- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Block FTP Brute Force Attemps - Threat ID 40001
- LIVEcommunity
- Discussions
- General Topics
- Block FTP Brute Force Attemps - Threat ID 40001
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-05-2012 09:49 AM
Hello,
I want to block Block FTP Brute Force Attemps.
The default rule in the PA alert only in theThreat log.
I added a new Vulnerabolity Protection Rule:
Action: Block
Host type: Any (also tried Server)
Category: brute-force
Severity: Any
CVE: Any
Vendor ID: Any
I placed the rule above al the default rules (see attachment).
If I simulate a ftp brute force attack I only see a alert message in the Threat log.
thanks in advance for your reply,
Hans
- Labels:
-
Configuration
-
Set Up
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-05-2012 11:55 AM
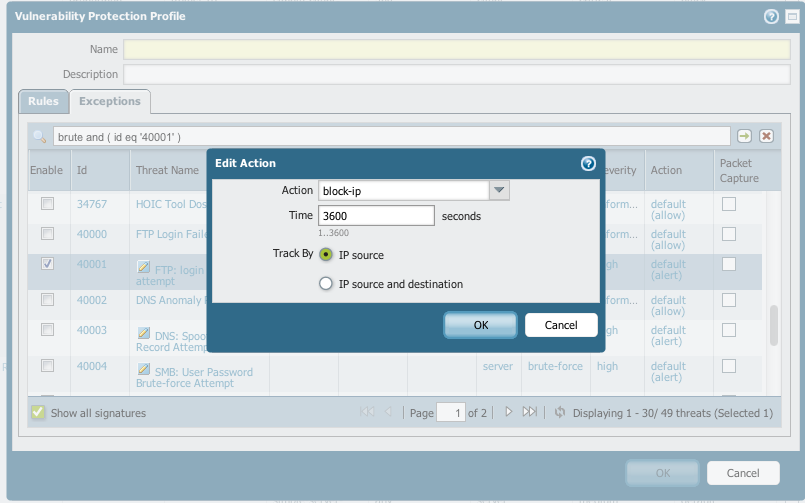
Try changing the action to 'block-ip'. Block will only block the packet/session related to the violation, which doesn't work very well for attacks based on cumulative attempts.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-05-2012 11:55 AM
Try changing the action to 'block-ip'. Block will only block the packet/session related to the violation, which doesn't work very well for attacks based on cumulative attempts.

- Mark as New
- Subscribe to RSS Feed
- Permalink
07-05-2012 12:05 PM
What is the actual signature that is being enabled behind that exception rule? Is it a custom sig or the Palo Alto Networks ftp brute force sig?
- 1 accepted solution
- 5072 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!



