- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
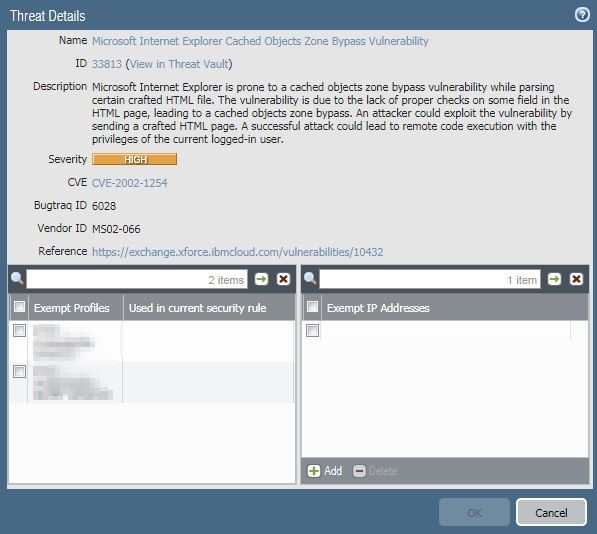
Exempt domain name instead of exempt ip address for vulnerability
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Exempt domain name instead of exempt ip address for vulnerability
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Exempt domain name instead of exempt ip address for vulnerability
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2019 01:03 PM - edited 01-09-2019 01:04 PM
Hello,
We get large amount of high severity threat alarm when users visit Yahoo, they were triggered by this url s.yimg.com/aaq/yc/js/tdv2-applet-canvass.8739955d2bd825cb0aa2.min.js ( 8739955d2bd825cb0aa2 is a random string that changes everytime ). I would like to setup an exception for s.yimg.com, but its ip always changes too and you can only exclude static ip address. What would be the best way to fix this?
TIA
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2019 03:28 PM
Hello,
Yes, it requires a seperate policy above the one that is blocking this. Also requires you to create a new vulnerabiolity profile and 'exempt' this vulnerability. Then in your policy you just make sure to assign the vulnerability profile with the exempting and the URL as a catagory.
Hope that helps.
- 4149 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Upgrade from Basic Threat Prevention to Advanced Threat Prevention in Advanced Threat Prevention Discussions
- We are trying to allow particular website to particular user but the same is not occuring in Advanced URL Filtering Discussions
- reduce exposure to PAN-OS vulnerabilities like CVE-2025-0111 in Advanced Threat Prevention Discussions
- mitigate risks from vulnerabilities in Advanced Threat Prevention Discussions