have PCAPS from the firewall, but do not know where this should be raised.
Many Thanks,
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-19-2016 02:10 PM
Can you share the traffic log of the "commvault" traffic and the "unkown-tcp" traffic?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 01:28 AM - edited 09-20-2016 01:29 AM
Hi,
In this situation, if an app signature has been created but is not recognising the app correctly then your best bet is to raise a case with TAC, they are very helpful in assisting you so that the right data is gathered and getting the signature modified accordingly so that it is recognised.
You could try and create a custom application for this as well:
https://live.paloaltonetworks.com/t5/Tech-Notes/Custom-Application-Signatures/ta-p/58625
hope this helps,
Ben
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 02:04 AM
yes, please share traffic logs and if possible, please show your security policy
it is possible the version of commvault you are running differs from the traffic pattern included in the AppID version of commvault.
(this can be due to a new updte to commvault or a deployment not seen before by our AppId team,...) if that is the case you'd need to open a support ticket to have the behavior of your commvault app verified and appid updated to include it's patern
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 04:12 AM
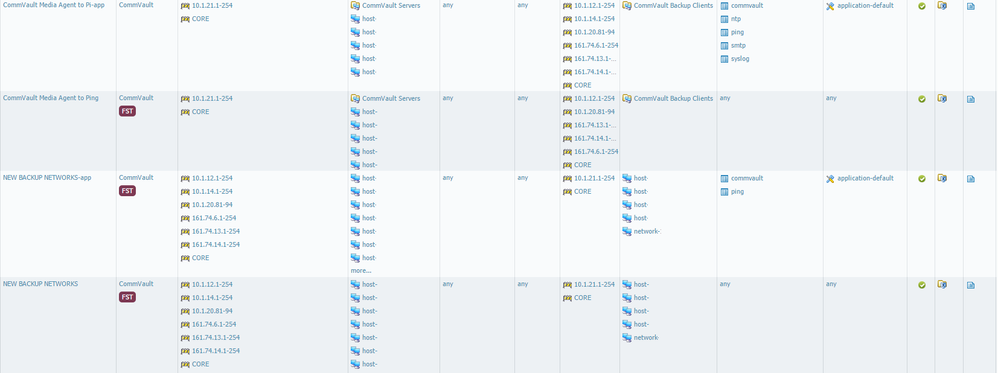
Please see traffic log and the rules that have been created for this.
Please let me know if you guys believe this is correct and if the support route still needs to be followed.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 05:18 AM
you're hitting a deny rule
if you create a security policy that matches the source and destination IP, but leaves the application as any (temorarily), do you still see unknown-tcp ?
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 06:33 AM
This is what I am failing to understand on why it is hitting that deny rule. That deny rule is number 800 in the rule set.
The commvault rules are 600 in the rule set. In the screenshot, that I provided "commVault Media Agent to Ping" & "New Backup Networks" are basically any any rules just set to specfic IP's. They let any application over any service go through. I have checked the correct zones and IP's are in the rule.
When I do a a security policy match from the CLI, the rule matches rule called "NEW BACKUP NETWORKS-app" so I do not understand why unknown-tcp is being hit.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-20-2016 07:04 AM
That's what @reaper was trying to help figure out.
As he stated it's possible there was an update to the APP-ID packge which changed how "commvault" is being idenfitied in your firewall, and while you've properly configured your security policy to use the application it's not matching for that reason.
So he was asking does it match L3 IP-IP (with applicable zones). Then when introducing the L7 application control is it matching or not.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-19-2021 06:25 AM - last edited on 05-19-2021 08:16 AM by jdelio
Hello,
Good Evening,
Please go through this link: https://documentation.commvault.com/commvault/v11/article?p=8572.htm
I hope the above link will help you.
Thanks & Regards,
Anita
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2024 02:45 AM
"Unknown-TCP" traffic from Commvault refers to network traffic generated by Commvault software that is using TCP (Transmission Control Protocol) but is unrecognized or unidentified by the network monitoring system.
This type of traffic can occur due to various reasons such as custom configurations, non-standard ports, or unexpected communication patterns.
Understanding and scrutinizing this traffic is crucial for network security and performance management, ensuring it doesn't compromise network integrity or impede data backup processes.
- 7300 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Outlook and mapi-over-http in General Topics
- Windows-Remote-Management & Implicit Use of Web-Browsing in General Topics
- New articles about how to create signatures without or with AI (ChatGPT/OpenAI) in Custom Signatures
- Security Policy with Destination Criteria in Strata Cloud Manager
- Detect RC4 traffic in Strata Logging Service Discussions