- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Avaya 9611G/4610SW VPN to PA-500
- LIVEcommunity
- Discussions
- General Topics
- Avaya 9611G/4610SW VPN to PA-500
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Avaya 9611G/4610SW VPN to PA-500
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-06-2012 11:34 AM
Has anyone had success connecting Avaya IP phones via VPN to PA devices? I am able to complete IKE Phase 1 authentication, but fail Phase 2 due to local/remote proxy IDs not found:
'IKE phase-2 negotiation failed when processing proxy ID. cannot find matching phase-2 tunnel for received proxy ID. received local id: 192.168.50.0/24 type IPv4_subnet protocol 0 port 0, received remote id: 172.16.33.2/32 type IPv4_address protocol 0 port 0.' )
I'm not sure where to configure the phase 2 parameters as the phase 1 connection occurs using a Global-Protect Portal/Gateway. The remote ID matches the address received by the client from the G-P Gateway pool.
If you have had any success with these devices, please help!
Thanks,
Steve
First Annapolis
- Labels:
-
Configuration
-
Networking
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 11:10 AM
Hello, was there every any discussion about making GlobalProtect compatible with the Avaya phones. Just recently tried it with the settings discussed in the forums, but could not get past Phase 1.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-31-2017 08:18 AM
In order to get the Avaya 96xx IP phones to connect to a GlobalProtect gateway, I found there are certain settings that need to be configured on the phone in order to make it work. I spent about 3 days going through different configuration setups and what I found was that the phones will auto-negotiate the IKE Phase-1 parameters, but for some reason will not negotiate the Phase-2 parameters automatically. The solution that worked for me was setting the following parameters in the 46xxsettings.txt file used to program the phones via http.
SET NVVPNMODE 1
SET NVIKECONFIGMODE 1
SET NVIKEIDTYPE 11
SET NVIKEXCHGMODE 1
SET NVVPNAUTHTYPE 4
SET NVSGIP "vphone.yourdomain.com" (I recommend using FQDN if possible. Static IP can cause challenges later if ISP changes)
SET NVVPNPSWDTYPE 1
SET NVVPNENCAPS 0
SET NVIKEPSK "your-psk-password-here"
SET NVIKEID "vpnphone@yourdomain.com" (This is also referred to as the Group Name)
SET NVIKEDHGRP 2
SET NVIKEP1ENCALG 0
SET NVIKEP1AUTHALG 0
SET NVIKEP2ENCALG 5 (manually sets Phase-2 IKE to aes-256)
SET NVIKEP2AUTHALG 2 (manually sets Phase-2 auth to SHA-1)
SET NVPFSDHGRP 0 (this is important - none of the P2 settings above would have any effect until PFS was disabled)
SET NVIKEP1LIFESEC 86400 (phone defaults to 432,000s, which is 5 days - I set here to 1 day or you can keep default)
SET NVIKEP2LIFESEC 86400
This will work with the 96xx series of Avaya IP phones and I can provide additional details/notes in case anyone is looking to connect one over a VPN connection to a GlobalProtect gateway. I had to migrate the configuration from a Juniper SSG firewall to Palo Alto PA-850 , which provided some challenges since there really is no Avaya documentation or support information available that discusses setting up a VPN phone on the Palo Alto platform. Good Luck!!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-12-2020 05:00 AM
I was interested to read your post about connecting Avaya 96xx phones to a Global Protect Gateway ovewr VPN.
We are looking to do something similar and wondered if you could share your notes and in particular the configuration of the PA gateway?
Regards
Stuart
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-25-2020 06:13 AM
Any information about this I am trying to do the VPN too
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-01-2020 02:02 PM - edited 04-01-2020 02:05 PM
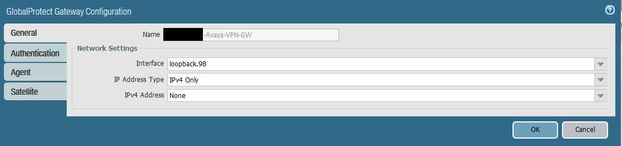
Sure. Here are some screenshots from my gateway configuration if that helps. Don't forget you will need rules to allow traffic between zones and you will also need an internal route pointing to the Palo Alto firewall for whatever IP pool you assign that will issue IPs to the phones.
For the interface, I have a public IP assigned to the loopback interface but you could also use your gateway interface, whatever is easier. I have a block of IPs I use outside of the main gateway interface, which is why I am using loopback.
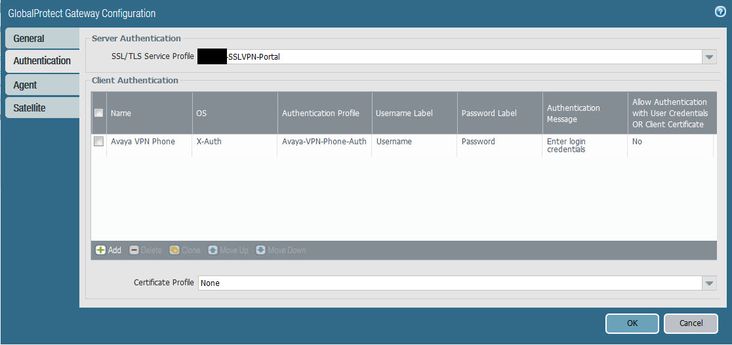
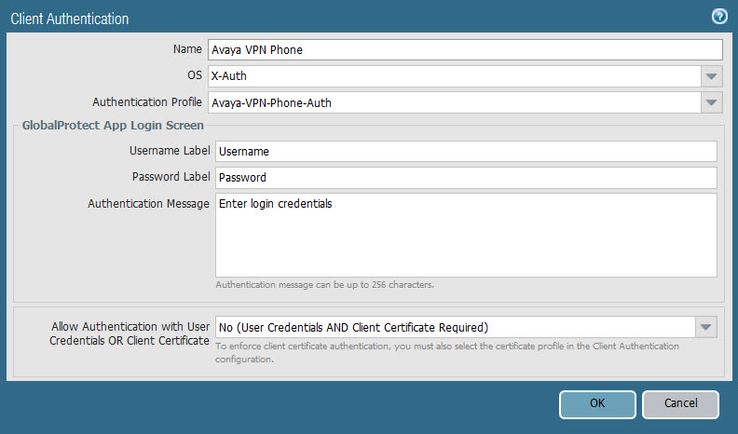
For the authentication page, you can select an existing or create an SSL/TLS Service Profile. For client authentication, you will want to set the OS type to X-Auth as shown here. The next screenshot shows the Client Authentication settings.
