- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Custom Application ports secure at Layer 7?
- LIVEcommunity
- Discussions
- General Topics
- Re: Custom Application ports secure at Layer 7?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2017 10:29 AM
Hi folks,
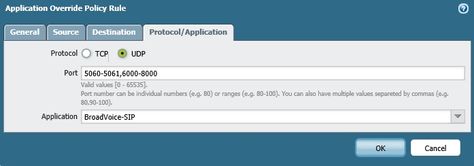
We have created an Application override and custom Application for SIP and RTP traffic. We also have Security/NAT rules that allow only this application (ports 5060, 5061, and 6000-8000) access to an internal VM with public IP directly.
As I am still learning PA, wanted to ask. Since we are using an Application (and override) that we created to open these ports, does PA still protect at the Application layer 7?
Will PA reject traffic from any other application to this server destination that may be using these same ports (maliciously)?
Application override policy rule. Added ports 6000-8000.
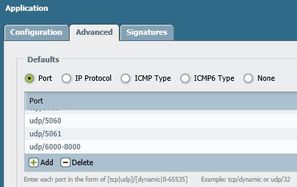
Application itself. Added ports 6000-8000
Security rule for Inbound SBC traffic.
NAT rule for Inbound SBC traffic.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2017 12:37 PM - edited 04-10-2017 12:49 PM
So there's a lot going on here, so please feel free to correct me on anything I may be misunderstanding here.
First and foremost, by using an application override policy, that traffic is now exempt from _both_ AppID and ContentID inspection. So yes, you lose layer 7 protection by using the application override policy. If it was strictly a custom App, it would still be subject to ContentID.
(ETA: I'm struggling to find the exact phrasing as such anywhere, but I am fairly confident this is the case. The closest I could find is this:
An application override with a custom application will prevent the session from being processed by the App-ID engine, which is a Layer-7 inspection. Instead it forces the firewall to handle the session as a regular stateful inspection firewall at Layer-4, and thereby saves application processing time.
Second, barring being more specific with source/destination, any traffic using those UDP ports will be automatically identified as the app and subsequently not inspected.
So you need to be very careful about this.
A custom App is the best approach. If you can correctly identify signatures in the traffic so the PA can reliably identify it as your custom app, you will have full protection.
CCNA Security, PCNSE7
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2017 11:09 AM
These two articles are a good start. PA will not use an app-id scanner for any override application. Your app simply will be identified based on matching UDP port (you told PA identify your app based on layer 4 TCP/UDP ports by creating app override rule). Your security profiles l believe still will take an action on allow traffic.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2017 12:37 PM - edited 04-10-2017 12:49 PM
So there's a lot going on here, so please feel free to correct me on anything I may be misunderstanding here.
First and foremost, by using an application override policy, that traffic is now exempt from _both_ AppID and ContentID inspection. So yes, you lose layer 7 protection by using the application override policy. If it was strictly a custom App, it would still be subject to ContentID.
(ETA: I'm struggling to find the exact phrasing as such anywhere, but I am fairly confident this is the case. The closest I could find is this:
An application override with a custom application will prevent the session from being processed by the App-ID engine, which is a Layer-7 inspection. Instead it forces the firewall to handle the session as a regular stateful inspection firewall at Layer-4, and thereby saves application processing time.
Second, barring being more specific with source/destination, any traffic using those UDP ports will be automatically identified as the app and subsequently not inspected.
So you need to be very careful about this.
A custom App is the best approach. If you can correctly identify signatures in the traffic so the PA can reliably identify it as your custom app, you will have full protection.
CCNA Security, PCNSE7
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2017 12:51 PM - edited 04-10-2017 12:53 PM
@bradk14 Good point regarding the security profiles. I must say l am not sure if security profiles actually taking an action with the policy override option or not. I can see you do have an option to use them while creating your custom app:
But when your traffic is matching the app override policy (your custom app) not sure if only app-id stops doing identification or as well as security profiles withing the normal policy also ignored.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2017 12:54 PM
As usual, thank you so much for your feedback, and so timely.
This Application and override was already in place when I arrived.
Based on feedback and my reading today, thinking of these questions now.
Why do we even have an Application override in this case? Could we just use the custom Application we created?
Just to confirm, given the fact we are using an Application override, means that technically not as secure for these ports since there is no App-ID associated with it, correct?
If you guys have additional feedback would be appreciated. Thanks again.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2017 01:07 PM - edited 04-10-2017 01:08 PM
@TranceforLife_technically_ the security profiles would 'work' for an application override, but since there is no layer 7 inspection, they won't have any effect. it's like assigning security profiles to a deny policy (only it's being allowed).
Just to confirm, given the fact we are using an Application override, means that technically not as secure for these ports since there is no App-ID associated with it, correct?
I believe it's worse than that. You are assigning an app to it, so if someone were to send syslog over 7000 for example, it would become BroadVoice-SIP and be sent to the fastpath. So there's a trickle down effect in that logs would be incorrect, as an example, your security policies may not be applied appropriately depending on their order, etc.
Absolutely the best course of action is always a custom app (without the override policy), but it's also the most challenging (but if it's already been done for you, then run with it). Actually the best course of action would be to submit a request to PA to create an app, but if it's inhouse or a standard app using non-standard ports, they won't be as inclined to to indulge the request.
CCNA Security, PCNSE7
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2017 01:08 PM
So I imagine that your custom application is simply made so that you actually have an application to override *to*. Your custom app-id likely won't actually match the traffic by itself. Take a look at the signatures and maybe attempt to find out if your custom application will actually match traffic or not; if you have an application override policy in place then you likely actually don't have the app-id setup correctly.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-10-2017 01:15 PM
You all typing quicker than l do :0 Yeah my understanding is if you create a custom app, without actually putting any signatures etc, purely based on ports - your traffic will not match as app-id engine will try to identify the traffic and will look not only at the ports.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2017 09:18 AM
Thank folks!
I am getting a better idea of how its working.
There are no signatures configured for this Custom Application.
So I thinking that since an Application override was created this custom Application would not do App-ID processing.
Therefore, this traffic is not identified at Layer 7 and only doing Layer 4 processing.
Sounds like I would need to go through the process of reading traffic and creating signatures for the custom Application if we want it secure at Layer 7.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2017 09:31 AM
Last question(s) on this point. 🙂
Since we have rules that specifiy the source and destination IP addresses specifically for these ports and traffic, would that be our only exposure?
I mean, this path could only be compromised by the source IPs defined, correct? Therefore limiting our exposure if we wanted to live with the Application override (and lack of Layer 7 inspection)?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2017 11:31 AM
yes, your security policy is your first line of defense and will restrict traffic accordingly.
CCNA Security, PCNSE7
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2017 12:54 PM
@OMatlock to add to what @bradk14 said some admins that don't have experiance building application sigantures will use this as a work around, and depending on the security of the application and the subset of devices that are listed in the security policy application override is a perfectly acceptable process.
If I created a custom application for everything our dev team whipped up then I would need at least two other people that were actually capable of creating signatures for everything.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2017 01:15 PM
Thank you for that. I think that is what happened here. Instead of creating a signature, they created an override, which would therefore remove that traffic from App-ID processing.
- 1 accepted solution
- 7559 Views
- 12 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Address Group and Tag limitations in General Topics
- New articles about how to create signatures without or with AI (ChatGPT/OpenAI) in Custom Signatures
- Trendmicro application identified as "ssl" despite of proper SNI, CN, SAN. in General Topics
- Header Fields for Syslog for Rapid7 in Next-Generation Firewall Discussions
- How to specify multiple conditions for the "test custom-signature-perf" command in Custom Signatures