- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Reference Design : Prisma Access and Prisma SD-WAN (DC) using Service Connection
- LIVEcommunity
- Products
- Secure Access Service Edge
- Prisma SD-WAN
- Prisma SD-WAN Articles
- Reference Design : Prisma Access and Prisma SD-WAN (DC) using Service Connection
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
on 08-16-2024 04:00 PM
1. Introduction
1.1 Purpose
The purpose of this whitepaper is to provide a comprehensive reference design for integrating Prisma Access with Prisma SD-WAN (Data Center) using Service Connection. This document aims to guide network architects, engineers, and IT professionals through the recommended design and various traffic flow scenarios to optimize network performance, security, and scalability.
1.2 Scope
This whitepaper covers the following aspects of the reference design:
- Overview of Technologies: An introduction to Service Connection, highlighting their key features and benefits.
- Design Considerations: Critical factors to consider when designing the network, including business and technical requirements.
- Recommended Design: Detailed network architecture illustrated with diagrams and explanations.
- Traffic Flow Scenarios: Analysis of different traffic flow scenarios.
The document is intended for organizations looking to leverage the combined capabilities of Prisma Access and Prisma SD-WAN to build a robust and scalable network. It is not intended to cover all possible configurations or deployment scenarios but focuses on the most common and recommended practices.
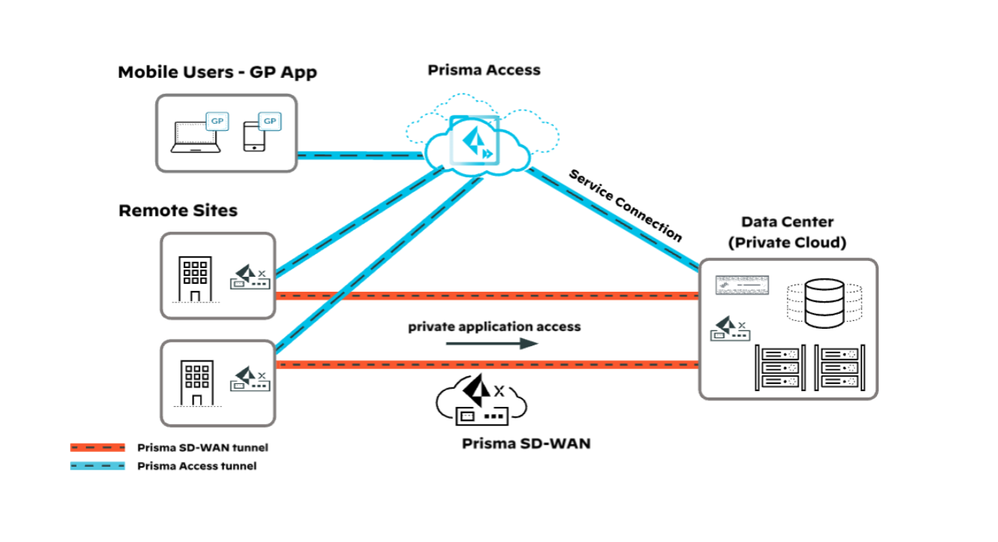
2. Overview of Service Connection
Service connections provide secure access from Prisma Access to internal applications and services. The service-connection options in this section begin with an initial attachment to Prisma Access from an on-premises facility using a single IPSec tunnel, or pair of tunnels, for resilience. For larger, more complex environments, the designs progress into multiple service connections for increased resilience and/or optimized routing to on-premises applications or services. Although the examples in this section refer to on-premises data centers, the applications or services could be cloud-hosted with dedicated access into your Prisma Access network via a service connection. The service-connection termination point can be a Palo Alto Networks NGFW or any IPSec capable firewall, router, or SDWAN endpoint. When terminating the tunnel on a non-Palo Alto Networks device, ensure that the remote IPSec endpoint has support for more recent encryption and authentication in order to ensure secure transport.
3. Design Considerations
When planning your network integration with Prisma Access and Prisma SD-WAN, consider the following key factors:
- Number of Connections: Determine how many connections to your data centers you need.
- Single Connection: If you have one connection to HQ or a data center, decide if you need a backup connection to Prisma Access.
