- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to configure dynamic NAT IPs
- LIVEcommunity
- Discussions
- General Topics
- Re: How to configure dynamic NAT IPs
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
How to configure dynamic NAT IPs
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2018 07:39 AM
I have a german ADSL connection and would like to make it accessible from outside. My server has internally the IP 10.0.109.111. From outside it is accessible via a DynDNS name because the public IP changes daily.
My router has the 192.168.4.1 IP and the PA 200 on the eth3 has the IP 192.168.4.2. From within the Internet I can also access this IP.
How do I set NAT policies to get from external to internal?
Look my policies...
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2018 08:03 AM - edited 06-07-2018 08:05 AM
I understand that this dynamic public IP is assigned to wan interface of the router. In this case you first need to set up port forwarning on router and then on Palo.
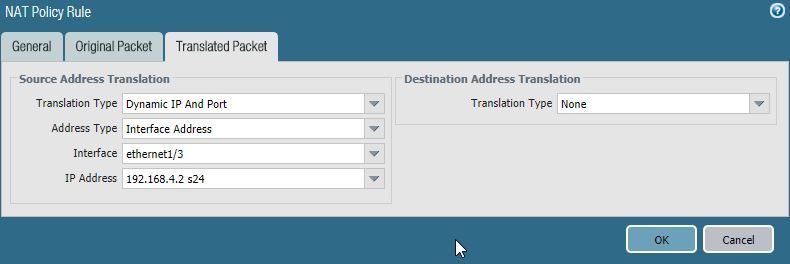
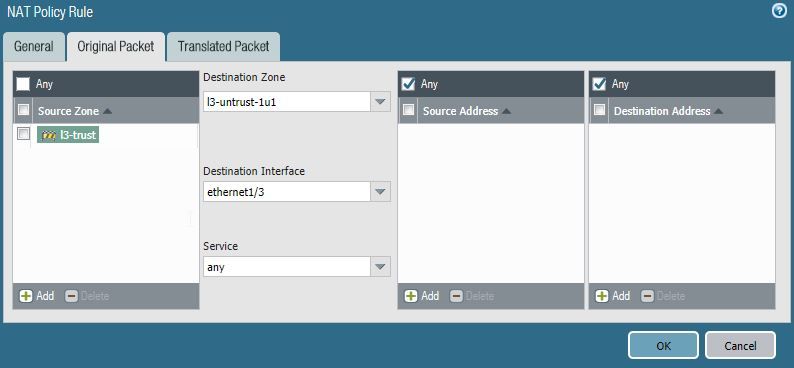
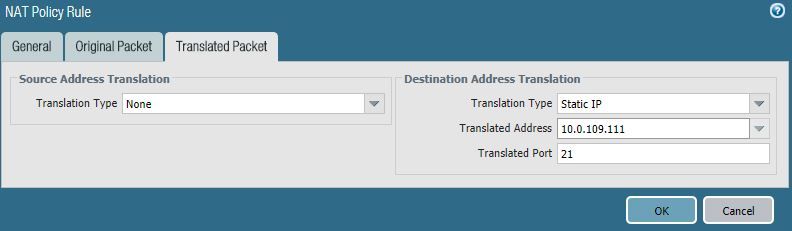
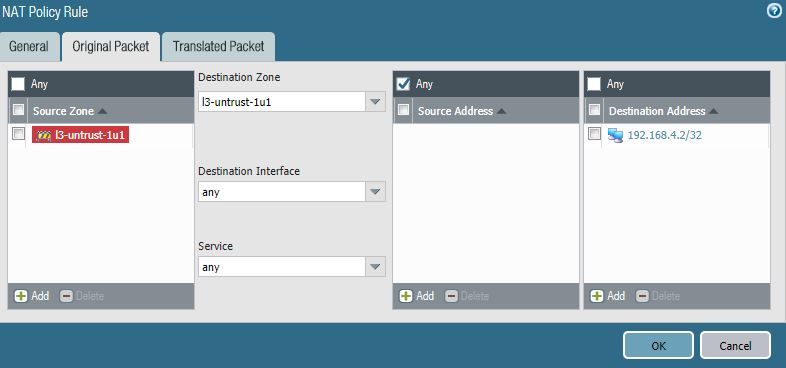
In this case Palo NAT rule looks like this.
Original Packet tab
Source zone - l3-untrust-1u1
Destination zone - l3-untrust-1u1
Destination interface - any will do the trick
Destination Address - 192.168.4.2
Translated Packet tab
Translation Type - Static IP
Translated Address - 10.0.109.111
Security policy
Source zone - l3-untrust-1u1
Destination zone - l3-trust
Source IP - any
Destination IP - 192.168.4.2
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-07-2018 01:56 PM
Hello,
In addition to this I would recommned not using clear text protocols such as FTP. There are free SFTP servers out there that you can use and would make your systems more secure.
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-08-2018 07:39 AM
@Raido_Rattameisterthaht it was.. Destination interface - any will do the trick
@OtakarKlierI know ftp is bad.. but i think its an easy way to test connections. So i have a test server and can connect from outside to this one.
- 2925 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Panorama API - get content of dynamic address group in Panorama Discussions
- HA GlobalProtect firewalls in Azure in VM-Series in the Public Cloud
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions
- Newly Registered Domains configuration in General Topics
- Defining a Known User Object List for Automated Playbook Logic in XSOAR in Cortex XSOAR Discussions