- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
VPN Traffic to Internet
- LIVEcommunity
- Discussions
- General Topics
- Re: VPN Traffic to Internet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
VPN Traffic to Internet
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2023 02:28 AM
Hi Team,
We have a requirement. Our PA Firewall has internet connectivity and VPN set to one of the peer end Forcepoint device.
VPN is up and running. Traffic from Forcepoint LAN to MPLS connected to PA is all working over the VPN.
Now the requirement is ANY traffic from Forcepoint site will reach PA firewall for both its internet and MPLS access.
May i know what needs to be done on PA to allow the access. Default route is pointing to the internet facing interface. ACLs from Site subnet to Internet is allowed. But in the Proxy ID config i have allowed only Site Subnet to MPLS subnet access. Is there anything else needs to be added in the Proxy ID please suggest or anything else i am missing here?
Regards,
Sanjay S
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-08-2023 05:32 AM - edited 09-08-2023 05:33 AM
Looking at the details given, you need to make sure,
- Modify the proxy IDs and Add ForcePoint LAN subnet to ANY (0.0.0.0) entry. This will match internet as well as LAN/MPLS traffic networks. But make sure you have similar VPN encryption domain on other site firewall also.
- You need to check if there is required NAT policy configured on PA to NAT ForcePoint LAN network when going towards Internet.
With this, traffic will hit PA via IPSEC. Once traffic is decrypted on the PA, it should match the internet policy, NAT and do the routing. Response traffic from internet will come back to PA and again pointed to source network routing i.e. on tunnel interface. Here, latency to the internet is expected.
Also, I would recommend you to make changes under maintenance window as there are chances of some outage during the changes and you should be in the position to get some time to t’shoot it.
If it isn’t working post changes, you can check below checks
- What is the status of tunnel ? Is Phase-1 & Phase-2 is up or down?
- In case of any of the phase-2 down, look for system logs filtered with VPN. This will give you some details on reason behind VPN SA down. In such cases, there are chances of having Phase-2 down if there is mismatch in the Proxy ID configuration. It should be identical on both sides.
- If tunnel is up ( both phases ), then check further whether traffic matching right policies for MPLS and Internet, etc.
Hope it helps! Please let me know if you still need any additional help on it, I would be happy to help.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-14-2023 01:28 PM
hi, running into similar problem with watchguard firebox being at remote, PA 7050 at DC end. Tunnel terminates in distinct zone on PA; traffic from remote to on prem works fine but cannot get traffic from remote to Internet which transits tunnel to work. Attempted to update NAT rule to permit tunnel zone without success. Missing something obvious. Topology
watchguard f/b----------public internet--------pa7050-----on premise nets
net 10.255.0.0/23 tun zone internal zone
internet zone
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2023 06:23 AM
When you look at the logs on your PA-7050, do you see the watchguard sending internet destined traffic through the tunnel at all? First thing I'd do here is validate that you're getting that traffic across the tunnel properly, because once that's done it's just a matter of ensuring NAT, security, and routing is all setup properly.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2023 01:08 PM
Hello,
On the IKE Gateway config ->Advanced tab, do you have NAT Traversal enabled?
Also maker sure you have the proper security policies to allow the traffic to flow from the VPN Zone to the 'Untrust" internet Zone. Along with the proper NAT policy. Sometimes the NAT policy is not in high enough, the firewall reads it top-down, left to right, just like the security policies.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2023 01:16 PM
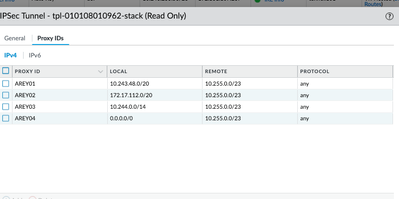
I hear you but that specific tunnel never comes up so the answer would be no, I don't see any traffic destined to public coming thru tunnel. There are three other SA's using the same tunnel and all three come up without an issue. This fourth one is using default and not coming up. Are defaults 0.0.0.0/0 a no-mo with proxy ID's? Here is my proxy-id config that matches on both ends of this delightful set up.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-15-2023 02:06 PM
Hello,
I would not use 0.0.0.0/0 since that would not bring the tunnel up. The Proxy-ID's are like the 'interesting traffic' in the Cisco world. Only the subnets that are on the Far side LAN should be in the proxy ID's, if applicable, and they should match on both sides otherwise the tunnel will not come up.
Do you know if the Watchguard is a route based or zone based VPN?
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000Clh5CAC
Regards,
- 1109 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- AWS plugin to read Tags in AWS in order to be able to create dynamic address object groups and use in policy not working for RDS & lambda in VM-Series in the Private Cloud
- Prisma SD-WAN initial deployment - LAN port in Prisma SD-WAN Discussions
- Insufficient data but still allowed the returning traffic to pass in Next-Generation Firewall Discussions
- Panorama - Failed to update content with following message: encfilesize is 91736928 in Panorama Discussions
- Cisco ACI-Plugin for Panorma: IP Subnet of BridgeDomain not being synced in Panorama Discussions