- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Is it possible to block IOC from Cortex XDR?
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XDR Discussions
- Re: Is it possible to block IOC from Cortex XDR?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 08:36 AM - edited 08-12-2022 08:50 AM
I'm trying to block domain across in our environment. I don't want to use url filtering on PA FW, but I want to use XDR IOC to block it. is possible to do it?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 08:40 AM
Hi Hpatel11,
Unfortunately, no, it is not possible to block IOCs with Cortex XDR directly, the IOCs exist only on the XDR server and are not sent to the agents. If you are an XDR Pro per Endpoint or Pro per TB customer, you can set up External Dynamic Lists and have your NGFW subscribe to those lists to automatically update your firewall policy directly from XDR.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 08:40 AM
Hi Hpatel11,
Unfortunately, no, it is not possible to block IOCs with Cortex XDR directly, the IOCs exist only on the XDR server and are not sent to the agents. If you are an XDR Pro per Endpoint or Pro per TB customer, you can set up External Dynamic Lists and have your NGFW subscribe to those lists to automatically update your firewall policy directly from XDR.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 08:48 AM
Hi @hpatel11
if IOCs are hashes you can block them adding them to the block list
Then as Afurze mentioned you can add other IOCs or internet web-sites to the EDLs so you can block them on your FWs
Other indicators like malicious email senders can be added (by your own procedures) to email server black lists...
Think of other tools you might have at your organization in order to appropriately block all kinds of IOCs
I hope this helps,
Luis
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 10:39 AM
I did this in my poc(long time ago), I blocked like www.heise.de through BIOC with restriction rule.
When I surfed on this webpage the whole browser got closed.
If you want I can repeat it in my cortex xdr pro per endpoint Environment.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 10:43 AM
I checked on BIOC but don't see anything for Domain. I see that we can do by IP.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 10:52 AM
Have you tried to take a network query to view which field the domain is called?
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 11:09 AM
Got it it's called action_external_hostname Let me try to use this.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 11:57 AM
I was able to create BIOC but can't associate BIOC with prevention policy. It's not syntax issue because I was able to trigger alert on it.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 12:14 PM
I think you need to do this from BIOC perspective. Not from the alert/incident perspective.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 12:16 PM
This is only option that we got.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 12:43 PM
So the guys from PA are right. You can only prevent with BIOC the processes.
At the moment I cannot say why it worked at my POC. I remember, when I opened the page the whole browser went down.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-12-2022 12:46 PM
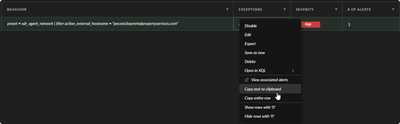
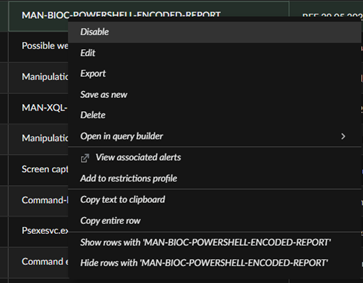
and by the way, you can add process BIOCs through right clicking and add to restriction profile.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-17-2022 12:41 AM
@Cyber1985 , please be notified that it is a process activity using network connection to destinations for incoming, outgoing and failed connections only. There is still a possibility for raw packets which is not something can be blocked using Cortex XDR.
Additionally, the BIOC rule as resriction actually blocks your browser process action and repetitive actions like these can be risky leading to crashing of the application itself and you might have to reinstall the application again.
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-17-2022 05:17 AM
Thank you very much for this information! I can remember that in my test the complete browser was "closed" automaticly.
- 1 accepted solution
- 12250 Views
- 15 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Can we upgrade Cortex XDR agent version to CE version from console ? in Cortex XDR Discussions
- TELAM SERVICES IS STOPPED - CORTEX XDR in Cortex XDR Discussions
- Cortex XDR - How do I open a new feature request? in Cortex XDR Discussions
- Cortex XDR Broker VM content cashing verification in Cortex XDR Discussions
- Cortex XDR manager upgrade in Cortex XDR Discussions