- Multiple Connections: If you have multiple service connections, ensure your internal network peering points to Prisma Access are also connected for redundancy.
- Service Connection Configuration: For multiple service connections, decide if your network will peer with Prisma Access as a single autonomous system (AS) or multiple autonomous systems.
These considerations will help you design a network that is redundant, scalable, and optimized for performance with Prisma Access and Prisma SD-WAN.
4. Recommended Design
In this section, we outline the recommended design for integrating Prisma Access with Prisma SD-WAN, emphasizing security, traffic symmetry, and simplicity in managing user identity information.
4.1. Network Architecture
To ensure a secure and efficient network design, we recommend deploying Palo Alto Networks' Next-Generation Firewall (NGFW) at the data center. The key components of this design include:
- Service Connection Termination: The service connection from Prisma Access should terminate on the NGFW at the data center. This setup provides enhanced security by leveraging the advanced threat prevention capabilities of the NGFW.
- Traffic Symmetry: Terminating the service connection on the NGFW ensures symmetrical traffic flow, which is crucial for maintaining consistent security policies and monitoring across the network.
- Simplified User-ID Management: Distributing User-ID information from Prisma Access to the NGFW is streamlined in this setup. This integration allows for seamless user identity management and policy enforcement, enhancing overall network security and efficiency.
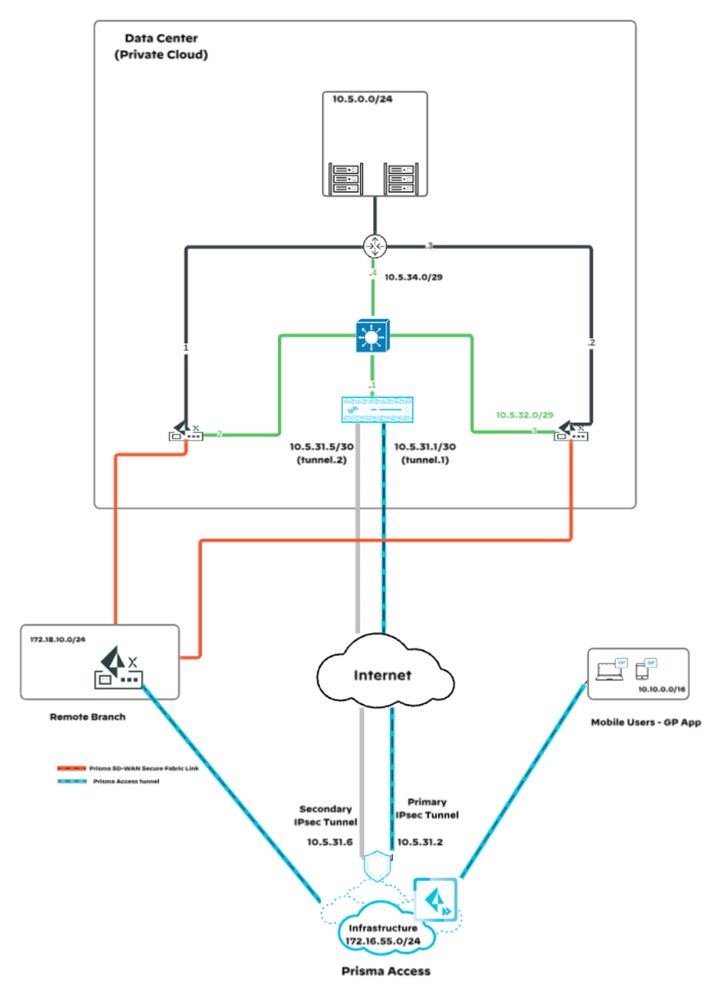
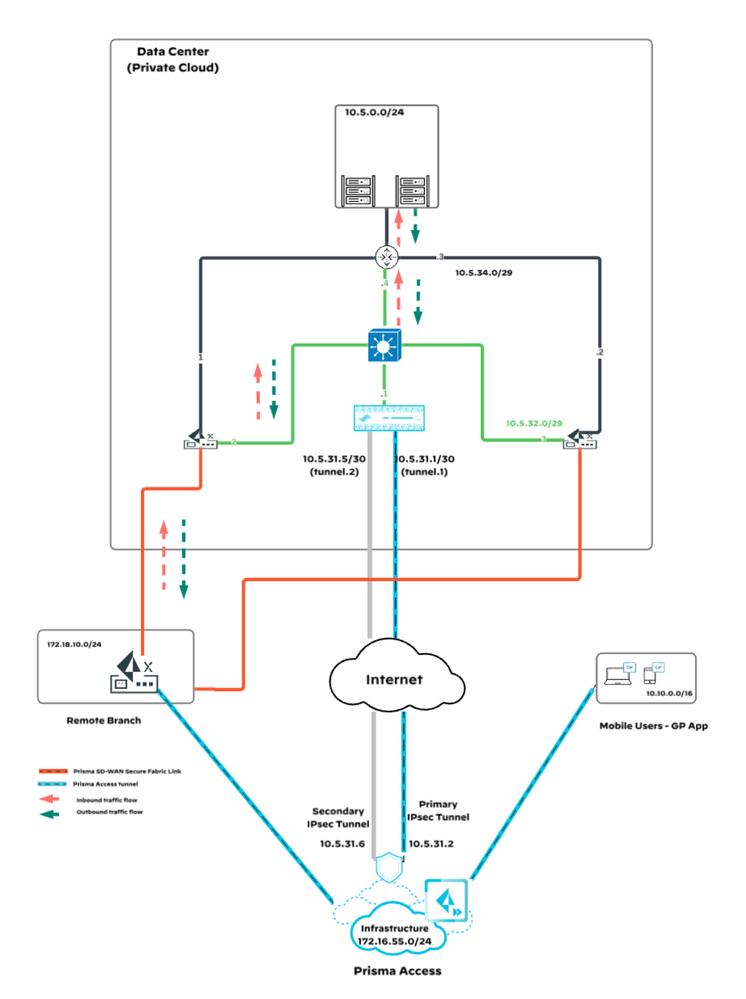
The recommended design includes the following components and connections as depicted in the reference network diagram:
