- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Global Protect doesnt connect to any portal after connecting to a client certificate authentication portal
- LIVEcommunity
- Discussions
- General Topics
- Re: Global Protect doesnt connect to any portal after connecting to a client certificate authentication portal
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Global Protect doesnt connect to any portal after connecting to a client certificate authentication portal
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-15-2022 02:13 PM - edited 07-15-2022 05:33 PM
There's portal A without client certificate auth
There's portal B with client certificate auth,
when i do the following:
Successfully connect to portal A,
Successfully connect to portal B, select a certificate and all of that,
Now im no longer allowed to connect to portal A, or any other portal thats password based, only to portal B.
(The only way to fix this, is to reinstall globalprotect client, and then its the same, but its very tedious)
The error that global protect gives is just that the certificate is not signed by a trusted certifying authority and it doesnt allow to install it.
How could this issue be fixed?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-15-2022 07:56 PM
- Are requiring user login and certificate or just certificate at the portal stage (Portals->Authentication->Client Authentication)?
- On portal B, are you sending Trusted Root CAs to the client (Portals->Agent->Trusted Root CA)?
- On portal B, are you sending client certificates to the client (Portals->Agent->[config]->Authentication)?
- If, after logging in to/out of portal B, no longer able to log into portal A. If you point your browser at portal A, do you get a certificate error?
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-16-2022 02:56 PM - edited 07-16-2022 03:36 PM
I cannot give any details about portal B since we're only providers for such client, portal A is the one we're responsible for, and where i could dig more details if needed,
But yes after connecting to portal B the browser gives certificate error on the portal A website, i had the guess that maybe portal B somehow was deleting portal A certificate or changing the default certificate folder, but after manually installing the portal A certificate in the trusted root certificate folder it was still giving me errors.
this is the pangps log file after the portal B connection trying to connect to portal A:
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-20-2022 10:16 AM
Are your portals using third-party signed certificates or internal CA signed certificates? It is hard to tell from the description, and not having access to portal B complicates diagnosing, but it sounds like whatever portal B is doing is breaking the certificate chain for portal A. The most obvious thing I can think of is that you are using internal CA signed certificates for your portals and portal B is pushing a new root/intermediate ca certificate that replaces the CA signing portal A's certificate, causing portal A to no longer validate. Replacing with a different CA would also break the browser from accessing/showing a secure connection.
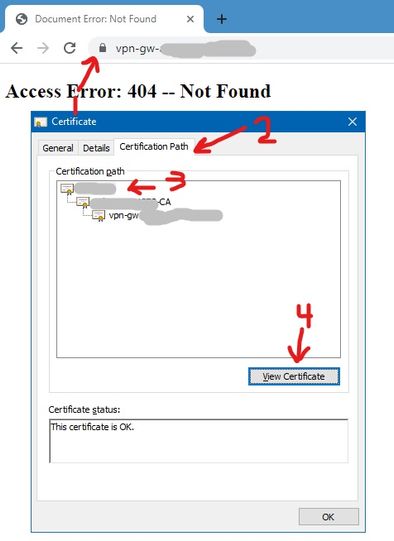
If you fix the PC so you can sign into portal A again.... Point a browser at portal A and then look at the certificate details. Specifically look at the certificate chain and the details of the CA certs used sign it. (Below I show my gateway address in the browser, which gives a 404 error - but the important part is the SSL certificate, not the page. The portal page will give something similar.)
Then compare the above CA certificate details on portal A to the details of the CA certificate on portal B. When the GP client works on portal A, can a browser successfully connect to portal B and does the SSL cert verify?
- 2651 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- RADIUS flows for Authenticating GP with username, password and OTP in GlobalProtect Discussions
- Packaging Global Protect in GlobalProtect Discussions
- CIE agent not connecting to AD servers in Cloud Identity Engine Discussions
- VPN Gateway fails to authenticate clients with new certificate uploaded in General Topics
- Azure Virtual Desktops integration with Global Protect nightmare in GlobalProtect Discussions