- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
VPN tunnel to a firewall NOT internet facing
- LIVEcommunity
- Discussions
- General Topics
- Re: VPN tunnel to a firewall NOT internet facing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
VPN tunnel to a firewall NOT internet facing
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-09-2018 02:43 AM
Hi,
I have a scenario with two sites which has two sets (HA) of firewalls, external and internal. So external handles everything internet and behind the internal the datacenter resides. Clients are in between.
We have MPLS between the sites which terminate in the internal firewall.
Now we want to setup site-to-site vpn as a backup for MPLS failure. Since there is a lot of routing in place we would like the tunnels to terminate in the internal firewalls.
How would you setup this? 🙂
NAT, PBF, etc...
Thanks
Magnus
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-09-2018 05:17 AM
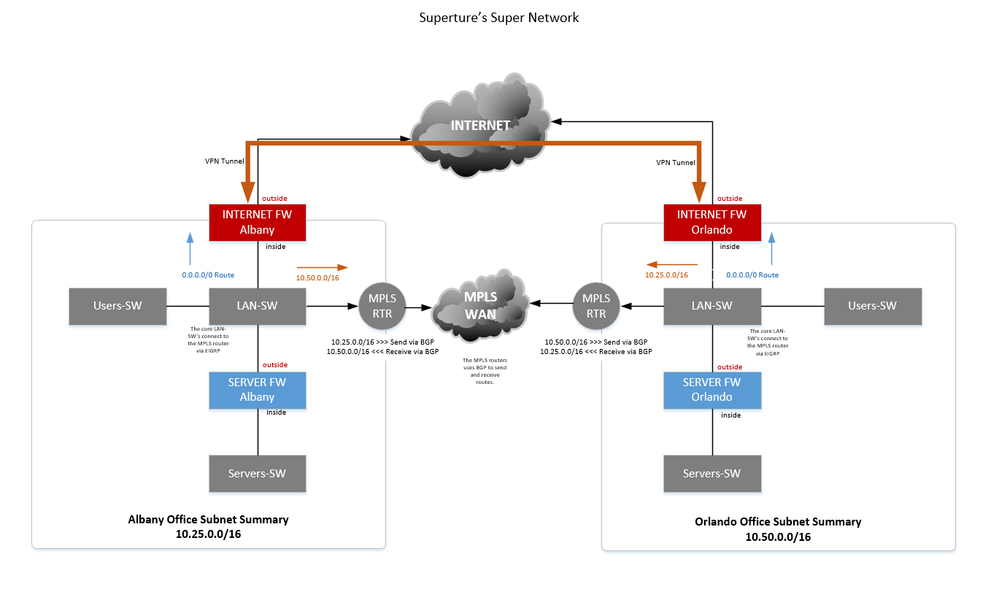
You would normally have a dynamic routing protocol setup to allow traffic from one site to another via your MPLS network. Then you can easily use your default route to send traffic to the Internet firewall for your backup VPN tunnel.
This is an example of how a network would likely be setup to serve the function you describe. When the MPLS goes down, you lose the dynamic routes and the VPN kicks in.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-09-2018 07:03 AM
Haha looks great!
But... suppose we have a lot of static routing and really want to terminate tunnel on the internal firewalls?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-09-2018 08:07 AM
Your routing becomes problematic in the design you are attempting with little benefit. In both scenarios you have your data passing over the Internet inside of an IPSec tunnel. In either method you will need to implement a dynamic routing protocol to have an automated method for path selection.
Also keep in mind that when you have the VPN tunnel on the Internal FW, you will need to setup dynamic routing from your core LAN switch to the FW. Otherwise the Firewall will always pass traffic between servers over the VPN tunnel and it won't use the MPLS.
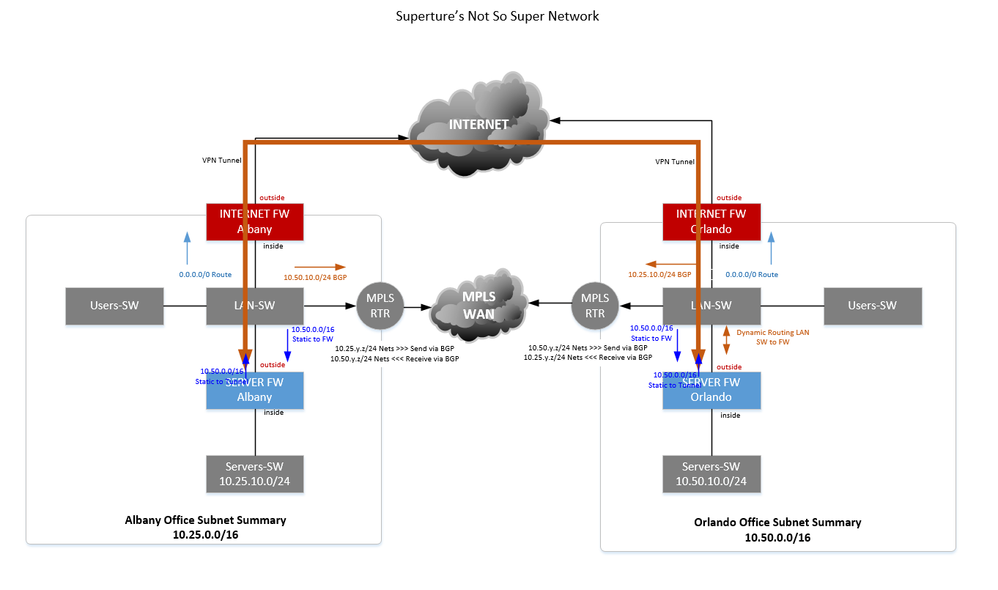
The LAN-SW's at each site will learn a more specific /24 route for the remote office networks and this will be a more prefferred path. Traffic will normally use the MPLS network from site-to-site.
When your MPLS dynamic routing stops (due to circuit or router failure) these specific routes disapear and the next best path are the /16 static routes.
Also remember that all of your FW rules will need to be built with the new VPN tunnel zone as a source or destination on the Server-FW's at each location.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2018 12:58 AM
Thanks!
I'm thinking if I terminate tunnel in the same zone as MPLS on the internal fw and use static route monitor it might work? I realize we could do this much more efficient but that will have to wait for switch refresh I think.
How do I get the tunnel to the internal fw? NAT all the way or PBF maybe?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-16-2018 06:56 AM
Hello,
If you have a lot of static routing then PDF would be your best bet. That way you set your PBF policy to route your primary way with a monitor and the option to 'Disable' the policy if hte monitor goes down. Then your static routes would be setup to use the backup path. This works great because the PBF policies are used prior to the routes in the virtual router.
Hope that helps.
Regards,
- 6473 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access with ECMP in Prisma Access Discussions
- Log forwarding from Cloud NGFW in Azure to Log Analytics Workspace for Sentinel in VM-Series in the Public Cloud
- Not able to log XFF (Actual Client IP) in PaloAlto Logs even when we enable XFF and URL filtering profile in Palo's in Next-Generation Firewall Discussions
- Failover is not occurring on the passive device properly. in General Topics
- Issue with allowing AnyDesk on a no-internet policy in Next-Generation Firewall Discussions