Next-Generation Firewall (NGFW): Positioned in the data centers, serving as the termination point for the service connection from Prisma Access. In addition, the NGFW can also be used to manage the Demilitarized Zone (DMZ), providing an additional layer of security for applications that require controlled exposure to the internet. Furthermore, the NGFW can be used to handle egress traffic from the data center to the internet, ensuring that outbound traffic is inspected and secured before leaving the network.
Prisma SD-WAN IONs: Two ION devices in each data center to handle SD-WAN functionality.
Core Router: The central router within the data center for core network routing.
The network diagram shows the detailed configuration and connectivity among the components:
- The service connection from Prisma Access terminates on the NGFW in the data center.
- The NGFW is connected to both Prisma SD-WAN IONs using Edge BGP peer configuration. This peer type allows the data-center ION to learn IP prefixes from the NGFW and split the prefixes if needed (if we are learning same prefixes from remote branches) when advertising back to the Core Router.
- The NGFW is also connected to the Core Router using Classic BGP peer configuration. This setup enables the NGFW to exchange routes with the Core Router, ensuring optimal routing and traffic management within the data center.
- Each ION device is connected to the Core Router using Core Peer configuration. This configuration enables the automatic generation of route-maps by the Cloud Manager to control route advertisement and learning.
5. Traffic Flow Scenarios
The following scenarios illustrate how traffic flows in the recommended network design, emphasizing the roles of Prisma Access, NGFW, and Prisma SD-WAN IONs.
