- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Blocking EFSRPC
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Blocking EFSRPC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2023 09:01 AM
In the 7/17 content release notes, improvements have been made to "Suspicious Encrypting File System Remote call (EFSRPC) to domain controller' generated by XDR Analytics BIOC detected on 2 hosts."
By default, the action for this is to detect/alert. I would like to change this to block. Does anyone know how to accomplish this? Better yet, what is the best way to determine which cortex settings/policies apply to a specific Incident? Is there some master list of Incident types and respective settings?
I looked through Prevention Profiles and could not find a setting that makes sense for the EFSRPC alert. Thanks in advance for any help you can provide.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2023 01:17 PM
Hi @Kyle_Begle,
Thanks for reaching out on LIVEcommunity!
In regards to the rule you're mentioning it is an analytics BIOC. This means there is not block functionality associated with it. Analytics BIOCs are not produced in real time and therefore cannot block. Please take a look at the Analytics Concepts. for a better understanding of how analytics work. Essentially it's looking at a lot of different factors after the event to determine the larger picture.
By looking into the activity that caused the alert you may be able to find similarities you can use to create a high fidelity BIOC which can be used to block unwanted activity in your environment.
I hope you find this information helpful. Have a great day!
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2023 01:17 PM
Hi @Kyle_Begle,
Thanks for reaching out on LIVEcommunity!
In regards to the rule you're mentioning it is an analytics BIOC. This means there is not block functionality associated with it. Analytics BIOCs are not produced in real time and therefore cannot block. Please take a look at the Analytics Concepts. for a better understanding of how analytics work. Essentially it's looking at a lot of different factors after the event to determine the larger picture.
By looking into the activity that caused the alert you may be able to find similarities you can use to create a high fidelity BIOC which can be used to block unwanted activity in your environment.
I hope you find this information helpful. Have a great day!
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-19-2023 08:12 PM
Hi @Kyle_Begle
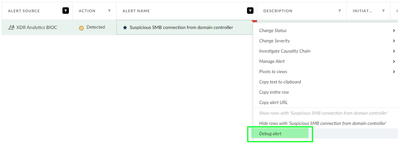
Just to add while looking into the activity that caused the alert you can "Debug alert" to see the interesting fields which can be used for creating BIOC and then you can configure BIOC rules as custom prevention rules and incorporate them with your Restrictions profiles as shared above by @anlynch .
Screenshot for reference:
Thanks
- 1 accepted solution
- 3180 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Detect and Block Openclaw with XDR!? in Cortex XDR Discussions
- Notepad++ block specific hash version in Cortex XDR Discussions
- I want to block commands and special operations that require administrator privileges on Windows. in Cortex XDR Discussions
- Cortex XDR Blocking Intel process in Cortex XDR Discussions
- Block Execution of Specific Applications Regard of version in Cortex XDR Discussions