- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
When setting Strict Security Profile
- LIVEcommunity
- Discussions
- General Topics
- Re: When setting Strict Security Profile
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2017 09:05 AM
Good day everyone need help with verify some information about setting strict security profile.
We are wanting to set the all Security profile from default to strict to help contiune doing the best security practices recommend by palo alto. Also not wanting the logging in the threat montior to show traffic we already know is ok. So when we are monitoring threat logging it will only show issues we need to investigate.
After research seeing what will be affect by this change and know that you can add expections to so that strict profile setting should not stop the traffic from contiuning.
How do I verify that traffic is not being stop by the new strict security profile setting?
Thank you any help would be great
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2017 08:51 AM
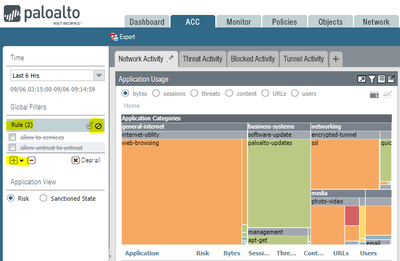
For traffic logs, I usually recommend to "log at session end" for all of the security policies, and then filter out what you don't want to see. This can be accomplished in the ACC as well as the raw logs. One way is to do it by rule name:
This shows you traffic and threats, except for those you specifically filter out in the list. Once you find a view that you like, you can create your own custom ACC tab and have those filters pre-populated.
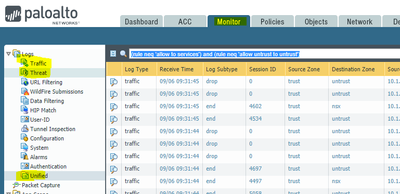
You can do similar things in the traffic, threat, and unified logs with a query like:
(rule neq 'allow to services') and (rule neq 'allow untrust to untrust')
One benefit to this approach is that you still have logs for all of the events, but you're only shown the ones you're interested in.
You're aware of the "log at session start" and "log at session end" options. That governs how traffic is logged for each individual security policy. If, for example, you have an internal application that generates way too many logs and you need to reduce the # of logs being written to disk (to increase log retention time for other traffic logs), then your next option is to not log any traffic through this particular security policy rule.
Afaik, this only affects "traffic logs" (aka traditional firewall logs). You'll still have URL logs, Threat logs, Data Filtering logs, etc. if applicable.
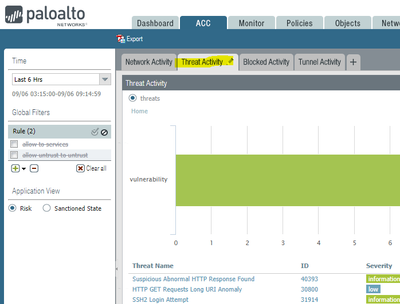
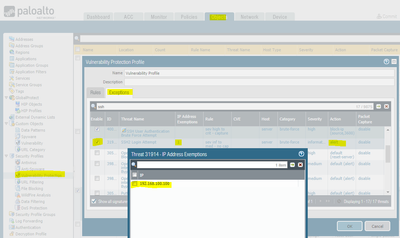
If your goal is to reduce logging for certain threat signatures, that can be done on a case-by-case basis by using security profile "exceptions". Let's say you had a network monitoring server that initatiates SSH sessions to network equipment all throughout your environment and it was generating too many "SSH2 Login Attempt" information alerts in your threat logs. You could add an exception to that profile by a.) enabling the exception, and b.) adding the IP address (source or destination). This action will disable that signature for traffic inspected by this specific profile and to/from the listed IP address.
Hopefully that gives you enough information to accomplish your goals. If not, let us know in more detail what you're trying to accomplish, what you see and what you'd like to see, and we'll figure it out.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2017 10:45 AM
Are you referring to limiting only specific applications or enabling threat prevention and looking for false positives?
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2017 11:57 AM
I think you're likely going to need to include a bit more information in what exactly you are looking to do. Are you talking about only allowing certain applications, upping your vulnerability profiles so that you specify actions other than default, tuning your Antivirus profile?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2017 01:51 PM
Ok, here is the links from the palo alto
His one
https://live.paloaltonetworks.com/t5/tkb/articleprintpage/tkb-id/Management-TKB/article-id/866
How to Add Exempt IP Addresses from the Threat Monitor Logs
search for Vulnerability Protection
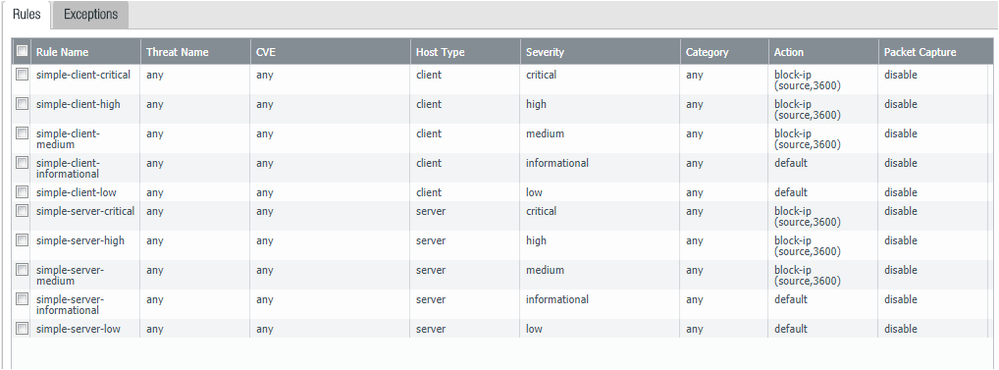
The goal is to when we see something that is critical and high for severity it does just alert it, it stops it by the strict profile settings.
