- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Botnet Syslog
- LIVEcommunity
- Discussions
- General Topics
- Botnet Syslog
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Botnet Syslog
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2013 10:58 AM
Hi guys,
I have a syslog that I make some monitoring dashboards and the customer want one view about all botnets in my network.
I had configured Palo Alto to send the logs to syslog. But I can't found the log about botnet.
Somewhere know how can I do this? What log that we can see the infections?
Thanks for the help!!
Best Regards
Lucas Passos
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-18-2013 09:41 AM
Hello Lucas,
Botnet Reporting is a threat prevention feature. The PAN collates information from traffic, threat, URL logs to identify botnet-infected hosts. The report generated each day consists a list of infected hosts, description(why we believe the host is infected) and a Confidence level. You can configure the parameters in addition to the query indicating what traffic you'd like to see the botnet report on. There are no Botnet logs, just predefined Botnet reports that run daily.
However, you can configure botnet reports to be emailed out on daily basis according to your email server profile.
Under Monitor > Botnet > Report setting
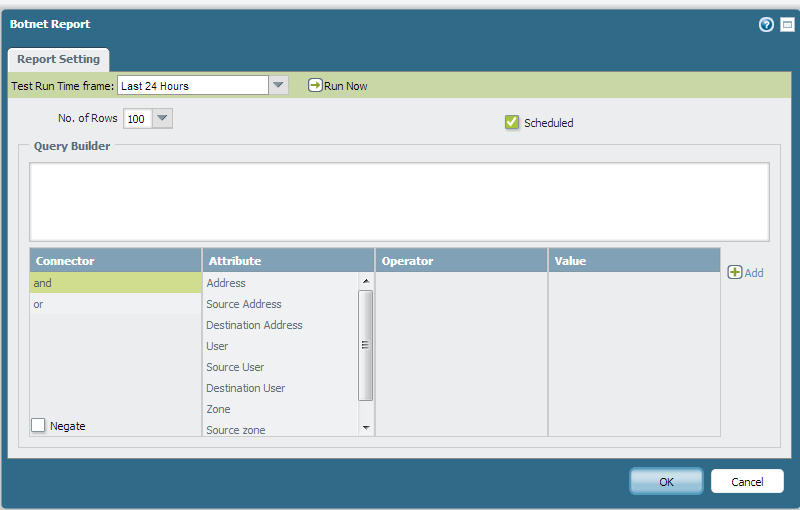
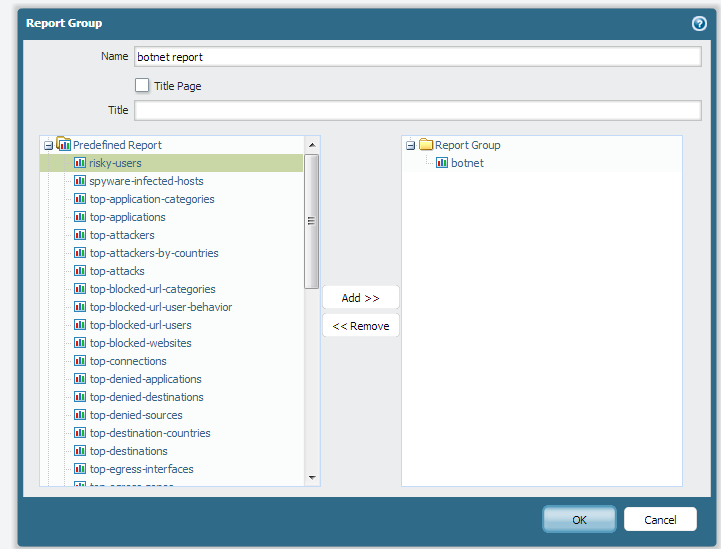
You can then create report group to include that botnet report
You can then create an email scheduler with email server profile to include that report group
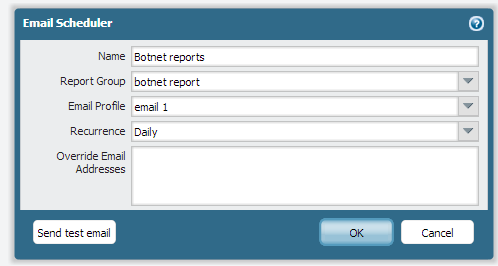
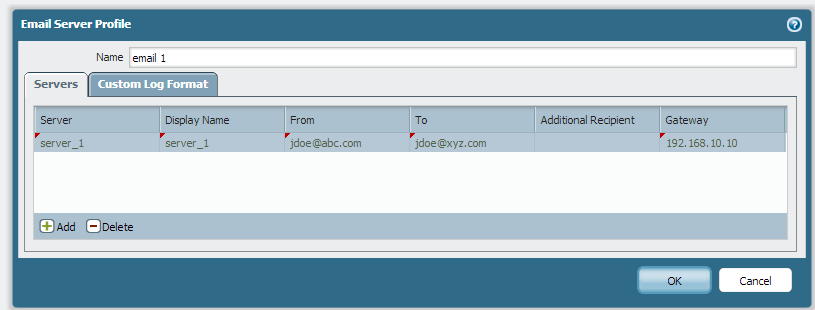
The above process who trigger an email (botnet report attached to it ) everyday to jdoe@xy.com
Since there is nothing called botnet log, we cannot forward it to any external server. On another note, you can indeed forward your threat logs to external entities by following the document:How to Forward Threat Logs to Syslog Server
Hope thats helps!
Regards,
Kunal Adak
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-19-2013 04:22 AM
Hello kadak!
Thank you for the answer. I was think about send email. Really I'll do this. But, it's not the perfect way, because I'll wanted make a dashboard. With the dashboard I'll can monitoring in real time.
Best Regards!
Lucas P
- Mark as New
- Subscribe to RSS Feed
- Permalink
02-23-2015 01:34 PM
Have you considered the API on your PA?
Since the botnet report is a predefined report, you can pull it using the API with a URL like this:
https://PA_FIREWALL_IP/api/?type=report&reporttype=predefined&reportname=botnet
With that in play, all you have to do is have something pull that URL (need to add the API auth string to the request first) and change out the IP address with that of each of your firewall modules. As long as the server (QRadar) for example, is configured to read the XML responses, you can read and act as needed on the report results.
You can pull the CSV's straight out as well - but that takes two requests - one to generate the report and the other to fetch the result.
Cheers.
- 5466 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Sending USB Alerts via syslog (Cortex XDR) in Cortex XDR Discussions
- Push Cortex XDR datasets/logs to dedicated syslog server in Cortex XDR Discussions
- Log forwarding from Cloud NGFW in Azure to Log Analytics Workspace for Sentinel in VM-Series in the Public Cloud
- XDR as "SIEM" (challenge for discussion) in Cortex XDR Discussions
- CorteXDR License Pro - Send Event in Cortex XDR Discussions



