- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Enhanced Security Measures in Place: To ensure a safer experience, we’ve implemented additional, temporary security measures for all users.
Unlock your full community experience!
Meltdown and Spectre Vulnerability
- LIVEcommunity
- Discussions
- Cloud Delivered Security Services
- Threat & Vulnerability
- Re: Meltdown and Spectre Vulnerability
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Meltdown and Spectre Vulnerability
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-04-2018 09:01 AM
Are PA devices effected by the meltdown and spectre vulnerability and if so, are these signatures known yet by PA?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-04-2018 02:31 PM
Please note we have posted the following advisories regarding Meltdown and Spectre.
https://researchcenter.paloaltonetworks.com/2018/01/threat-brief-meltdown-spectre-vulnerabilities/
Please also note that these are vulnerabilities which require local code execution therefore coverage in the form of IPS (vulnerability protection) signatures are not germane to these particular vulnerabilities as these are not network-borne attacks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-04-2018 04:32 PM
Hi,
Is the vulnerability applicable only to the hardware platform or if the Virtual firewall series are also affected?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2018 03:29 AM
The new 762 update sent out last night was applied to our PA500 and "broke" it.
We had lots of resources-unavailable session end reasons.
We had to revert and restart the dataplane.
Has anyone else had these issues?
-Ronelle
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2018 08:21 AM
@bvandivier wrote:
Please also note that these are vulnerabilities which require local code execution therefore coverage in the form of IPS (vulnerability protection) signatures are not germane to these particular vulnerabilities as these are not network-borne attacks.
I believe PA's response is accurate for packet level devices, but what about products like an On-Premise Wildfire sandbox. I assume Wildfire is some form of a hypervisor product that is intentionally executing files on intentionally flawed OSes. Is this not "local code execution"? Are there any specific statements for the Wildfire product?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2018 08:31 AM
Any specific statements regarding Wildfire or other products as they relate to meltdown/spectre will be shared in future updates to the official advisory.
https://researchcenter.paloaltonetworks.com/2018/01/threat-brief-meltdown-spectre-vulnerabilities/
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2018 09:51 AM
@Ronelle wrote:The new 762 update sent out last night was applied to our PA500 and "broke" it.
We had lots of resources-unavailable session end reasons.
We had to revert and restart the dataplane.
Has anyone else had these issues?
-Ronelle
We have 5 with no issues (well 4 - 1 is an A/P pair).
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-05-2018 02:09 PM
Singature just released: "Name: Multiple CPUs Side-Channel Information Disclosure Vulnerability, Unique Threat ID: 30276"
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-08-2018 11:02 AM
Is there a test site where we can see what the endpoints will look like when the palo triggers a drop?
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-23-2018 01:16 PM
default action = alert. surprising.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-24-2018 12:54 AM
Default Palo Action on any new threat = Alert
...as far as I can tell. I have always presumed it is deliberate, but I don't know how long they leave it before they feel confident enough to block. We have spotted some very mature Critical or High threats which are still only "alert" as default action.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2018 03:35 PM
Hello,
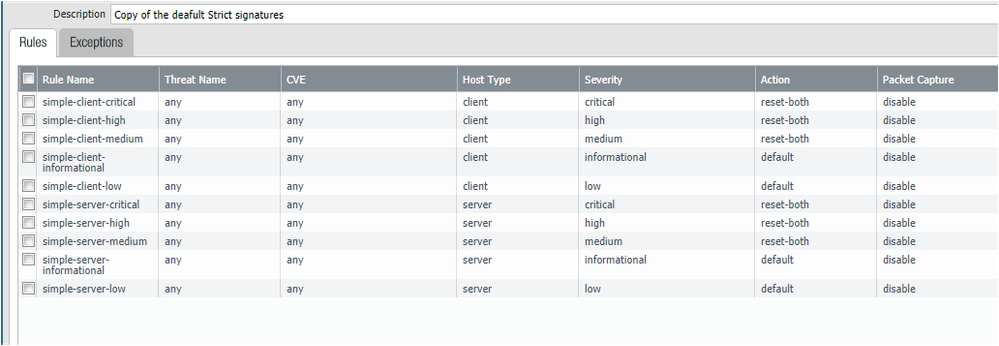
The defaults are set to alert as a safety measure. WHat we do is copy the default Vulnerability policies and manuall set the action based on severity. I.e. anything medium and higher is blocked or reset, etc. This way when new signatures come out, they may be classified as high or critical, but our policies are set so that they will be blocked in some fashion.
Hope that makes sense.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-25-2018 04:16 PM
So you override the default actions for those severities? I have that configuration in place in some places, but the way the default actions as described to my be an SE from Palo Alto which got me thinking about that approach. He said something to the effect that default action is evaluated very differently than severity. They are basically set based on confidence that there will be no false positives.
Another example he gave was the Poodle signature which simply detected any SSLv3 - which you certainly wouldn't want to block, particularly at that time. Granted that was an informational signature, not medium or higher, but you can look at Vulnerability Protection signatures '( severity contains 'critical' ) and ( action contains 'alert' )' and see 1704 signatures (over 1/10th) where the default action is alert (and one that is allow.)
Do you even alert below medium? All I have investigated in those severities have ended up on our whitelist so far.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2018 01:17 AM
We do drop/reset Critical and High because we have seen serious vulnerabilities being ignored because they are alert only, but we had worked out that the PAN approach was more based on confidence. That makes lots of sense, but only if the action changes after a few days or so when they have worked out how reliable the detection is. We have found that they stay on alert for months which just gives too large a window for attack.
We do alert everything but our logs are huge! It's a good point maybe we don't need to, we just tend to log as much as possible so we can see what is going on.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-26-2018 01:00 PM
Hello @chyates,
Yes, I am actually thinking of just performing a server side reset on my external facing zones so my servers connection gets reset but the attackers does not so it keeps their session open :).
Cheers!
- 19166 Views
- 16 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!