- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Do I have a split - full tunnel issue
- LIVEcommunity
- Discussions
- General Topics
- Do I have a split - full tunnel issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 02:33 PM
I'm a system admin, and have also become the Network guy. This is okay: it's a small network. I'm still learning.
I have a PA-200, installed by a VAR, in a colocation rack. Rack is filled with windows and linux hosts.
I need to alter the VPN so that when my users in the office connect from their laptops, they can see the systems (ssh, rdp, https) in the rack, while at the same time being able to connect to the office printer, the internet, and so on.
Thanks in Advance,
Brian
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 12:39 PM
Hi Bdunbar,
If access route is 209.49.29.29/32, than GP client will not be able to access anything other than 209.49.29.29/32.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-26-2014 03:08 PM
Hello Brian,
Could you please check the access route configuration in your GP gateway.
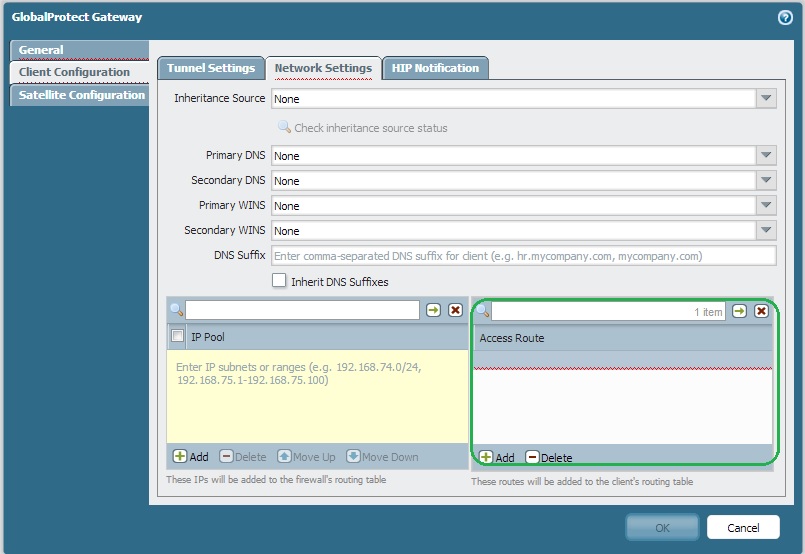
Related discussion: Re: Proper Way to allow Split-tunneling
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-08-2014 03:33 PM
The easy way is use a full tunnel (access route 0.0.0.0/0) and control the access to the host and internet using security policies.
For example
From: specific_users to: DMZ Hosts_needed -> accept
From: All users to: Untrust ANY -> accept.
Also if you need both, you can follow the next guide.
Using Global Protect with One gateway and both split - full tunnel
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-08-2014 05:17 PM
Please check if there are networks defined in access list. If yes, then you need to include the servers, printers ips there.
Important - you also need security policy to allow the traffic.
e.g VPN zone to Trust allow access to <server ip>
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 11:19 AM
Apologies for the delay - I'm a one-man IT department right now.
Access Routes: 209.49.29.29/32
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 12:39 PM
Hi Bdunbar,
If access route is 209.49.29.29/32, than GP client will not be able to access anything other than 209.49.29.29/32.
Regards,
Hardik Shah
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 01:02 PM
Removed that value - and we're good.
I believe, now, that when the client PC logs into the VPN _all_ it's traffic is going to the colocation rack and using their internet. So I still need to set up the split tunnel per the above link.
And next up: the powers that be want to expand our use of the apps and services on the servers in that rack, so 'a client per machine' is now a legacy solution and I need to think about a dedicated VPN tunnel. Joy!
But I feel a lot better about this: thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-17-2014 01:09 PM
Hi Bdunbar,
You can configure all Networks used in COLO in "Access Route".
So Internet traffic will flow through clients Internet circuit. and corporate traffic will flow through VPN tunnel.
Regards,
Hardik Shah
- 1 accepted solution
- 4892 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- GlobalProtect Always-On (6.3.3-c711) – Users Stuck in “Connecting” State but Still Have Internet Access in General Topics
- stream timeout in General Topics
- DHCP Relay over SDWAN issue in Advanced SD-WAN for NGFW Discussions
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions