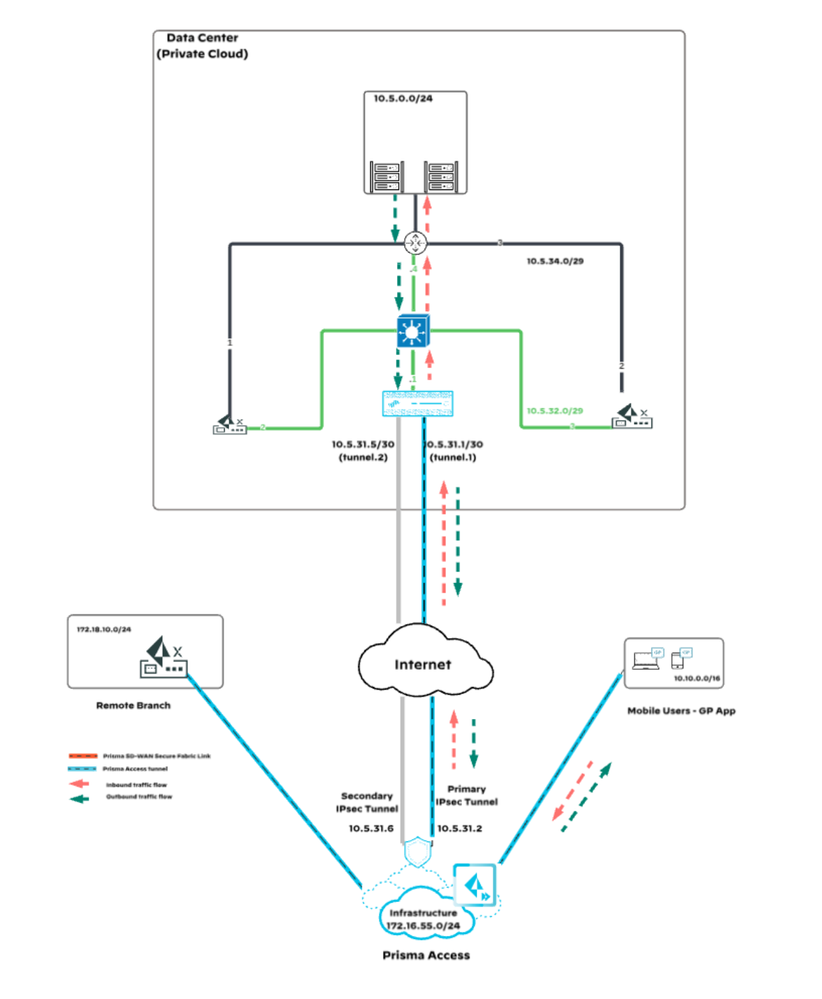
5.1 Mobile User Accessing Private Application in Data Center
5.1.1 Inbound Traffic:
- A mobile user attempts to access a private application hosted in the data center.
- The traffic is routed through Prisma Access and reaches the data center via the service connection.
- The service connection terminates at the NGFW.
- The NGFW, which has learned the routes directly from the Core Router, forwards the traffic to the Core Router.
- The Core Router sends the traffic to the destined application.
5.1.2 Return Traffic:
- The return traffic from the application is sent back to the Core Router.
- The Core Router forwards the return traffic to the NGFW.
- The NGFW sends the traffic back to Prisma Access over the service connection.
- Finally, Prisma Access routes the return traffic back to the mobile user.
Note: There is no need for mobile user traffic to traverse the ION devices in the data center.
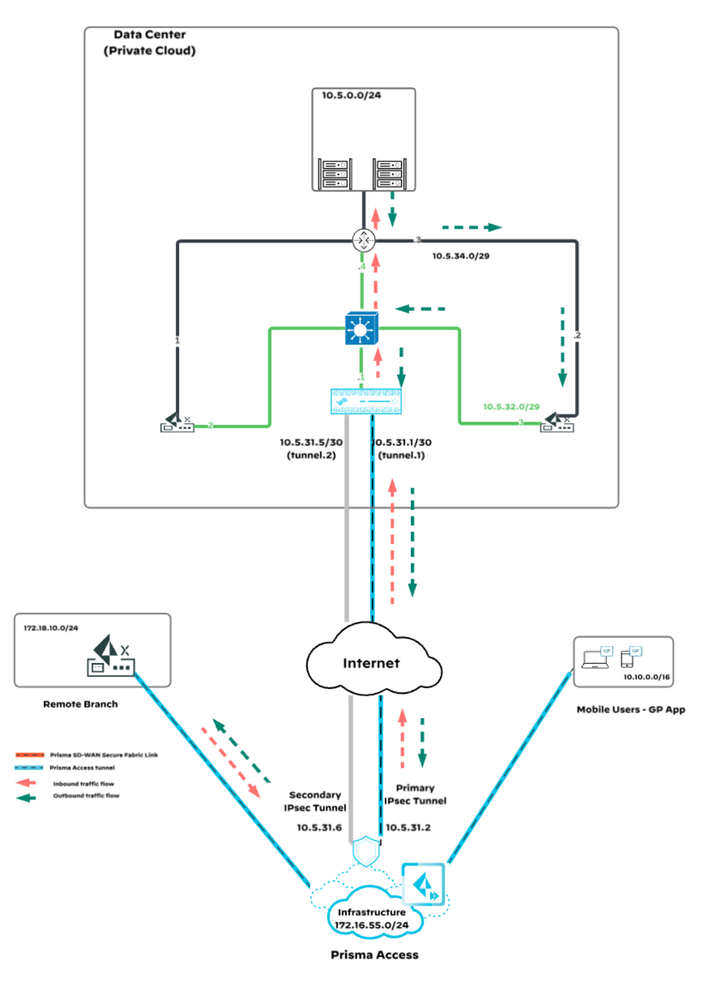
5.2 Remote Branch User Accessing Private Application in Data Center via Prisma Access
5.2.1 Inbound Traffic:
- A remote branch user attempts to access a private application in the data center.
