- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Finding a rogue IP in Prisma SD-WAN
- LIVEcommunity
- Discussions
- Secure Access Service Edge
- Prisma SD-WAN Discussions
- Finding a rogue IP in Prisma SD-WAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Finding a rogue IP in Prisma SD-WAN
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2022 09:43 AM
Greetings.
Looks like someone misconfigured a global/local slider and we're receiving a /32 IP address in the BGP route table from the Data Center IONs. I'd like to identify the offending site quickly - is there an easy way to locate an IP by site using the portal?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-08-2022 02:38 PM
Thank you for the post @TKlausen2
maybe there is a better way to do it, but on top of my head I can think of below options:
Advertising router ID / AS number
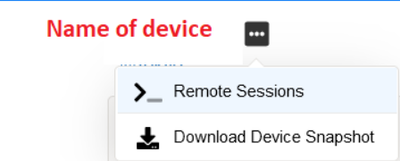
Login to SD-WAN portal, then navigate to: Maps > Claimed Devices, then click on any appliance, then a new page will open:
After you click on remote session, a new page will open where you can login from CLI. Authenticate with elem-admin, then issue: "dump routing route prefix=X.X.X.X/32" where X.X.X.X is the prefix you are tracking down. Reference is here: https://docs.paloaltonetworks.com/prisma/prisma-sd-wan/prisma-sd-wan-ion-cli-reference/use-cli-comma...
In this output, you will see the router ID as well as AS of the device that advertised that prefix:
If you know to what router/site that router ID / AS number belongs, then you go to that site and fix it. If you do not know that information, you can still find it from SD-WAN portal from: Manage > Setup > Devices > Claimed > Select a device > Routing > BGP/Peers > BGP Global Config for ION device. If you have hundreds of devices, this might however be a time consuming and equals to searching that slider misconfiguration manually device by device.
Audit Log
An alternative way might be to search in audit log to track down recent changes. Reference: https://docs.paloaltonetworks.com/prisma/prisma-sd-wan/prisma-sd-wan-admin/prisma-sd-wan-administrat...
Kind Regards
Pavel
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-13-2022 11:32 PM
From the DC device try the below commands
#dump prefix reachability prefix=x.x.x.x/32
this will give you path id from which its learning the prefixes and then try
#inspect fib vpn pathid=zzzzzzzzzz
the above command will give you the site name. |
- 3067 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Triage process to eliminate endpoint issues prior to Prisma Access queries in Prisma Access for MSPs and Distributed Enterprises Discussions
- On-Boarding of Cisco SDWAN to Prisma in Prisma Access Discussions
- In prisma sdwan unable to enable l3 forwarding in Prisma SD-WAN Discussions
- Prisma SDWAN ION monitoring in Prisma SD-WAN Discussions
- Prisma SDWAN Evaluation License in Prisma SD-WAN Discussions