- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
DNS lookup takes a long time with GP
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Re: DNS lookup takes a long time with GP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-20-2021 11:39 PM
GlobalProtect Gateway is being used, and all traffic is being routed to the firewall except for some network.
DNS lookup takes a long time when I input the domain (website which not in the PC DNS table) that the browser accesses first while connected to a VPN
- DNS Lookup time takes about 5-10 seconds
The DNS server is using an internal server, and the network is belong to split tunneling exceptions.
I am wondering why DNS lookup processing is delayed.
Or is it correct that DNS lookup takes a long time during VPN connection?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-03-2021 07:20 PM
The issue was resolved as follows.
Cause: Querying queries to all NICs that have DNS Lookup enabled, so lookup time increases while waiting for results from VPN NIC
Resolution: Register in paloalto registry to run batch script after VPN authentication.
The script content deletes the DNS Server settings of the VPN NIC to set DNS queries to use only the primary NIC of the PC.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-21-2021 07:41 AM
Do you also have GP app setting to split tunnel DNS and what GP client version are you using?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-21-2021 05:11 PM
GP Client version is 5.2.6-87(latest)
And Split-Tunnel Option is "Both Network Traffic and DNS" from GP-Portal-Agent-Config-App
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-21-2021 10:10 PM
Try removing that setting from the agent to see if that is the issue.
are you testing with a dns lookup tool/app or in the browser itself.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-21-2021 10:15 PM
That option was initially "Network Traffic Only", but DNS Lookup took a long time, so I switched to "Both Network Traffic and DNS".
The test is being done on my PC, and the DNS cache table is checked with the "ipconfig /displaydns" command.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-22-2021 12:00 AM
are you adding the url in nslookup or just adding it in the browser
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-22-2021 01:27 AM
I do not add additional URL.
For my case, the DNS server belongs to the split tunneling exception, so the dns server is left blank in the gateway-agent-network service configuration.
So DNS uses PC's default DNS settings.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-22-2021 02:14 AM
This does not happen when i do the same.
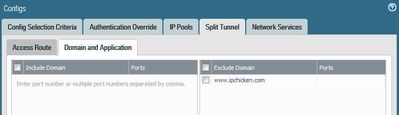
I have 1 domain in "Domain Split Tunnel" and have left my DNS servers blank in the gateway services and have set both network and DNS in portal app.
as soon as i browse to the website that is in my split tunnel it resolves instantly with my local DNS.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-23-2021 01:12 AM - edited 04-23-2021 01:26 AM
As you said, I call the internal DNS server and get the IP right away.
However, the browser notificate that the host is being searched, and the DNS lookup time is very long.
Looking through wireshark during this time, vpc nic are not communicating with the target website.
The chrome/edge browser issue are the same. It doesn't appear to be a browser issue.
In summary
1. vpn connect
2. connect to website domain from browser, connect to internal DNS server from pc default nic
3. get IP from internal DNS server (There seems to be no problem so far.)
4. (vpn nic) The browser is looking for the host, and this is taking a long time.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-23-2021 01:26 AM
If you are using wireshark then what happens to the packet captures when the DNS replies in summary 3. does it pause or do you see connection attempts to the correct address.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-25-2021 05:44 PM - edited 04-25-2021 06:54 PM
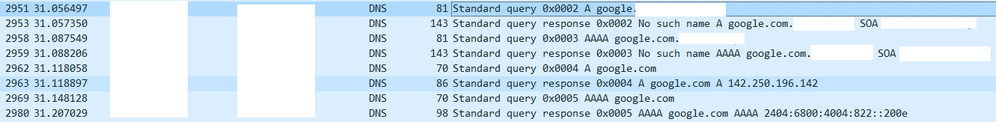
This packet is a capture of DNS query with nslookup command on PC's origin NIC(not VPN NIC).
The first second query is the result of a query against the DNS suffix, and the last is the correct query result.
Further confirmation
The VPN NIC also sends query packets to the internal DNS.
(Packets come into the Paloalto firewall. It doesn't seem to apply to the split-tunneling exception.)
Information
1. Not all queries are requested, but only a few packets request duplicate DNS queries using Origin NICs and VPN NICs.
2. Packets requested by the VPN NIC only have a request and no response.
3. If the DNS lookup in the web browser takes a long time and the web page is displayed normally, the query packet is only sent to the PC NIC, and the packet is not generated from the VPN NIC.
It seems to be because the DNS query is being called concurrently with the PC NIC and VPN NIC.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-03-2021 07:20 PM
The issue was resolved as follows.
Cause: Querying queries to all NICs that have DNS Lookup enabled, so lookup time increases while waiting for results from VPN NIC
Resolution: Register in paloalto registry to run batch script after VPN authentication.
The script content deletes the DNS Server settings of the VPN NIC to set DNS queries to use only the primary NIC of the PC.
- 1 accepted solution
- 11861 Views
- 12 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- user-id - Firewall is not learning upn name format in Next-Generation Firewall Discussions
- Automatically choose REST API version in Panorama Discussions
- GlobalProtect client takes extra time to disconnect in GlobalProtect Discussions
- BFP with OSPF graceful restart causing outages during failover in Next-Generation Firewall Discussions
- impact of Graceful Restart in the routing table reconvergence in Next-Generation Firewall Discussions