- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
custom snort signature add the pattern if the context operator is not found
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- custom snort signature add the pattern if the context operator is not found
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2020 12:17 AM
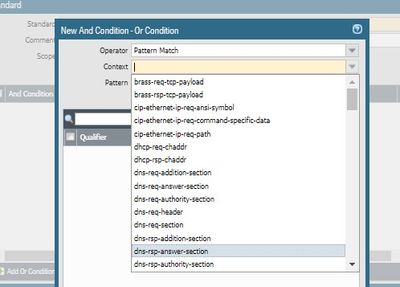
creating a custom snort signature on Palo alto Firewall but didn’t found the concern context operator for match pattern.
Shall we create a context operator or how it can add the pattern if the context operator is not available?
For example:
alert tcp $HOME_NET any -> $EXTERNAL_NET 443 (msg:"[CIS] Emotet C2 Traffic Using Form Data to Send Passwords"; content:"POST"; http_method; content:"Content-Type|3a 20|multipart/form-data|3b 20|boundary="; http_header; fast_pattern; content:"Content-Disposition|3a 20|form-data|3b 20|name=|22|"; http_client_body; content:!"------WebKitFormBoundary"; http_client_body; content:!"Cookie|3a|"; pcre:"/:?(chrome|firefox|safari|opera|ie|edge) passwords/i"; reference:url,cofense.com/flash-bulletin-emotet-epoch-1-changes-c2-communication/; sid:1; rev:2;)
Not available
http_method
http_client_body
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-21-2020 08:19 PM - edited 10-26-2020 01:25 AM
@OtakarKlier wrote:Hello, 8 ball pool
Writing custom signatures is something I always leave to the vendors, its their job :). If you setup your PAN with the everything turned on, anti-virus, spyware, url filtering, dns sinkhole, using secure dns (even if it snot PAN's), SSL Decrypt, wildfire, tight policies, I think you will find not much if anything can get through. Also enable the telemetry to be sent to PAN, it helps hem write signatures for everyone :), a small way to give back.
Also use best practices on the rest of the network as well as endpoints (AV etc).
You can always use their threat db to search and see if they already have something. If they dont put in a TAC request and they'll work on one.
https://threatvault.paloaltonetworks.com/
Regards,
Thank you very much!! Very useful advice
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-07-2020 02:42 PM
Hello,
Writing custom signatures is something I always leave to the vendors, its their job :). If you setup your PAN with the everything turned on, anti-virus, spyware, url filtering, dns sinkhole, using secure dns (even if it snot PAN's), SSL Decrypt, wildfire, tight policies, I think you will find not much if anything can get through. Also enable the telemetry to be sent to PAN, it helps hem write signatures for everyone :), a small way to give back.
Also use best practices on the rest of the network as well as endpoints (AV etc).
You can always use their threat db to search and see if they already have something. If they dont put in a TAC request and they'll work on one.
https://threatvault.paloaltonetworks.com/
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-21-2020 08:19 PM - edited 10-26-2020 01:25 AM
@OtakarKlier wrote:Hello, 8 ball pool
Writing custom signatures is something I always leave to the vendors, its their job :). If you setup your PAN with the everything turned on, anti-virus, spyware, url filtering, dns sinkhole, using secure dns (even if it snot PAN's), SSL Decrypt, wildfire, tight policies, I think you will find not much if anything can get through. Also enable the telemetry to be sent to PAN, it helps hem write signatures for everyone :), a small way to give back.
Also use best practices on the rest of the network as well as endpoints (AV etc).
You can always use their threat db to search and see if they already have something. If they dont put in a TAC request and they'll work on one.
https://threatvault.paloaltonetworks.com/
Regards,
Thank you very much!! Very useful advice
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-18-2021 05:25 AM
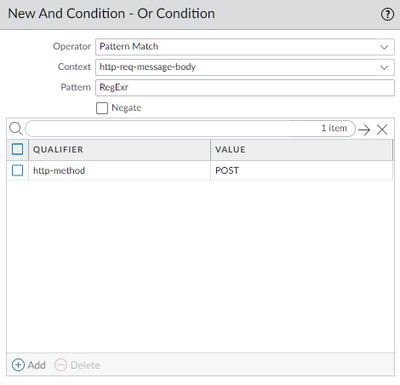
Hi @Mohammed_Yasin,
http_method in the Custom Vulnerability Object is the http-method Qualifier and the http_client_body is the http-req-message-body Context, i.e.,:
Albert
- 1 accepted solution
- 4485 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!