- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Palo Alto Azure - second trust interface routing issue
- LIVEcommunity
- Discussions
- Network Security
- VM-Series in the Public Cloud
- Re: Palo Alto Azure - second trust interface routing issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2019 06:47 PM - edited 03-14-2019 07:02 PM
Hello to all,
I am doing a lab in Azure with a VM-300. I have the three interfaces - trust, management, and untrust. I have this model working to protect 2 additional subnets that have VMs, I achieved east-west and north south protection, including microsegmentation. However, I was wondering if I can add a new interface to control security policies by zones (currently I will ahve to specify the sunet address). I added a NIC on a new subnet and after reboot the PA has a third interface (trust2), and with other subnet that have VMs in in and emulated what I did with the trust interface.
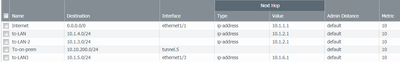
Problem is that I am seeing traffic going through the firewall, but is not returning back (no reply).. I think it might be a routing issue in Azure UDR however they seem fine to me.. See below for my Azure UDRs and PAN VR. Can someone tell me if they have achieved this configuration and possiblity where my issue is? Let me know if you need a network diagram, iI can do one
and add it. From below, I am trying RDP connection from LAN2 to LAN3 subnet:
10.1.2.4 - trust interface ip on Palo Alto VM
10.1.6.4 - trust2 interface ip on Palo Alto VM
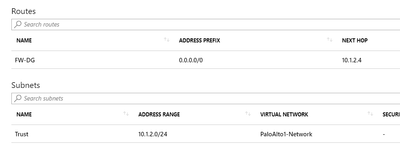
Azure trust subnet (FW trust interface):
Azure LAN subnet (first subnet to be protected by trust):
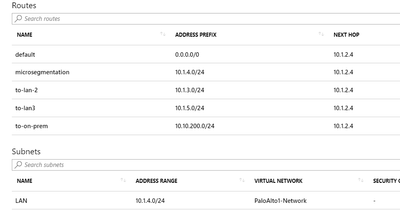
Azure LAN2 subnet (second subnet to be protected by trust):
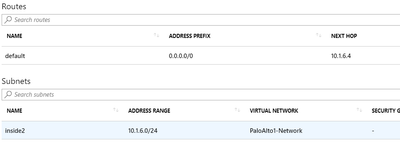
Trust2 subnet (FW trust2 interface):
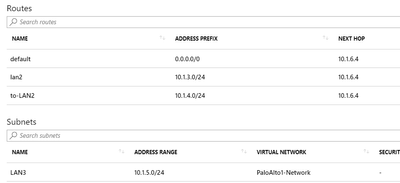
Azure LAN3 subnet (subnet to be protected by trust 2 FW interface):
Palo Alto VR:
Log:
@reaper - (I really like your posts! 🙂 ) Please take a look.
@jdelio your posts too!
Thanks in advance!
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2019 07:18 PM
While it is possible, I would not recommend going this route.
To make it work, you need to be diligent in ensuring your UDRs point to the correct firewall IP for the bidirectional traffic. One thing that jumps out at me is that your VR is utilizing E1/3 interface for the Trust 2 routes but you do not have E1/2 specified for the Trust 1 routes.
Another common issue is that manually added Azure Interfaces typically do not have IP Forwarding Enabled in the IP config. Check this on your E1/3 and E1/2 interfaces.
With that said, this model does not hold true when you introduce the Internal LB with HA Ports for Fault Tolerance and Scalability. In order to introduce this model, a single LB Front End IP and single Interface per Firewall needs to be used for all East/West/Hybrid routes to ensure symmetric routing and persistence due to Azure's hashing algorythm. This results in Security Policies that are subnet based and not zone based.
You can use the Transit VNET template as an example.
https://github.com/PaloAltoNetworks/Azure-Transit-VNet/tree/master/Azure-Transit-VNET-1.0
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-14-2019 07:18 PM
While it is possible, I would not recommend going this route.
To make it work, you need to be diligent in ensuring your UDRs point to the correct firewall IP for the bidirectional traffic. One thing that jumps out at me is that your VR is utilizing E1/3 interface for the Trust 2 routes but you do not have E1/2 specified for the Trust 1 routes.
Another common issue is that manually added Azure Interfaces typically do not have IP Forwarding Enabled in the IP config. Check this on your E1/3 and E1/2 interfaces.
With that said, this model does not hold true when you introduce the Internal LB with HA Ports for Fault Tolerance and Scalability. In order to introduce this model, a single LB Front End IP and single Interface per Firewall needs to be used for all East/West/Hybrid routes to ensure symmetric routing and persistence due to Azure's hashing algorythm. This results in Security Policies that are subnet based and not zone based.
You can use the Transit VNET template as an example.
https://github.com/PaloAltoNetworks/Azure-Transit-VNet/tree/master/Azure-Transit-VNET-1.0
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-15-2019 08:01 AM
Hello @jmeurer,
Thank you so much for your help!! Looks like the issue was that I did not enabled IP forwarding when I created the Azure NIC for the Palo Alto second trust interface. I also added the interface name for th estatic routes on the Palo Alto VR for better reading.
Regarding the model that you are telling me, what will be the recommended arquitecture if I only have one firewall?? All models that I have found on Palo alto documentation seems to be for HA.. Also, is there a use case where I have one firewall that I will want to have load balancers and/or other Azure resource?
Is the model that you told me for HA, or it can be applied to a single firewall? Just want to know possible deployments. I only have one subnet with aroudn 20 servers that I want to protect with a single firewall.
Thanks again!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-15-2019 08:25 AM
Your model works for single firewall. My point was more so if you want to consider Fault Tolerance in the design when adding a second firewall. No need for the added complexity of the load balancers in a single firewall use case.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-15-2019 11:25 AM
Thanks for the prompt reply. I see, I will stick with the one interface approach to have the versatility to change to an HA model if needed in the future.
Thanks again!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-10-2020 03:06 AM
We are running into same issue where in palo alto VM ( NVA) is deployed in HA on azure using design mentioned below.
Looks like Palo Alto interface is not routing packet .
I checked routing is fine with azure UDR and on Palo Alto VR , issue is only when traffic hits palo alto floating IP interfaces.
Anyone faced same issue ? Basically issue we are facing with HA deployment .
- 1 accepted solution
- 15820 Views
- 5 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GloablProtect + Explicit Proxy blocks WSL traffic. in GlobalProtect Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- Conditional Advertisement / BGP Failover with Dual ISP — How to Remove ISP1 Routes on Internet Loss? in Next-Generation Firewall Discussions
- PA-440 won't talk via network in Next-Generation Firewall Discussions
- Max number of units (aeX.Y subinterfaces) supported under a single AE interface? in Next-Generation Firewall Discussions