- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Cannot push IKE gateway X variable using template (chicken or the egg)
- LIVEcommunity
- Discussions
- Network Security
- Panorama Discussions
- Re: Cannot push IKE gateway X variable using template (chicken or the egg)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2023 01:43 PM
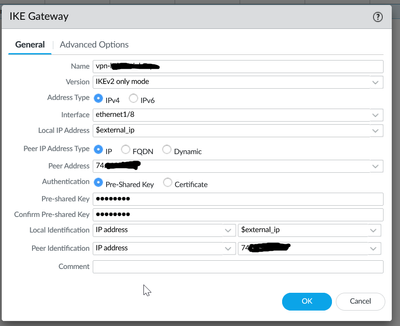
I have run into another 'bug' in 11.0.2 where my Palo Alto (PA-440) is trying to apply a configuration in an impossible order. Or, more likely, this is a Panorama bug of some sort.
Screenshot of gateway configuration:
Error message from the attempted push from Panorama:
- network -> ike -> gateway -> vpn-xxx-> local-address -> ip '74.xxx.xxx.xxx' is not a valid reference
- network -> ike -> gateway -> vpn-xxx -> local-address -> ip is invalid
The error is followed by a SLEW of other errors occurring in sort of a domino fashion.
The problem appears to be that this is a first time push to this device and the IP is invalid to be used for an IKE gateway, because it is not yet assigned to the interface of the PA-440. I opened a support case (02665364) and spent a few hours with support on the issue. But the best advice that they had was to remove the portion of the configuration that is causing the issue. I deleted the IP-Sec tunnel, and the IKE gateway. Then pushed the changes, and got success (verified that the public IP was applied to ethernet1/8 using the X variable . Then I created the IKE gateway with the same settings, and pushed the changes, and also got success. But ... this doesn't help me when I have 10 more devices that I need to configure, and I want to be able to push a VPN tunnel using Panorama and templates.
This appears to be a bug to me, so I am hoping that this gets picked up by engineering, etc?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2023 12:58 PM
Actually, doing two templates in a stack actually worked on a new device!
I have two templates in a template stack. The first template is 99 percent of the firewall configuration, which includes the interface and a variable that is assigning that interfaces IPv4 address. Then the second template in the stack applies only the VPN configuration.
There is some redundancy, as *both* templates use the same X variables, which are filled with dummy values (on both templates). Then I am overriding those variables with the actual properties on the device level (Managed Devices > Summary > Variables / Edit) which include that external interfaces public IP address.
The only other caveat is when I pushed the configuration to the device for the first time I had to use this combination of settings in Panorama:
- Merge with device candidate config - Un-Checked
- Include device and network templates - Checked
- Force template values - Checked
I will send a note to the case to check this thread, as this seems like a viable solution to this "chicken or the egg" issue. 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-15-2023 08:30 PM
Hello SteveBallantyne,
Have you tried to update the value of the variable?
I think you should put the netmask with the address.
For reference, when you use a variable, you can try to set the value normally and you will see it is populated with /xx.
If the netmask is missing, the firewall will take the value as an address object (I guess) and raise the alert you have.
--> to me seems to be working as expected.
(also in the case note, it seems the interface is not configured completely as well - no ip set on x/x interface.)
Olivier
PCSNE - CISSP
Best Effort contributor
Check out our PANCast Channel
Disclaimer : All messages are my personal ones and do not represent my company's view in any way.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2023 05:19 AM
Hello Oliver,
Thank you for the feedback - and these are good thoughts! I actually had tried adding the netmask to the IP. It accepted the value when it was used for the IPv4 address attached to the 1/8 interface - but it rejected that value when used for the IKE gateway.
It seems like the PA-440 is fine with the variable and the way that I used it. But I can't have it defined in an IKE gateway because for some reason it tries to apply that part first. And since it's a first time push, there was a lot that went with that template being applied (such as zones, certificates, etc).
I don't imagine that many people have this problem because it implies that you have at least two or more sites, with nearly the same VPN tunnel at each site. But we have a traditional hub and spoke site, and all of the satellite need the same access. And man, would this make my life easier if I could get this to work. 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2023 05:45 AM - edited 08-16-2023 06:01 AM
Here is a random thought ...
I am still new to Panorama and templates. I know that I have device groups, templates, and then template *stacks*. Would there be a way that I could trick the PA-440 into applying the changes in the correct order? In other words - one template to apply the external interface IP address - and then another template lower in the stacking order to apply the IKE policy?
EDIT: I may be onto something as it looks like there is a "move up" and "move down" option on templates, which suggests that these would be applied in a specific order!
