- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Creating an Authenticated Tunnel from One Internal Zone to Another Internal Zone
- LIVEcommunity
- Discussions
- General Topics
- Creating an Authenticated Tunnel from One Internal Zone to Another Internal Zone
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2021 03:37 PM
I would like to create a secure internal tunnel such that a user requires authentication (ideally MFA, or a cert, or at least a PW, etc) to get from one internal zone to another internal zone (ie user zone to the management zone). What are my options?
Is anyone doing this sort of thing with Okta? Is there a certificate based way to do this? Other ideas?
If anyone can point me to some materials, or just help me know better what to search for or what the solution is called, I'd be delighted.
Thanks!
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2021 05:28 AM
Hi @pomologist ,
Great document find! Why don't you add the management zone to your authentication policy? Am I missing something?
Hi @BPry and @OtakarKlier ,
In the newer PAN-OS, the Captive Portal Settings tab under Device > User identification has been renamed Authentication Portal Settings. When I edit the setting and click on help, I see this message.
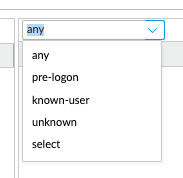
So, I don't think it is only for User/IP mapping or only triggers on unknown users in the newer PAN-OS. Also, in the Authentication Policy, you have a drop down for source users that can specify any, unknown, etc.
I have tested this with GlobalProtect, and I am required to authenticate on the web redirect page. My User-ID vpn-client data source existed before the captive-portal data source was generated.
I hope this helps,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-09-2022 12:36 PM - edited 05-09-2022 12:41 PM
Hi!
This is a bit late, but just wanted to let everyone know that I did indeed get this working using the guides here:
And here:
(although I wasn't integrating Prisma, the basic technique is the same)
This series is also very helpful:
https://live.paloaltonetworks.com/t5/blogs/globalprotect-overview/ba-p/322170 especially part IV
The final result is spectacular and wonderful. Thanks for all your helpful ideas!
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2021 05:39 PM
Do you already have user-id setup to properly identify the user so that you can authorize only the users needing access to management resources access to your management zone? If you have user-id setup properly I'm kind of missing the point of why you would want to do this, your accounts should be secured to the point where this is a none issue.
If you aren't using user-id I would recommend that you actually get it setup, but you can use an authentication policy to do this and capture the user-id for further use in your security rulebase.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-28-2021 08:20 AM - edited 10-28-2021 08:58 AM
Thanks very much for your input!
Yes I currently have user-ID set up for several zones, but user-ID captive portal redirect is currently only triggered on those zones when a user attempts to access the internet (user-zone -> internet-zone). I.e., the redirect is only triggering for http/https traffic.
I have tried doing user ID from a user-zone to management-zone - but I haven't found a way to trigger the authentication redirect to user-id captive portal in this case.
Any idea what I should check or what I'm doing wrong?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-28-2021 01:33 PM
Hello,
The captive portal is only for the PAN to perform user-id to IP mapping. How about something like making all users VPN in even from internal? This would accomplish your goals, but management will be not happy.
Just some thoughts.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-28-2021 03:30 PM
Hi @pomologist ,
The Authentication Policy (Captive Portal) can "authenticate end users before they can access services and applications." https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/authentication/authentication-policy.html They would have to use web-browsing/ssl as far as I know.
You could also create an internal GP gateway for access.
MFA can be used for both options. Check out the table -> https://docs.paloaltonetworks.com/compatibility-matrix/mfa-vendor-support/mfa-vendor-support-table.h....
Thanks,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-28-2021 03:51 PM
So I just found this knowledge base article that sounds like what I want to do.
Has anyone ever gotten this sort of thing working? I currently use the Okta Captive Portal for User ID, but again I can only get it working when http/https traffic triggers the captive portal. This would offer a great way to authenticate traffic between sensitive zones, if I can get it to work.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-28-2021 06:12 PM
Captive Portal will only trigger for users who aren't already authenticated and mapped to the IP via user-id. If you already have a user mapped to the IP it won't trigger anyways, regardless of it not being web traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-28-2021 06:31 PM
So far, that doesn't seem to have caused unwanted behavior for us with the existing Okta captive portal setup. On zones that use it, it authenticates reliably every time users attempt to access the web zone, repeatedly. I have not encountered a situation where it fails to authenticate anyone. It's fantastic because it's both multi factor, and auths against existing database of users in the Okta cloud LDAP.
If I could just take the exact way its currently working, and prompt for authenticating using captive portal the same way when accessing the management zone, as it does with the web zone.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-29-2021 05:28 AM
Hi @pomologist ,
Great document find! Why don't you add the management zone to your authentication policy? Am I missing something?
Hi @BPry and @OtakarKlier ,
In the newer PAN-OS, the Captive Portal Settings tab under Device > User identification has been renamed Authentication Portal Settings. When I edit the setting and click on help, I see this message.
So, I don't think it is only for User/IP mapping or only triggers on unknown users in the newer PAN-OS. Also, in the Authentication Policy, you have a drop down for source users that can specify any, unknown, etc.
I have tested this with GlobalProtect, and I am required to authenticate on the web redirect page. My User-ID vpn-client data source existed before the captive-portal data source was generated.
I hope this helps,
Tom
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-09-2022 12:36 PM - edited 05-09-2022 12:41 PM
Hi!
This is a bit late, but just wanted to let everyone know that I did indeed get this working using the guides here:
And here:
(although I wasn't integrating Prisma, the basic technique is the same)
This series is also very helpful:
https://live.paloaltonetworks.com/t5/blogs/globalprotect-overview/ba-p/322170 especially part IV
The final result is spectacular and wonderful. Thanks for all your helpful ideas!
- 2 accepted solutions
- 5841 Views
- 9 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Rapid connecting/disconnecting after some time in GlobalProtect Discussions
- Request Advice – BGP Failover Route-Based IPsec VPN With WatchGuard (WG) in Next-Generation Firewall Discussions
- Strata Cloud Manager with NGFW in Strata Cloud Manager
- One portal, multiple gateways for different users in GlobalProtect Discussions
- NATing Question in General Topics