- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Destination NAT translation is not working os .5.0.10
- LIVEcommunity
- Discussions
- General Topics
- Re: Destination NAT translation is not working os .5.0.10
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Destination NAT translation is not working os .5.0.10
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 03:15 AM
Hi Friends,
PAN OS 5.0.10 is running. i have create a destination NAT translation but is not working and also i am not getting any logs. please suggest.
Regards
Satish
- Labels:
-
Configuration
-
Networking
-
Set Up
-
Troubleshooting
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 03:38 AM
Hi Wenar,
Yes, I have already a security policy for that.
Regards
Satish
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 05:24 AM
Can you post a screenshot of the security policy? Keep in mind that your security policy has to look like this:
Source:Any
Source Zone: Any (or Untrust)
Destination: Public IP
Destination Zone: Zone for Private IP
You should see the traffic in the traffic log.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 08:40 AM
Hi Satish,
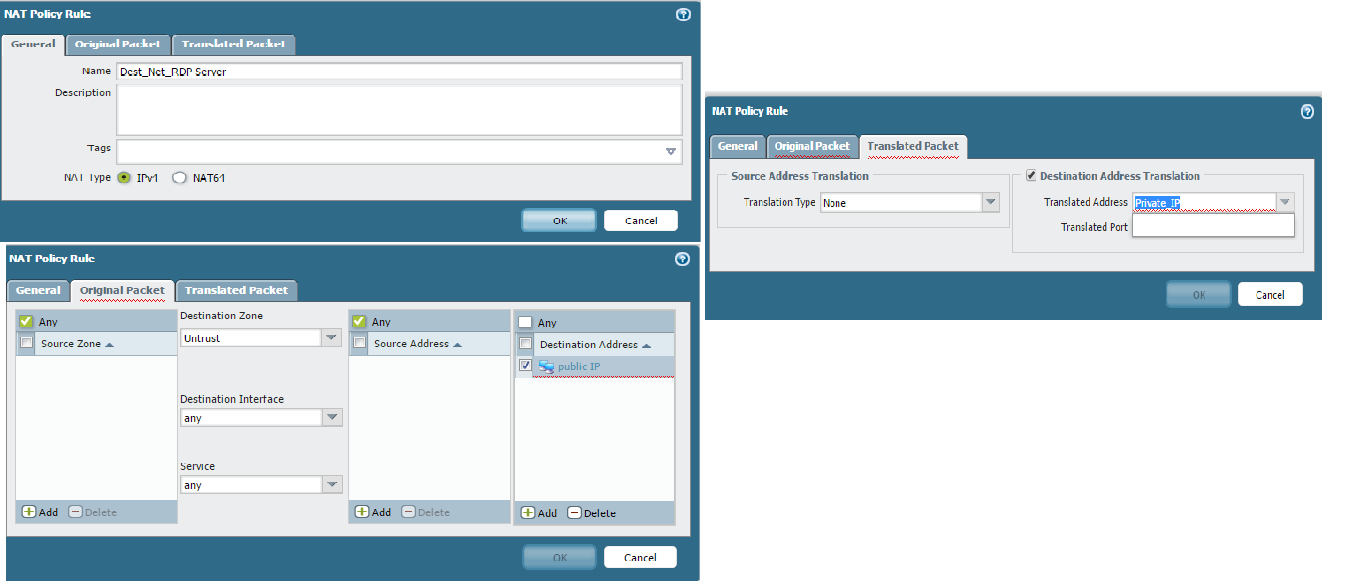
Verify your Security Policy and NAT policy look like what you see below. Make sure that Destination address for your NAT and Security Policy is your Public IP.
Also, for your NAT policy use Source Zone: Untrust, Destination Zone: Untrust. Use only Private IP in your Translated Destination Address.
Security Policy
Nat policy
Regards
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 12:55 PM
Could you confirm if the traffic for that IP address is even reaching the firewall ? Try configuring packet capture and see if the packet is reaching the firewall, if it's not then it should be a simple ARP or routing issue.
Hope it helps !
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-09-2015 02:13 PM
Hurricane electric has a helpful public looking glass utility: Looking Glass - Hurricane Electric (AS6939). They even have an app for the Android ![]() .
.
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2015 05:38 AM
I would start by filtering your policy logs by the source address of the attempt. Then you can see what policy the traffic is hitting in your firewall. Make sure you do have a logging final deny all policy so it is not silently dropped and that logging is enabled for all policies.
Nat columns can be added to the monitor policy logs so you will also see from here if the traffic is being recognized by any of the nat rules.
ACE PanOS 6; ACE PanOS 7; ASE 3.0; PSE 7.0 Foundations & Associate in Platform; Cyber Security; Data Center
- Mark as New
- Subscribe to RSS Feed
- Permalink
01-10-2015 06:13 AM
Just to add something that has not been mentioned... It could be possible that the traffic is indeed reaching the firewall and the NAT itself working properly, but you need to make sure you have a route not only on the firewall to reach the private IP, but also a route configured on the server itself to get back to the outside world through the same firewall interface that was used to forward the incoming packets.
Hope this helps.
- 5328 Views
- 8 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- AWS GWLB with secondary appliance in chain in VM-Series in the Public Cloud
- Policy processing order in General Topics
- Difficulty in Displaying Unused Firewall policies in PA networks using API key in Next-Generation Firewall Discussions
- GlobalProtect prelogon and internal gateway detection in General Topics
- Bi-direction Nat logic in Next-Generation Firewall Discussions