Hope this help make more sense,
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2017 02:45 PM
Hello,
You should be able to accomplish this with a Vulnerability Protection Profile. Objects->Security Profiles-> Vulnerability Protection.
Here I have the polciies to block the offending IP for 1 hour.
Once this is completed you need to add the profile to a Security Polcies to it will take affect. What I usually do is Set all the security Profiles I need and then Bundle ithem into a Security Profile Group, then just apply the group to the security Policy.
Hope that helps!
Cheers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2017 01:39 AM - edited 09-04-2017 01:41 AM
this maybe helpful in understanding (and optimizing) your security profiles:
(security profiles start at about 7:08)
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2017 10:46 AM
Sorry for the late reply
When you use policy that is blocking offending IP for a hour, can you still see the traffic in the Threat monitor logs ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-05-2017 11:56 AM
Hello,
While that response depends on the capacity of the PAN you have and how much traffic is flowing through it, I would honeslty say yes, I am most confident that the logs should be there.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2017 07:14 AM
Thank you Otakar.klier
Is there a way to make those expections not show up in the monitor threat logs?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2017 07:23 AM
Hello,
Maybe someone else has a better way. However what I thought up was to create two Vulnerability policies and two traffic policies. In the first policy you would have traffic that you don’t want logged, i.e. informational or low, etc. and you set the security policy not to log the traffic. The second policy would have the more strict Vulnerability policy and that Security policy would be set to log at session end.
Not sure you would want to do this since you might lose good information when it some to the traffic logs.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2017 07:31 AM
Well, sorry I will explain more on why I would not want to see the traffic that is high that I add execptions listed after change the security profile and setting that security profile to a group profile.
There is traffic that is showing in the monitor threat area as high, I know this traffic is required for business to run plus it the traffic is going cross zone.
I was thinking it would be better when I am monitor threat logs to see traffic that I need to do research in to make sure that is business approved traffic. Also it will clean up a lot of traffic that is not need to be seen in my thinking.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2017 07:52 AM
Another thought could be to just let the PAN log everything and then filter the view to only things you want to see?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-06-2017 08:51 AM
For traffic logs, I usually recommend to "log at session end" for all of the security policies, and then filter out what you don't want to see. This can be accomplished in the ACC as well as the raw logs. One way is to do it by rule name:
This shows you traffic and threats, except for those you specifically filter out in the list. Once you find a view that you like, you can create your own custom ACC tab and have those filters pre-populated.
You can do similar things in the traffic, threat, and unified logs with a query like:
(rule neq 'allow to services') and (rule neq 'allow untrust to untrust')
One benefit to this approach is that you still have logs for all of the events, but you're only shown the ones you're interested in.
You're aware of the "log at session start" and "log at session end" options. That governs how traffic is logged for each individual security policy. If, for example, you have an internal application that generates way too many logs and you need to reduce the # of logs being written to disk (to increase log retention time for other traffic logs), then your next option is to not log any traffic through this particular security policy rule.
Afaik, this only affects "traffic logs" (aka traditional firewall logs). You'll still have URL logs, Threat logs, Data Filtering logs, etc. if applicable.
If your goal is to reduce logging for certain threat signatures, that can be done on a case-by-case basis by using security profile "exceptions". Let's say you had a network monitoring server that initatiates SSH sessions to network equipment all throughout your environment and it was generating too many "SSH2 Login Attempt" information alerts in your threat logs. You could add an exception to that profile by a.) enabling the exception, and b.) adding the IP address (source or destination). This action will disable that signature for traffic inspected by this specific profile and to/from the listed IP address.
Hopefully that gives you enough information to accomplish your goals. If not, let us know in more detail what you're trying to accomplish, what you see and what you'd like to see, and we'll figure it out.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2017 10:53 AM
Hey jvalentine
I do not use the ACC much, maybe I should look into that more.
This seems to me to answer my questions about logging
.
With the help of Otakar.kKlier on knowing how the security profile will affect as well what i will still see in logging so be a enough to get this going
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-07-2017 12:16 PM
I would highly recommend getting to know your way around the ACC. It's an astounding resource when you know how to use it properly and filter to what you actually want to see.
- 1 accepted solution
- 11645 Views
- 17 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma Access Explicit Proxy — Anti‑Spyware behavior when DNS bypasses Prisma (logging subtype + test methodology) in Prisma Access Discussions
- Possible to disassociate global snippets from SCM? (Total number of security profiles exceed platform capactity) in Strata Cloud Manager
- GlobalProtect Name Normalization issue in GlobalProtect Discussions
- Issue after onboard Azure VM into SCM in Strata Cloud Manager
- PA-415-5G not working with fresh T-Mobile SIM in General Topics