- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
working process behind policy with multiple depended applications
- LIVEcommunity
- Discussions
- General Topics
- Re: working process behind policy with multiple depended applications
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2018 06:01 PM
I was little ambigous on how Palo alto processes a policy. let say i have a policy with 3 applications(a,b,c) in application field and multiple service ports(1,2,3) is there a chance that one of the application(a or b or c) specified in my application field is also being allowed on ports other than what it meant be allowed (say A must be allowed on port 1,but it is also communicating via 2 or 3).
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2018 10:27 PM
If you have 3 apps and 3 ports, then any of the apps can match any of the listed services.
App A could be communicating on port 1, 2 or 3. Same for app B and app C.
When grouping multiple items in a policy element, it's an OR statement. The traffic must match application A OR B OR C and it must match service 1 OR 2 OR 3. So A + 3 or B +1 are both valid matches.
If you need to restrict App A to a single port, you'll need to use a unique security policy rule.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-22-2018 01:24 AM
@rmfalconers statement is correct regarding the 'OR' property of any object added to the same field in a secureity policy (app A or B or C)
but
if you enable 'application-default' in the services, instead of using singular service objects, all applications used in security policy will only be matched against their own default ports (visible in the application properties) while other apps will not be allowed to re-use those ports unless they are listed in their own properties
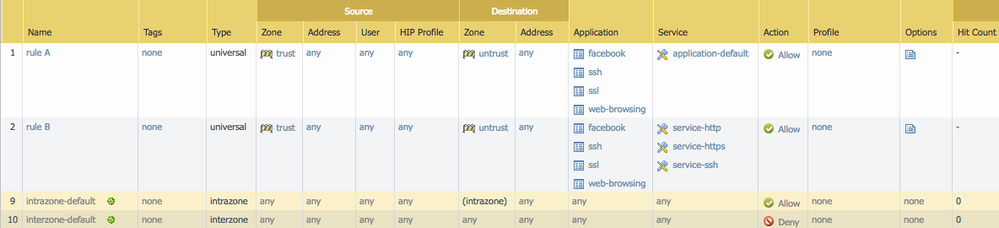
as an example look at rule A and B below. they are identical except for the services:
Rule B will allow facebook, ssl and web-browsing on tcp 22 and ssh on tcp 80 and 443
Rule A will allow ssh on tcp 22, but not tcp 80 or 443, web browsing (cleartext http) on tcp 80 but not 443 or 22, ssl on port 443, but not 22 or 80
so you will not need to create a single rule per application, you only need to use application-default to prevent applications re-using other applications' ports
PANgurus - Strata & Prisma Access specialist
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-21-2018 10:27 PM
If you have 3 apps and 3 ports, then any of the apps can match any of the listed services.
App A could be communicating on port 1, 2 or 3. Same for app B and app C.
When grouping multiple items in a policy element, it's an OR statement. The traffic must match application A OR B OR C and it must match service 1 OR 2 OR 3. So A + 3 or B +1 are both valid matches.
If you need to restrict App A to a single port, you'll need to use a unique security policy rule.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-22-2018 01:24 AM
@rmfalconers statement is correct regarding the 'OR' property of any object added to the same field in a secureity policy (app A or B or C)
but
if you enable 'application-default' in the services, instead of using singular service objects, all applications used in security policy will only be matched against their own default ports (visible in the application properties) while other apps will not be allowed to re-use those ports unless they are listed in their own properties
as an example look at rule A and B below. they are identical except for the services:
Rule B will allow facebook, ssl and web-browsing on tcp 22 and ssh on tcp 80 and 443
Rule A will allow ssh on tcp 22, but not tcp 80 or 443, web browsing (cleartext http) on tcp 80 but not 443 or 22, ssl on port 443, but not 22 or 80
so you will not need to create a single rule per application, you only need to use application-default to prevent applications re-using other applications' ports
PANgurus - Strata & Prisma Access specialist
- 2 accepted solutions
- 2819 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Modify Security Policy rule - application depends on in General Topics
- QOS for SIP Questions in General Topics
- Custom App-ID with just source and destination ip address in Custom Signatures
- Fuel Spark Event Discussion: Identity Management/Zero Trust and Quantum Security (August 22, 2024) in General Topics
- Export/Import filters in Cortex XDR Discussions