- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GlobalProtect Pre-Logon Prompting for User Certificate
- LIVEcommunity
- Discussions
- Network Security
- GlobalProtect Discussions
- GlobalProtect Pre-Logon Prompting for User Certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
GlobalProtect Pre-Logon Prompting for User Certificate
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2021 06:25 AM
We have GlobalProtect Pre-Logon working with machine certificates however once the user logs into their laptop they are also prompted with thier User Certificate each time. There internal CA does issue machine and user certificates. Is there a way to disallow the User certificate prompt? Do we need to also use User certificates along with machine certficicates? Verion is 10.0.7 and GP 5.2.7
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-25-2021 06:19 PM
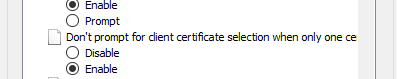
You need to ensure the portal and gateway URLs are added to your trusted/Intranet sites in IE and ensure this setting is enabled.
For Edge and Chrome you need to configure "AutoSelectCertificateForUrls" to avoid the pop-up
Microsoft Edge Browser Policy Documentation | Microsoft Docs
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-10-2022 09:16 AM
This looks similar to an issue we are seeing on our Win 11 intune build and the Hello for business cert, we have added the urls and the cert to use and are able to browse to the page in a web browser without being prompted. If we remove the WHFB cert the device does not prompt. do we need to add to the ie trusted sites and enable the dont prompt for client certificate selection?
Any help or advice would be much appreciated
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-14-2022 09:27 AM
I have the same question. We are in the process of deploying Windows Hello for Business authentication certificates which need to be in the UPN format. The PaloAlto Global Protect Client needs the user authenticaiton certs in the CN format. The issue we are seeing is that now Global Protect is prompting for which certificate to use because there are now two authentication certificates in the users personal store. How to we force GlobalProtect Client to connect and use a certificate without prompting in the client? Is there a way to tell the GlobalProtect Client to use a certain certificate in the registry?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-14-2022 09:37 AM
The easiest way to do this is to use a custom OID for the GlobalProtect certificates so that you can automatically select the proper certificate based on the OID value. That will have it default to the proper certificate without prompting for selection.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-14-2022 10:23 AM
Thank you for this info. Will try this approach. Have a great day!
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-18-2024 06:29 AM
So you know this approach does work if you are only publishing one certificate for the user. and one for the machine. We created one for the machine with a unique OID for prelogon purposes. Then we created another for the user with a unique OID for user logon purposes. The User Auth Certificate had client authentication purpose and enrolls into the Software Key Storage provider. Things were working fine and Global Protect was selecting the proper certificate to authenticate depending on the prelogon and logon states. With Windows Hello, we had to enroll a certificate into the Windows Hello for Business Certificate Keystore for Remote Desktop Services to work using Biometric, Pin, or Fingerprint. This certificate does not have an OID and has client authentication purposes. Technically speaking the WHFB certificate should be completely ignored when Global Protect is connecting because it does not hava an OID. Both of these Certificates appear in the User's Personal Certificate store in Windows. What we are finding is that Global Protect still presents the user for Certificate selection when connecting. Global Protect, searches all Certificates and if there are multiple that have the Cliient Authentication Purpose, it prompts the employee and does not honor the OID. To me this is a GP bug, because Global Protect should use its conifguration stating to look for the OID to connect automatically and not prompt the user. We have tried to change to SAML SSO Authentication and get the exact same thing with the certificate selecting promting to the user. The challenge is that we need both of the user certificates. I do think that Palo Alto should fix this as more and more people are migrating to Passwordless solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-19-2024 10:39 AM
Do you have a doc you followed to get this working?
