- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global Protect HIP Check and AD Computer Account
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- Global Protect HIP Check and AD Computer Account
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Global Protect HIP Check and AD Computer Account
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2023 04:31 AM
Hello,
I'm currently trying to restrict Global Protect users from logging into the Portal or Gateway with unauthorized devices.
In our setup, all devices that are allowed to connect (mobile, laptops, desktops, etc.) are listed in an Active Directory OU (computer account).
I have been unable to find any information on how to configure this restriction in the official documentation or through online resources.
Is it possible to implement this limitation?
Thanks,
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2023 07:12 PM
Hi @BusanaB ,
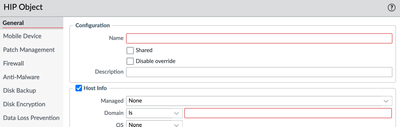
One method you could use is to verify the domain retrieved under host info:
If the domain matches the HIP object, then it is a device in the domain.
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2023 03:31 PM - edited 07-20-2023 03:43 PM
Hi,
The most secure way of checking this I using certificates, checking if the connecting client is using a certificate distributed by your companies PKI.
You can even deploy separate certificates per device type using extended key usage and check on the specific OID. (Microsot PKI)
On top of the client cert user or machine cert you add SAML/LDAP/RADIUS authentication.
Or you can do the check for allowed on you authentication backend RADIUS (NPS/ISE). But this will not disallow users from connecting to portal and trying to authenticate on it. Can only be achieved with certificates.
- 3771 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Cannot log into global protect, testing configuration on EVE-NG in GlobalProtect Discussions
- PANGP virtual ethernet driver in GlobalProtect Discussions
- Clientless VPN and Remote Desktop in Next-Generation Firewall Discussions
- Remote Desktop Connection to a Global protected PC behind a private Azus Router in GlobalProtect Discussions
- global protect vpn client -> microsoft edge -> pick an account - multiple microsoft-accounts and member of different m365 tenants in GlobalProtect Discussions