- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Best Practices for Security Policies with App Default and Custom Services
- LIVEcommunity
- Discussions
- General Topics
- Re: Best Practices for Security Policies with App Default and Custom Services
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Best Practices for Security Policies with App Default and Custom Services
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-21-2018 10:00 AM
Hello,
I have been tasked with converting some legacy security rules from app=any, service=custom object to app=app-ID and service=application-default. However, some of our apps use custom ports over known applications, so straight conversion is not possible.
For example. I have a basic rule to allow inbound applications web-browsing (tcp/80) and ssl (tcp/443) to one of our web servers using application-default for the service. This web server also supports HTTP over 8080, and HTTPS over 8443. Instead of creating one rule for the apps/application default, and another rule below it for the apps/custom service objects, I would prefer creating a single application default rule that incompases HTTP over both 80 and 8080, and SSL over 443 and 8443 in order to keep the firewall rules clean.
To do this, I have created two custom applications objects, web-browsing-8080 using the web-browsing as the parent app over port 8080, and app object ssl-8443 using ssl as the parent app over port 8443. I do not have signatures defined for either custom apps, and we are not decrypting inbound SSL. Understandibly these custom apps are not recognized by the firewalls that otherwise matches web-browsing over 8080 and SSL over 8443. I am new to custom App-IDs so it's likely I'm approaching this wrong.
What are the best practices regarding configuring applicaiton rules for both application-default and custom services objects? Is it recommended to create two rules, one with app-default and the second with the app and custom required ports, or is it better to create a single rule using custom app-IDs to enforce application-default?
Thanks for your time!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-21-2018 02:12 PM
Hello,
While I do not have custom applications that I created. The solution I use is to build the policy with all the ports the application will need
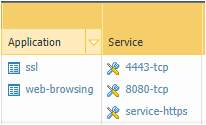
Here is an example of a policy I have with standard rules and non-standard ports:
This way the firewall has to see those applications, ssl or web-browsing, over the specified ports listed. Wile this might not answer your question, I hope to give another way of doing it suggestion.
Cheers!
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-22-2018 04:01 AM
I think @OtakarKliers solution makes the most sense, unless you have more specific custom apps: ones you can identify by their behavior, like a recurring header or payload string you can match in a signature
if you need lots of these, I'd recommend grouping them in security rules by 'technology' so there's no unexpected port creep (sql over port 80)
PANgurus - Strata specialist; config reviews, policy optimization
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-22-2018 08:58 AM
Thanks for the feedback Otakar.Klier! I appreciate it! I will discuss this method with my team and update the post if required.
-j
- 11502 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Threat Protection Coverage for LockBit 5.0 in General Topics
- Issue with allowing AnyDesk on a no-internet policy in Next-Generation Firewall Discussions
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions
- UserID mapping for users usings Azure VPN Gateway and AzureAD in Next-Generation Firewall Discussions