- Depending on the policy configuration at the remote branch, the traffic is routed through Prisma Access via the Prisma Access tunnel from the branch.
- The traffic reaches the data center's NGFW via the service connection.
- The NGFW, having learned the routes directly from the Core Router, forwards the traffic to the Core Router.
- The Core Router sends the traffic to the destined application.
5.2.2 Return Traffic:
- The return traffic from the application is sent back to the Core Router.
- Since the source is the branch prefix and DC ION is learning the same prefix from the NGFW, when the ION advertised to the Core Router, it split the prefixes (e.g., 172.18.10.0/24 is advertised as 172.18.10.0/25 and 172.18.10.128/25).
- The Core Router prefers the ION device over the NGFW for return traffic based on the advertised prefixes.
- The return traffic reaches the ION device. The ION device sends the return traffic to the NGFW.
- The NGFW forwards the traffic back to Prisma Access over the service connection.
- Prisma Access routes the return traffic back to the remote branch over the Prisma Access tunnel.
5.3 Remote Branch User Accessing Private Application in Data Center over Secure Fabric Tunnels
5.3.1 Inbound Traffic:
- A remote branch user attempts to access a private application in the data center directly (depending on policy configuration) over secure fabric tunnels.
- The traffic is received by the ION device in the data center.
- The ION device sends the traffic to the Core Router.
- The Core Router forwards the traffic to the destined application.
5.3.2 Return Traffic:
- The return traffic from the application is sent back to the Core Router.
- The Core Router forwards the return traffic to the ION device (as explained previously)
- The ION device in the data center sends the traffic back to the remote site over the secure fabric tunnel because when we receive the inbound flow, the session was recorded and we follow the same path for the outbound flow for the existing session.
These traffic flow scenarios illustrate the seamless integration between Prisma Access, NGFW, and Prisma SD-WAN IONs, ensuring optimized routing, security, and performance across the network.
Hey There,
Thanks for sharing this design.
Will be great if you help to understand below questions.
1/-- Is this personal write-up or its Paloalto Official Design document ?
2/-- If our requirement is solely to provide MU access to the Private Application in the DC and RN access to the Private Application in the DC, then ION devices are not necessary.
3/-- In addition, in second requirement if MU and RN access internet then we can apply security profiles (URL Filtering, Threat Prevention, etc.) in Prisma Access Cloud ?
Thanks.
- This is official Palo Document
- You don't have to have ION in the DC at all if you don't want, just depends on your use cases....but most customers that have ION at Branch are going to have ION at DC also.
- Yes, whatever traffic you send to Prisma Access will be inspected whether that is for public or private app access.
5.2.2 Return Traffic:
- The return traffic reaches the ION device. The ION device sends the return traffic to the NGFW
why the DC ION send the return traffic to the NGFW as its also learned the prefix from SDWAN? Because it doesn't have an existing session recorded? Thanks!
- 10939 Views
- 3 comments
- 2 Likes