I am going to work on configuring this and applying it to a new out-of-the-box PA-440.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2023 06:02 AM
Hi @SteveBallantyne ,
That is a very interesting idea! I would love to know if it works. Sometimes I have commit failures based upon the order of Panorama commits, and I have learned to work around them.
With regard to your issue, I don't see a problem with 2 pushes from Panorama - one for the interface, and then one for the IPsec. That's a lot better than configuring the 10 NGFWs individually. Thoughts?
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2023 06:48 AM
Hello all,
I can try tomorrow in testbed to see the IKE gateway with the variable set to IP/netmask.
Regarding the order of the template in the stack, I would think the order will only change the actual value pushed to the firewall (template inheritance order), you are not pushing template 1 then template 2 and so on and so on (imagine you're pushing x different templates on a PA-220 ... endless commit).
If you need to set up hub and spoke : sdwan plugin? 🙂
Olivier
PCSNE - CISSP
Best Effort contributor
Check out our PANCast Channel
Disclaimer : All messages are my personal ones and do not represent my company's view in any way.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2023 12:58 PM
Actually, doing two templates in a stack actually worked on a new device!
I have two templates in a template stack. The first template is 99 percent of the firewall configuration, which includes the interface and a variable that is assigning that interfaces IPv4 address. Then the second template in the stack applies only the VPN configuration.
There is some redundancy, as *both* templates use the same X variables, which are filled with dummy values (on both templates). Then I am overriding those variables with the actual properties on the device level (Managed Devices > Summary > Variables / Edit) which include that external interfaces public IP address.
The only other caveat is when I pushed the configuration to the device for the first time I had to use this combination of settings in Panorama:
- Merge with device candidate config - Un-Checked
- Include device and network templates - Checked
- Force template values - Checked
I will send a note to the case to check this thread, as this seems like a viable solution to this "chicken or the egg" issue. 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2023 01:45 PM
Hi @SteveBallantyne ,
That is good news! The 1st template is the one on top of the stack?
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2023 02:16 PM
You got it, Tom! And so long as I wasn't trying to use the default to "smash" the templates together before-hand, the PA-440 seemed to do just fine with applying one template in-full before moving onto the next.
Support is going to work on a KB for this. 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-16-2023 06:17 PM
Hello SteveBallantyne,
Good to hear it works (so there is no bug :D)
Regarding the KB, I don't have the full picture of the case so I will not comment further.
Just for information, you can check this PANCast Episode about the Templates and Template Stacks
Olivier
PCSNE - CISSP
Best Effort contributor
Check out our PANCast Channel
Disclaimer : All messages are my personal ones and do not represent my company's view in any way.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-03-2024 12:19 PM
I have the same issue with config push. really helpful. I have 6 templets moving up or down dont change anything fyi.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-03-2024 12:27 PM
Hello Leightonlee, which setting is the Palo Alto getting hung up on? Best bet for a solution is to create a new template that includes only that setting and then rearrange it so that your new template is on the top of the stack (if possible).
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-04-2024 07:55 AM
Warnings:
Duplicate certificate subject found:
Details:Validation Error:
network -> ike -> gateway
I opened a case if the new device is in the device group and the templates as well both interface config and all why this keep happening?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2024 03:08 PM
I am also running into this issue right this moment. Much like SteveBallantyne's original post, I have a hub-spoke topology where all satellite offices use the same VPN configuration to phone home. I am getting "network -> ike -> gateway -> Primary-1 -> local-address -> ip 'x.x.x.x' is not a valid reference" no matter what shape or form I build the IP Variable with. I have two templates in my stack, the first configures everything L1, VPN, and Routing, the second configures services (AAA, DNS, NTP, etc) that will phone home across the VPN. Following the guidance in this thread did not change my results in any observable way. If I create the IKE Gateway locally on the Firewall with all the same settings, it accepts just fine.
To my knowledge, the position of the Templates in the Stack only apply to conflict resolution between the templates.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-07-2024 03:55 PM
Hi @kylebrolafski ,
I think the issue was that the VPN config was committed before the template variable, and therefore did not exist yet. @SteveBallantyne moved the VPN config to a template lower in the stack which appears to have forced the interface and template variable to commit 1st. He also recommends other commit options in the solution.
Thanks,
Tom
- 1 accepted solution
- 10861 Views
- 16 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Transferring the config from defective PA850 to new PA 850 in Next-Generation Firewall Discussions
- Cannot push IKE gateway X variable using template (chicken or the egg) in Panorama Discussions
- Can a firewall hostname be setup as a variable in a Template? in Panorama Discussions
- Public PKI CA with SCEP support in GlobalProtect Discussions
- Template Variables for Global Protect in Panorama Discussions