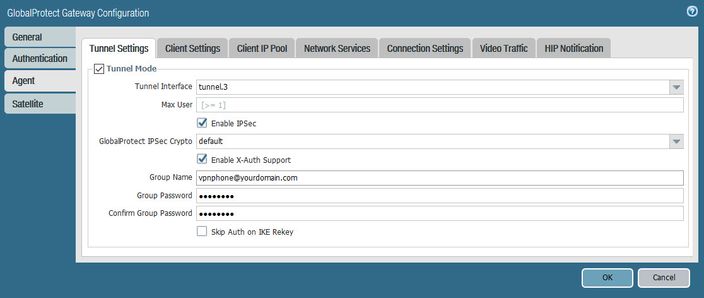
For the GlobalProtect Agent tab, you'll select a tunnel interface, enable IPSec, enable X-Auth support and set the Group Name parameters as shown. This is what will need to match in the Avaya configuration I detailed in my post above.
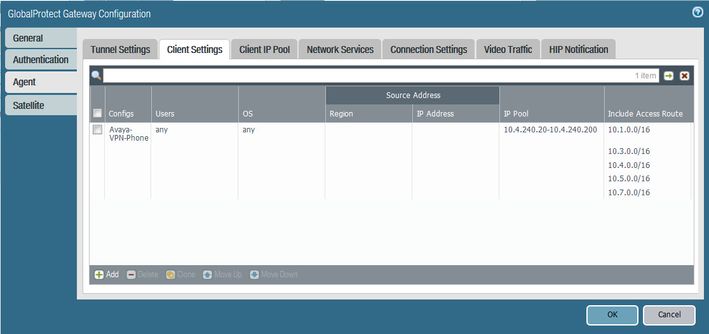
Next click on the Client Settings tab and setup the IP Pool you will assign to the phones. You'll also need to split-tunnel your internal routes for the Avaya phone system and other user VoIP subnets.
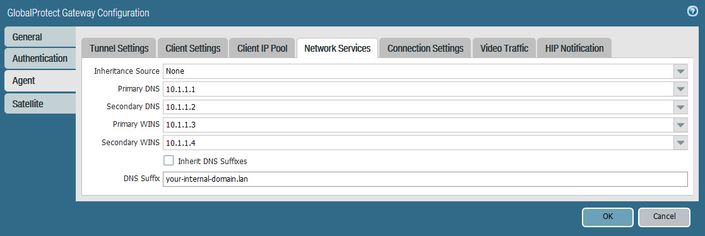
I'm not 100% sure these settings are required unless you are doing FQDN for the Avaya system. Our Telecom team has everything going to host IPs so we really don't use any DNS on the phones. I just included for reference.
That's really all there is to it really. I setup a completely separate GP gateway just for the phones and I have all of my regular VPN users connecting on a different gateway but I also have a pool of public IPs to pull from where as that may not be an option.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-14-2020 04:52 PM
Howdy,
I just wanted to pipe up and say thanks for this. With it, myself (firewall/networks) and our in-house phone/networks guy were able to build out a solution new to our environment. It saved us a TON of time.
2 x 5220 active/passive (8.1ish) and an Avaya 9641gs test phone.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-01-2021 12:39 PM
This post was really helpful and I was able to bring up the tunnel between Avaya phone and Palo alto firewall. Additionally, I'm trying to authenticate phone using both user credentials ( local user) and a certificate. However, phone was able to authenticate just using the credentials and firewall not even checking for certificate. one of the problem here is Avaya phone asks for user name and password when it makes VPN connection so I dont have option to use "OR" in client authentication settings inside gateway configuration. I'm wondering if someone tried or using this kind of authentication. Any help is appreciated.
Thank you,
Naveen
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-20-2023 05:39 AM
Hi,
To setup VPN Tunnel for Avaya IP Phones, you just need to configure RemoteVPN (GlobalProtect) and need to enable x-auth, thats it. X-Auth is the feature which is must to connect the Avaya IP Phones (as it considered as 3rd party vpn client). You dont need to have GlobalProtect license as Avaya IP Phones Operating Systems dont fall in Mobile/Tablet devices.
I just implemented in April 1st Week. I was migrating all Avaya IP Phones VPNs from Cisco ASA to PaloAlto firewalls and it worked without any issues.
- 26314 Views
- 22 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Prisma SD-WAN DHCP option 242 in Prisma SD-WAN Discussions
- PA500 not being powered on for years refuses to boot... in Next-Generation Firewall Discussions
- Unable to launch application when terminal server agent is installed in General Topics
- Global Protect Gateway on PA500-VM in GCP in GlobalProtect Discussions
- Factory reset in General Topics