- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Detecting an SSLv2 Server Response with a Custom Signature
- LIVEcommunity
- Discussions
- Custom Signatures
- Detecting an SSLv2 Server Response with a Custom Signature
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Detecting an SSLv2 Server Response with a Custom Signature
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-02-2016 02:40 PM - edited 03-02-2016 02:59 PM
DISCLAIMER:
As with all custom signatures on this forum, this signature is being provided by the author as a result of enthusiasm for the product and to share ideas with the Palo Alto Networks security community.
It is:
- Not recommended for deployment in a production network of any kind.
- Not a solution to any vulnerability.
- Not an official supported Palo Alto Networks signature.
That said, I do hope it will illustrate to interested community members what can be done with the strength of the Palo Alto Networks custom signature engine.
With SSLv2 vulnerabilities continuing to present themselves, customers may find themselves interested in knowing when a session established with a server in their environment is leveraging this cryptographic protocol.
Palo Alto Network's custom signature engine can help you accomplish exactly this.
While the pattern matching contexts we expose are incredibly useful for looking for specific types of data, integer contexts are equally strong if you are looking to see whether or not an exposed context contains a specific value. Given the pattern matching contexts limitation of requiring seven static bytes as an anchor for detection, this makes more surgical tasks where you only want to evaluate a single field more difficult. For our example, the SSL version present in a Server Hello response is two bytes; this means it is not a candidate for a pattern matching signature.
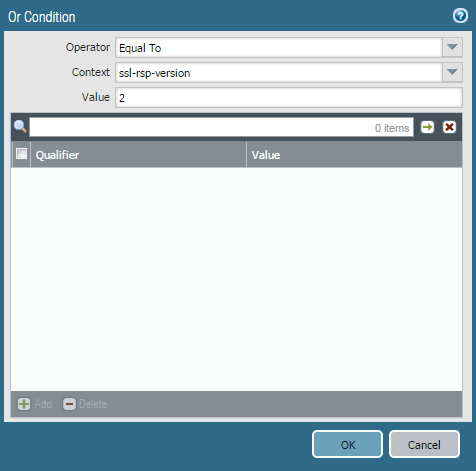
However, we expose ssl-rsp-version in the integer contexts, making the below possible:
In the signature I will attach to this thread, we are inspecting the "SSL-RSP-VERSION" integer context to see if it contains a value of 2.
This signature is an informational level that will alert when SSLv2 server responses are detected, allowing any network administrator who wants to be aware of this to take appropriate action.
As always, any feedback or corrections from the community is absolutely welcome.
- 4264 Views
- 0 replies
- 2 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- Cortex XDR blocks MalwareBytes in Cortex XDR Discussions
- XQL to detect the ScreenConnect Client in response to CVE-2024-1709 and CVE-2024-1708 in Cortex XDR Discussions
- SAML Login Issue with Token-signing Certificate in GlobalProtect Discussions
- What are the response steps to be taken in the event that DDoS is detected on the Palo Alto ? in Next-Generation Firewall Discussions