- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Can you setup a S2S VPN behind your Outside (untrusted) interface on same firewall?
- LIVEcommunity
- Discussions
- General Topics
- Re: Can you setup a S2S VPN behind your Outside (untrusted) interface on same firewall?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Can you setup a S2S VPN behind your Outside (untrusted) interface on same firewall?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-23-2023 03:01 PM
Hi
I am using a pair of PA-3250 in HA and have 17 S2S VPNs using my outside interface that has /24 public IP assigned to it. Due to ongoing issues with our current internet, we have decided to move to a different internet platform (DIA) and enhance our redundancy (enable BGP).
However, with this new setup, the ISP must give us a new /29 block to exchange BGP. As a result, the current /24 subnet and the IP we use for VPN peering will sit behind this new IP block on the same PA.
Someone mentioned to me the 17 S2S tunnels will not work and IPSec tunnels must be terminated on the interface closet to the remote peer. VPN traffic cannot enter the firewall on one interface, cross the backplane and then be delivered to a second interface.
Any feedback and possible work around will be appreciated.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 05:45 AM
Hi @highmiles ,
Am I understand you correctly - you plan to connect second ISP to your firewall using new public range, but you want to keep your IPsec tunnels using the existing/old public range for local peer address?
In my humble opinion Palo FW is your least concern in such setup...
- How do you plan to route old-ISP public /24 to point to your new-ISP public /29?
- How do you plan to route the return traffic from old-ISP interface back over new-ISP interface?
Why do you even want to do this way?
If you plan to completely migrate from old-ISP to new-ISP, just change your IPsec tunnels to use new-ISP interface as local peer.
If you plan to have ISP redundancy and want to failover IPsec tunnel over each ISP depending on the path, you will need to create additional tunnels over the new-ISP to all 17 remote sites
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 05:54 AM
"Someone mentioned to me the 17 S2S tunnels will not work and IPSec tunnels must be terminated on the interface closet to the remote peer."
This someone was incorrect.
You can run IPSec tunnels anywhere.
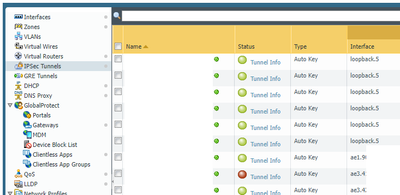
Even on loopback interfaces.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 05:58 AM
/29 will be for BGP peering.
/24 will be advertised to ISP and ISP will advertise it further.
You can get default route from ISP through BGP or have static route to ISP next hop in /29 range.
Important is to ask ISP to filter only default route to you and not send whole internet routing table down to your Palo.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 10:05 AM
Both old IP block and new address block will be on the same PA, the new block will have a new Zone name.
My question was specifically regarding my VPNs peer address that i am currently using, will it work if i move it one hop (on the same PA) behind the new IP block?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 10:07 AM
Yes it will work.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 10:11 AM
I like this answer! The IPSec will still work even if I used Loopbacks interfaces, interesting.
So, this guy we hired (from a well-known Paloalto partner) tells me otherwise, and he has 15+ years of experience.
He suggested i purchase VPN concentrators! (Something i don't want to do).
I am really puzzeled 😞
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 10:17 AM
You should find better partner to work with.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 10:19 AM
Hi Radio_Rattameister
I am not worried about the architecture of this as much as I am worried about the VPNs.
So the new /29 block will be used between me and the ISP, my current /24 block willl still be on the same PA but one hop behind.
All of this is being done to enable fail-over the /24 block to my other data center in case of a DR.
Maybe there is trick or certain feature we have to enable for the IPSec to work if we introduce a new block Infront or the current public IP we use for VPN peering.
He said the same thing about my Global Protect for remote access (which runs on a separate PA), they will also be impacted.
Is there a guide or link on how to setup S2S (L2L) VPN IPsec on an interface that is not facing the public?
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 10:27 AM
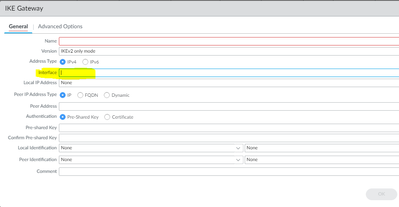
You just go to IKE gateways and change local interface.
Same with GlobalProtect.
You need to change interface on Portal and Gateway config.
Example below of working tunnels on non-public facing interface.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 10:40 AM
Why would i change my IKE gateway's local interface? That is what i am trying to prevent in the first place.
I need to keep using the current VPN peer IP. (currently set to 204.x.x.10/24 and directly facing internet)
I will Introduce a new /30 block (or /29) between me and ISP and start distributing/propagating my /24 to ISP.
My /24 will now be behind this new /29 and peering to my 204.x.x.10/24 will be one hop away from internet.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 10:44 AM
Assuming you currently have 204.x.x.10/24 configured on ethernet1/1 and you move it to ethernet1/2
You need to change local interface droppdown from ethernet1/1 to ethernet1/2 because IP address 204.x.x.10/24 will move between interfaces.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-24-2023 10:51 AM
ok, i see, got it, this is assuming i am moving my /24 block. But i am not moving it 🙂 .
I will simply create new Zone and assign to new interfaces for the new /30.
I appreciate your input, let me go back to the consultant and challenge his theory, not sure if i will succeed, he is the expert.
Thanks again.
- 3916 Views
- 12 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA-415-5G not working with fresh T-Mobile SIM in General Topics
- GloablProtect + Explicit Proxy blocks WSL traffic. in GlobalProtect Discussions
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- PA-440 won't talk via network in Next-Generation Firewall Discussions
- Trying the DNSProxy feature for Static Response in General Topics