- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to get the process id from crowdstrike (CS) integration
- LIVEcommunity
- Discussions
- Security Operations
- Cortex XSOAR Discussions
- Re: How to get the process id from crowdstrike (CS) integration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-30-2023 12:41 AM
- https://xsoar.pan.dev/docs/reference/integrations/crowdstrike-falcon#30-cs-falcon-process-details
- https://xsoar.pan.dev/docs/reference/integrations/crowdstrike-falcon#51-cs-falcon-rtr-list-processes
- https://xsoar.pan.dev/docs/reference/integrations/crowdstrike-falcon#7-cs-falcon-run-command
Hi Folks,
In my context I do have the malware process path and malware filename too, I need to find out the local process id in the host.
Please suggest what is best way to do it.
case 1: When I try to use the cs-falcon-process-details it simply gives me the same input paramter in different fields, I was expecting to use the process_id_local, but it is the 2 part of the string split on ":". PFA result.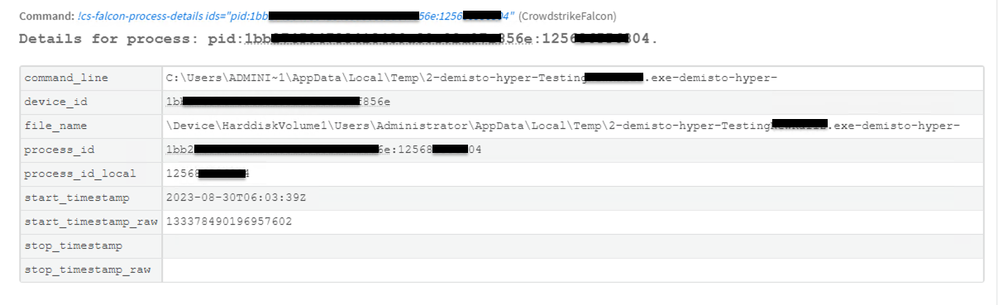
case 2: Try to remote fetch list of all running process but result is a big file and I can not process or use it in my playbook to filter 
case 3: Try to remote run the ps but the result is too big and I can not pass grep like sub commands to filter.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-03-2023 10:25 PM - edited 09-03-2023 10:31 PM
hi,
I was not looking at transformation.
Q- "In my context I do have the malware process path and malware filename too, I need to find out the local process id in the host.
Please suggest what is best way to do it."
Did some research and got some help from colleagues used powershell and runscript integrations to get the result; And used extend context to add it context data.
!cs-falcon-run-script host_ids="1bbxxxxxxxxxxxxxxxx7f856e" raw="$t=Get-Process ${incident.malwarename} | Format-List Id,ProcessName;Write-Output $t|Out-String -Stream" timeout="30" queue_offline="false" extend-context=true
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-31-2023 03:52 PM
Hi,
You can use the Set automation, in the context key, name it with the key you want to save it as. For example, process_id. In the value, you can set the value where you’ve process ID in 2 parts. Use a split transformer and split it at : and call last array element transformer which will get and return the second element (which is last in this case). This will essentially transform and store the process ID in the process_id key.
You can refer to https://youtu.be/795E42gz8M8?feature=shared for video on using transformers.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-03-2023 10:25 PM - edited 09-03-2023 10:31 PM
hi,
I was not looking at transformation.
Q- "In my context I do have the malware process path and malware filename too, I need to find out the local process id in the host.
Please suggest what is best way to do it."
Did some research and got some help from colleagues used powershell and runscript integrations to get the result; And used extend context to add it context data.
!cs-falcon-run-script host_ids="1bbxxxxxxxxxxxxxxxx7f856e" raw="$t=Get-Process ${incident.malwarename} | Format-List Id,ProcessName;Write-Output $t|Out-String -Stream" timeout="30" queue_offline="false" extend-context=true
Thanks
- 1 accepted solution
- 7115 Views
- 2 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Looking for 2FA/MFA/OTP Solution to Support Authentication for Cortex XSOAR v8 (On-Prem) in Cortex XSOAR Discussions
- Resolving CrowdStrike ODS Scan Detections With Integration in Cortex XSOAR Discussions
- Fetching CrowdStrike Next-Gen SIEM Alerts into SOAR in Cortex XSOAR Discussions
- Extrahop Reveal X Integration - Stop fetching of Hidden Detections possible? in Cortex XSOAR Discussions
- Getting Vulnerability Findings from Tenable SC for a Specific Host in Cortex XSOAR Discussions