I have been fighting with the prelogon and userlogon certs. Prelogon works fine, but the minute it goes to userlogon it errors out with invalid cert. Turns out it's trying to use the machine cert to do a userlogon. I have tried a ton of different settings and cannot figure this out.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2024 08:31 AM - edited 05-31-2024 08:34 AM
Hi following up on this. Right now it appears that PaloAlto does not have a sound solution for Passwordless Authentication. We have tried two different things (SAML AUTH and Cert Auth) and both of the configs do work, but both have Certificate Popups for VPN which confuses end-users. When I researched how GlobalProtect behaves, it uses the default browser to prompt for certificates. When multiple certificates of the client authentication purpose type are presented, then GlobalProtect prompts the user. You would think, it would just automatically select the certificate with the OID for logon, but it does not. The way it works is that Global Protect uses the default browser to select a certificate. The way Edge works is that it automatically selects the certificates based on the order that they appear. In our case the WHFB (non-OID) is first, but does not have the OID and thus the user is prompted.
OUR SETUP
We have deployeed 3 x certificates via Intune SCEP to end user devices (1 x for Machine unique OID for PRELOGON) and (2 x for User, one with a unique OID for LOGON and the other for WHFB). The PA Appliance is configured to only use the machine OID for Prelogon and then the user OID for logon.
PRELOGON- The machine cert is real easy. Go into AD and create a cert template with a custom OID https://learn.microsoft.com/en-us/mem/intune/protect/certificates-scep-configure. Then create a SCEP profile in Intune and target your device group. Set up your PA to look for the OID and use Cert Auth for PreLogon connection. You need to ensure the Cert has both the Machine Name and the AAD Device Id in it for different auth services like Radius for Wired/Wireless and VPN. We set up prelogon as cert auth because we want people to be connected to the vpn prior to logging into the pc to be able to create the windows profile when they sign in for the first time.
LOGON- The user Logon piece is the challenge. We deploy one User certificate via Intune SCEP with a OID the first time someone logs into a pc. This goes into the User's Personal Cert Store in Windows. We then have to deploy a user Cert to the Windows Hello for Business keystore (stored in TPM) when devices enroll into WHFB. This cert is used for the users Primary Refresh Token to validate the Biometric Credential in Azure/Entra and prove it is a legit credential to sign into M365 services. The 2 x user certificates are a necessary config requirement, but GlobalProtect does not honor the OID and forces a pop up for the end user to select a certificate. See my explanation above.
SAML
With SAML, we have created an enterprise application that basically leverages the user certificate to automatically pass them to the GP Portal, through the Azure/Entra IDP, then establish a VPN connection. This does work, but at logon, the GP VPN is connected using the machine cert and not automatically flipped over to the user cert once fully in windows. The vpn is connected, but still on Prelogon. You have to click the GP VPN and click connect, which will open a webpage to authenticate to the VPN portal. Then there are Certificate prompts for the Portal (not user friendly), then a prompt to open the link using GlobalProtect (not user friendly), then you click Connect in GP VPN, then to another webpage for the gateway then again a cert prompt for the Gateway (not user friendly), then one to open the link (not user friendly). Finally the VPN is connected via SAML and the end user Certificate.
We figured out how to supress the Certificate and Link prompts in Edge with AutoSelectCertificateForUrls and AutoLaunchProtocolsFromOrigins config settings. You also have to add the portal and gateways to the trusted internet sites zones in IE configs. This has improved the experience, but with each reboot, the end user has to repeat the process above minus the Cert and Link prompts.
Palo Alto needs to create a way to simply honor the biometric as a credential and cache it in the GP app. This would solve everything. Right now everythign is clunky and simply making us want to go clientless VPN.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-31-2024 08:32 AM
OUR SETUP
We have deployeed 3 x certificates via Intune SCEP to end user devices (1 x for Machine unique OID for PRELOGON) and (2 x for User, one with a unique OID for LOGON and the other for WHFB). The PA Appliance is configured to only use the machine OID for Prelogon and then the user OID for logon.
PRELOGON- The machine cert is real easy. Go into AD and create a cert template with a custom OID https://learn.microsoft.com/en-us/mem/intune/protect/certificates-scep-configure. Then create a SCEP profile in Intune and target your device group. Set up your PA to look for the OID and use Cert Auth for PreLogon connection. You need to ensure the Cert has both the Machine Name and the AAD Device Id in it for different auth services like Radius for Wired/Wireless and VPN. We set up prelogon as cert auth because we want people to be connected to the vpn prior to logging into the pc to be able to create the windows profile when they sign in for the first time.
