- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
TCP-RST-from-CLIENT
- LIVEcommunity
- Discussions
- Network Security
- Next-Generation Firewall Discussions
- TCP-RST-from-CLIENT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
TCP-RST-from-CLIENT
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2023 12:41 AM
Hi Friends,
We have a requirement we have cloud server Oracle cloud
When ever user from LAN tries to access the resources over the cloud user is able to login but unable to access any resources.
While checking in logs it is showing tcp-rst-from-client.
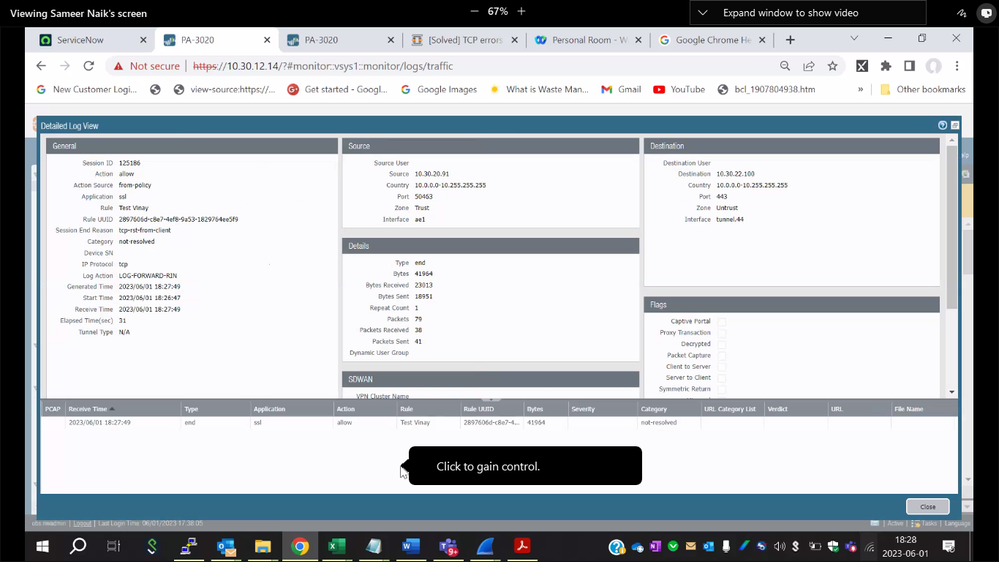
I am attaching the screenshot and session flow for reference.
I am also attaching the wire shark screenshot for reference.
I have tried by changing the tcp settings
Asymmetric Path to bypass.
Session Flow.
Session 125186
c2s flow:
source: 10.30.20.91 [Trust]
dst: 10.30.22.100
proto: 6
sport: 50463 dport: 443
state: INIT type: FLOW
src user: unknown
dst user: unknown
qos node: tunnel.44, qos member N/A Qid 0
s2c flow:
source: 10.30.22.100 [Untrust]
dst: 10.30.20.91
proto: 6
sport: 443 dport: 50463
state: INIT type: FLOW
src user: unknown
dst user: unknown
qos node: ae1, qos member N/A Qid 0
start time : Thu Jun 1 18:26:47 2023
timeout : 30 sec
total byte count(c2s) : 18951
total byte count(s2c) : 23013
layer7 packet count(c2s) : 41
layer7 packet count(s2c) : 38
vsys : vsys1
application : ssl
rule : Test Vinay
service timeout override(index) : False
session to be logged at end : True
session in session ager : False
session updated by HA peer : False
layer7 processing : completed
URL filtering enabled : True
URL category : not-resolved
session via syn-cookies : False
session terminated on host : False
session traverses tunnel : True
session terminate tunnel : False
captive portal session : False
ingress interface : ae1
egress interface : tunnel.44
session QoS rule : N/A (class 4)
tracker stage firewall : TCP RST - client
tracker stage l7proc : ctd decoder done
end-reason : tcp-rst-from-client
Can you help me what might be the resolution for this.
Regards,
Satya Kalyan.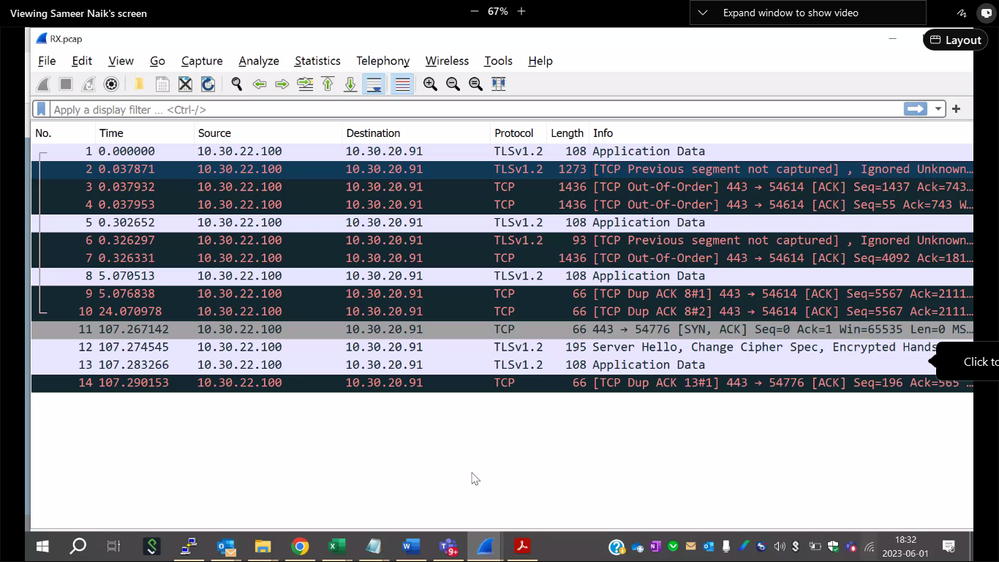
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2023 12:59 AM
@Satyak - few points to note here
1) Assuming that your connectivity from On-Prem to Cloud is via IPSec & do you have firewall rules allowed from the firewall on cloud to the Onprem Subnets?
2)Is it only the few users or all the users facing the problem?
3) Try to induce a catch all policy to for further troubleshooting
Lets wait for more senior members to comment as well
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-02-2023 03:26 AM
Yes ipsec tunnel is created and rule is also created.
everyone from LAN is effected
- 5633 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!