- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Cisco ASA To Panorama Partial Configuration question
- LIVEcommunity
- Tools
- Expedition
- Expedition Discussions
- Cisco ASA To Panorama Partial Configuration question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Cisco ASA To Panorama Partial Configuration question
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-29-2024 06:54 AM
We currently use Panorama to manage multiple firewalls across our organization.
We have a Edge ASA Cluster we are needing to migrate over to an existing pair of Palo Alto Firewalls, managed by Panorama.
I would like to only migrate over the Objects, Security Policies, and NAT rules, From the Cisco ASA config to the Panorama.
I have imported my ASA config into Expedition, is it okay to delete the network interfaces, zones, etc that were imported with the ASA config? and only focus on the objects, security policies, and nat rules?
Is the Best Practice way of merging the ASA objects, Security policies, and NAT rules to our Panorama, by using the Load Partial Config commands in the cli of the panorama?
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-29-2024 08:19 AM
Thank you for reaching out.
In Expedition, you can manage Objects and Policies, which should be sufficient. However, please note that if your rules reference specific "zones", these zones must be declared in your device (Panorama). Otherwise, you will not be able to push or commit your configuration. The same applies to tags and other objects used in your Objects or Policies.
To ensure best practices, please follow these guidelines:
-
For network-related information such as interfaces and zones, use the "set" command on the CLI.
-
For objects such as tags, addresses, address groups, services, service groups, applications, routes, security rules, and NAT rules, use the "load partial mode merge" command on the CLI.
If you have any further questions, feel free to ask.
Thank you!
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-29-2024 10:55 AM
Yes, the Zones on my Panorama managed firewalls are different than what was imported into Expedition from my ASA config.
For clarification, I will need to change the Zones on my Expedition ASA config to match that of what I will be applying them to on the Palo Alto config?
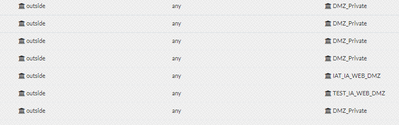
For example.
ASA Config in Expedition
On my Palo Alto managed firewalls, the zone name I will be applying these rules to is named "WEB_DMZ" for the dmz side, and "Outside" for the outside side. Will it error out being that the Cisco outside interface is a lowercase o vs the Palo Alto side is a Capital O.? Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-01-2024 08:46 AM
I recommend that the security rules and NAT rules contain the correct names of your zones before pushing them to your device.
You can do that by renaming your zones or by doing a bulk change on your security rules updating the field zone to and zone from.
Let me know if I can help in anything else,
Best regards,
David
- 643 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!