- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
GP Authentication issues with Symantec VIP
- LIVEcommunity
- Discussions
- General Topics
- Re: GP Authentication issues with Symantec VIP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
GP Authentication issues with Symantec VIP
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-05-2021 07:03 AM
Hi,
We are running Palo Alto Global Protect with Symantec VIP MFA. We have run this for quite some time now and it has been stable until recently.
We are seeing random errors appearing on one of the validation servers. It seems Palo is sending the request but Symantec is dropping it. A restart of the validation service on VIP EG fix the issue temporarily but it appears atleast once a day everyday.
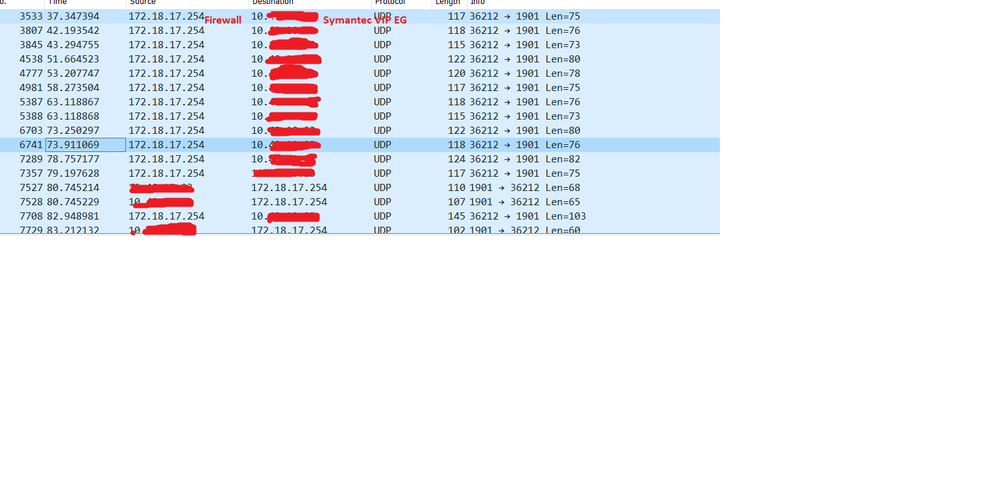
I have taken a wireshark capture when the error was happening. You can clearly see the firewall making the request with no response from the server and from packet 7527, this is where i restarted the validation service on Syamentec running on the port you can see response going to the firewall.
Understand this looks more like a Symantec issue but the change was made on the firewall which triggered these errors. On Palo i have started using Authentication sequence which goes through 3 profiles. 2 X LDAP and last one Radius. 1 x LDAP is not in use and i will be deleting that.
The radius one has been recently added using Okta MFA. Surprisingly when i remove the profile from the sequence on Palo no errors are seen on Symantec VIP MFA server. I have tested this a number of times now at the cost of some operational impact :(. No other way to reproduce the error. Ignore my feeble attempts to mask the IP.
SYMANTEC LOGs:
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2021 06:14 AM
Is the RADIUS profile going to Symantec VIP and then to OKTA MFA (please provide info how the RADIUS works and if you are making the SYMANTEC VIP to talk with OKTA ask Symantec if this is possible at all)? Why not directly integrate Okta MFA without RADIUS as this is supported by palo alto?
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2021 07:04 AM
are independent. I have the sequence like below:
Symantec Radius on port 1901
Symantec Radius on port 19xx (for a different user group. this isnt being
used)
Okta Radius
I have also selected the option where it picks the authentication profile
using domain when a user enters their username. So the request doesnt have
to go through options first second and then third. It goes straight to 3 as
here is where the user puts his mail as his username and i can see Palo go
straight to Okta. So then it becomes completely bewildering if the request
doesnt even go to Symantec and it gets stuck.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2021 03:03 PM
My suggestion is to try the Okta MFA without RADIUS as it is supported by Palo Alto and test and say if the issue is still there.
- 5015 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- SilverFort compatibility with Panorama VM-Series in General Topics
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions
- Issues GP in Iphones in General Topics
- User-ID Integration with AD Failing (Access Denied / Kerberos Errors – Event ID 10036) in Next-Generation Firewall Discussions
- Could you please tell me about the Embedded Browser Framework Upgrade, an enhancement of GlobalProtect version 6.3? in Prisma Access Discussions