- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Block the remote desktop acces with Palo Alto Network
- LIVEcommunity
- Discussions
- General Topics
- Re: Block the remote desktop acces with Palo Alto Network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Block the remote desktop acces with Palo Alto Network
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2015 02:35 AM
Hello,
In or company i need to block the remote desktp access of a specific address to the critical server like database server.
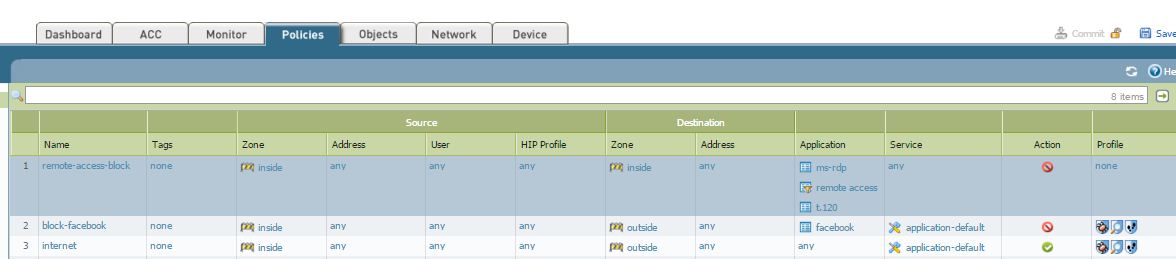
I add a security rule in the PA-500 by block (ms-rdp and t.120) applictions to a specific address by without any result.
How could i blck the remote access ?
Please i need you help
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2015 03:28 AM
Hello,
You find in the attachment a screnshoot of the recurity rules in the PAN
Thank you
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2015 04:36 AM
you want to block same zome traffic? so if your client and server are on the same subnet the traffic will not forward to your palo alto (which is the default gw from your clients i think).
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2015 05:06 AM
Yes the servers and the clients desktop are in th same subnet , the same security zone . So , I can't block the traffic in this case with the PAN?
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2015 05:44 AM
If you can't put server to seperate subnet then you could do it with virtual wire or layer 2 setup.
Keep in mind that traffic has to pass the firewall.
If client and server are both connected to switch then they talk directly and traffic does not pass firewall and you can't block this traffic.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2015 07:03 AM - edited 11-27-2015 07:04 AM
ok thank you, so i can this by configuring a virtual wire in the firewall , i connect the servers directly to the firewall or by usig another switch . It it in the zoe named "serverzone". Then, i add a security rules from "internal" rules to the "serverzone" by restrict the ms-rdp.
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-27-2015 07:57 AM
It is best practise to have users and servers in diferent zones.
What you could do at the moment is to add another layer 3 interface to same zone you have already (inside) and attach server directly to it.
Multiple interfaces can be in same zone.
But in this case your traffic from inside zone to inside zone passes firewall and you can control this traffic.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-30-2015 03:11 AM
you could split up the user and server space by putting them in different VLANs and then using the firewall as bridge, that way you should be able to keep your subnet configuration
please take a look at this guide: Getting Started: Layer 2 Interfaces
PANgurus - Strata specialist; config reviews, policy optimization
- 11199 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- False positive (generic.ml): HelpDesk Viewer in VirusTotal
- Prisma Access alert notifications in Prisma Access Discussions
- Renew Palo Alto Global Protect Certificate issued by Public CA in General Topics
- Please tell me about the maximum number of sites that each Remote Network SPN can accommodate. in Prisma Access Discussions
- Azure Virtual Desktops integration with Global Protect nightmare in GlobalProtect Discussions