- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
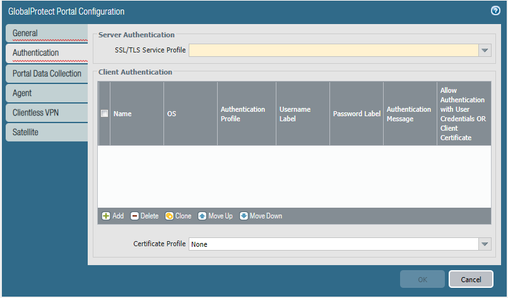
GlobalProtect Portal - No certificate profile configured, but prompt for certificate
- LIVEcommunity
- Discussions
- General Topics
- Re: GlobalProtect Portal - No certificate profile configured, but prompt for certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
GlobalProtect Portal - No certificate profile configured, but prompt for certificate
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 01:13 AM
Hi Community,
I got a strange problem and want to hear, if someone got the same.
We got a Panorama managed PA-3220 PAN-OS 8.1.7 with GlobalProtect portal, external gateway (which share the same IP) and an internal gateway.
The external gateway got a certificate profile defined, the portal not.
If I open the Webpage, the Portal prompts for a certificate - the same does the GP-client (4.1.12).
I cannot find any issues in the KB or release notes.
A colleague of mine experienced a similar issue and deleted the portal & gateways and configured that new - then it worked.
The configuration looks good (checked with AutoAssistant and XML-configs).
Looking forward to your feedback.
Best Regards
Chacko
Chacko
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 07:22 AM
Well, as a 7 year instructor, the requirement (not recommendation) is that the portal NEEDS to have a certificate (preferably publically signed).
The field below (in yellow) is a REQURED field. Not sure how you are programing a portal without a certificate profile.
It should be the same SSL/TLS profile that is being used by the Gateway.
- Create the interfaces (and zones) for the firewall interface where you plan to configure the portal. See Create Interfaces and Zones for GlobalProtect.
- Set up the portal server certificate, gateway server certificate, SSL/TLS service profiles, and, optionally, any client certificates to deploy to end users to enable SSL/TLS connections for the GlobalProtect™ services. See Enable SSL Between GlobalProtect Components.
- Define the optional authentication profiles and certificate profiles that the portal can use to authenticate GlobalProtect users. See Authentication.
Please feel free to respond back to better clarify what you are trying to do.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 07:57 AM
@S.Cantwell: I agree, but I really mean the certificate profile, not the tls service profile.
Chacko
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 09:20 AM
Howdy again!
I think we (who are reading these messages) are getting just superficial info. We need more details about your configuration setup. I am an instructor who teaches and does PS for my company, so I am pretty familiar with the setup.
Is this a new configuration, or something broke?
Are you doing client certificates for authentication? This would be one reason why a request for a cert (probably machine cert would be requested. Do you have "on-demand" or (always-on) in your configuration for your user.
Thanks.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2019 09:34 AM
It's a new installation.
public portal requires an authentication sequence (primary kerberos, secondary ldap) and got two configs:
1st config is user logon (always on) for only a ldap group "vpn-users" and deploys the internal gateway for SSO and the external gateway. 2nd is user logon (always on) for everyone else, which deploys only the internal gateway for user id information.
The external gateway requires a user certificate and ldap for authentication.
The internal gateway got an auth sequence (primary kerberos, secondary ldap).
This setup is my default and works fine with several customers, so I'm confused, why the portal is prompting for a certificate, because no certificate profile is required for the portal.
I already opened up a case with TAC, but I'm interested in this now, and want to understand the issue and find a solution.
AutoAssitant does not see any issues regarding configuration.
Two strange bevahiors:
1. clients get promptet for user cert when accessing portal (doesn't matter if web-portal or GP client).
2. After connecting to portal, the FW logs a failed kerberos auth for user '' but, there is no Kerberos traffic sent from the client. The GP client logs match this and show a failed authentication for ___empty-user____
Everything except for Kerberos SSO (the reason I raised the TAC case) with credential provider worked fine, the both issues occured first, after changing the Kerberos config.
I noticed, that we use two SPNs, but had only one Auth-Profile for Kerberos - I missed to export a second keytab with the 2nd SPN.
AD looks fine, both SPNs are matched to the Palo service user, and the keytabs are looking good and where imported succesfully to the config.
1st auth profile Kerb-Ext-GW shows SPN "vpn.company.com" in keytab while 2nd auth profile Kerb-Int-GW shows SPN "gpgw.internal.local" as SPN
Already rebooted the firewalls and reinstalled the GP clients, but the behavior is persistent
Chacko
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-16-2021 07:59 AM - edited 09-16-2021 08:00 AM
I am having the same problem but actually originated in different way.
I enabled and disabled the function (for testing purpouses) several times until, even if "Certificate Profile" is set no none, it still requires some undetermined sertificate from the VPN clients. I am forced now to leave it on to let people connect.
Luckily, it happened 3 days before the live of the feature.
In means though that I cannot disable the request for client certificates if I need to. I don't like it at all...
- 9650 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- web file blocking in Next-Generation Firewall Discussions
- RADIUS flows for Authenticating GP with username, password and OTP in GlobalProtect Discussions
- High Data Plane Utilization During Business Hours in Next-Generation Firewall Discussions
- Trendmicro application identified as "ssl" despite of proper SNI, CN, SAN. in General Topics
- license.api.paloaltonetworks.com returned with HTTP response code : 404 in General Topics