LOGON- The user Logon piece is the challenge. We deploy one User certificate via Intune SCEP with a OID the first time someone logs into a pc. This goes into the User's Personal Cert Store in Windows. We then have to deploy a user Cert to the Windows Hello for Business keystore (stored in TPM) when devices enroll into WHFB. This cert is used for the users Primary Refresh Token to validate the Biometric Credential in Azure/Entra and prove it is a legit credential to sign into M365 services. The 2 x user certificates are a necessary config requirement, but GlobalProtect does not honor the OID and forces a pop up for the end user to select a certificate. See my explinaiton above.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-27-2025 06:12 AM
@rheinrich wrote:
OUR SETUP
We have deployeed 3 x certificates via Intune SCEP to end user devices (1 x for Machine unique OID for PRELOGON) and (2 x for User, one with a unique OID for LOGON and the other for WHFB). The PA Appliance is configured to only use the machine OID for Prelogon and then the user OID for logon.PRELOGON- The machine cert is real easy. Go into AD and create a cert template with a custom OID https://learn.microsoft.com/en-us/mem/intune/protect/certificates-scep-configure. Then create a SCEP profile in Intune and target your device group. Set up your PA to look for the OID and use Cert Auth for PreLogon connection. You need to ensure the Cert has both the Machine Name and the AAD Device Id in it for different auth services like Radius for Wired/Wireless and VPN. We set up prelogon as cert auth because we want people to be connected to the vpn prior to logging into the pc to be able to create the windows profile when they sign in for the first time.
LOGON- The user Logon piece is the challenge. We deploy one User certificate via Intune SCEP with a OID the first time someone logs into a pc. This goes into the User's Personal Cert Store in Windows. We then have to deploy a user Cert to the Windows Hello for Business keystore (stored in TPM) when devices enroll into WHFB. This cert is used for the users Primary Refresh Token to validate the Biometric Credential in Azure/Entra and prove it is a legit credential to sign into M365 services. The 2 x user certificates are a necessary config requirement, but GlobalProtect does not honor the OID and forces a pop up for the end user to select a certificate. See my explinaiton above.
We faced exactly the same issue a few years ago. We did solve it by not using a custom OID. We used the pre-existing OID Remote Desktop Authentication (1.3.6.1.4.1.311.54.1.2) and this worked!
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2025 03:17 AM
Unfortunately, this doesn't work on our end. We used the OID for "IPSec User" that PaloAlto provides as an example in their article Enable Certificate Selection Based on OID. However, the certificate selection popup still appears, even though the other certificates don't have this OID.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-11-2025 08:13 AM - edited 07-11-2025 08:15 AM
This is good to know. What I have discovered is that the prompting is hit or miss depending kn the GP version. We are on 6.3.2 and we have every thing silently hidden and selecting the certificate through the Edge prompt on duplicate certificate setting. If we move to 6.3.3, then the prompting comes back at every reboot. This is most certainly a bug in the Global Protect behavior. We have submitted tickets. The prelogon should only search the machine cert store and the logon should only search the user personal store. And both should only select the certificate with the proper OID without prompting unless there are two with the same OID. We have one OID for user and one OID for machine. Additionally, we are seeing that the registry values themselves are not going automatically from user to machine for the cert search depending on the prelogon and logon state. This will sometimes leave the client in a disconnected state at logon because the registry key is still set to machine. PaloAlto should get this fixed because it has us searching for alternatives since we are on all on Passwordless authentication options like Passkey, Certificate, and Windows Hello for Business now.
- 16626 Views
- 14 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions
- GlobalProtect Gateway on PA-820 Stopped Responding – Guidance Needed in GlobalProtect Discussions
- GlobalProtect: How to combine both Machine Certificate and User Certificate Check in GlobalProtect Discussions
- VPN client failing with - Gateway DEV-VPN: Could not connect to gateway. The device or feature requires a GlobalProtect subscription license. in GlobalProtect Discussions