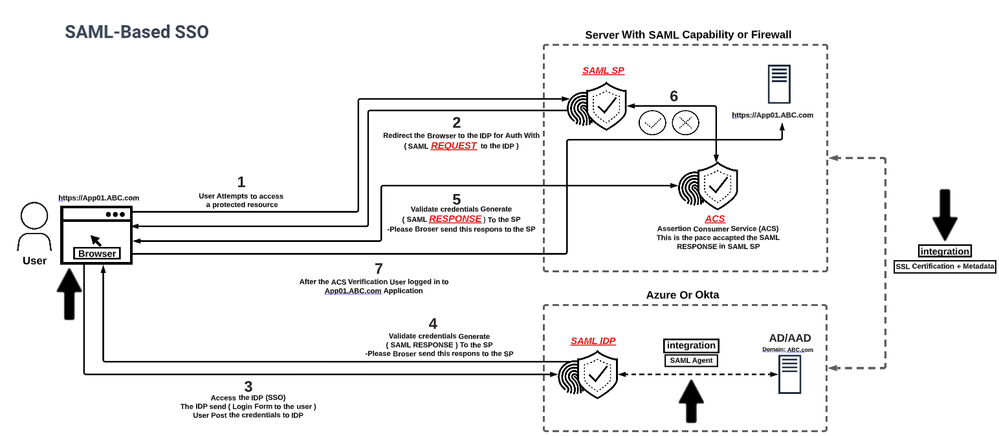
As a SAML-based, single sign-on (SSO) login summary with most of SAML components in the picture below, I want to point out some important things that need to be done to make SAML work:
- SAML is XML-based protocol used for exchanging authentication and authorization data between different parties, so we'll need the user's browser to handle that
- Any authentication needs a database to validate the users against it. You can store or create users in Identity Provider (IDP) as user's database, but most of the time you'll need to integrate IDP with Active Directory or Azure Active Directory
- Identity Provider (IDP) and Service Provider (SP) don't talk to each other during SAML user verification. To make SAML work, you need to connect IDP with SP ahead of time. IDP and SP need to exchange metadata and get SSL certification for this integration to work. The SP and IDP must establish a trust relationship, which involves exchanging metadata that includes information about each other's endpoints, public keys, and other configuration details
SAML (Security Assertion Markup Language) protocol components and messages based to single sign-on (SSO):
- Identity Provider (IDP): The system responsible for authenticating users and issuing SAML assertions that contain information about the user's identity and attributes
- Service Provider (SP): The system that provides access to protected resources or applications and that relies on SAML assertions issued by the IDP to authenticate users
- Assertion Consumer Service (ACS): A web endpoint on the SP that receives and processes SAML responses from the IDP
- SAML Request: A message sent by the SP to the IDP requesting authentication and authorization for a user
- SAML Response: A message sent by the IDP to the SP containing a SAML assertion that authenticates the user and provides information about their identity and attributes