- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to create IPSec VPN tunnel between two Palo Alto 200 firewalls?
- LIVEcommunity
- Discussions
- General Topics
- Re: How to create IPSec VPN tunnel between two Palo Alto 200 firewalls?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-28-2017 12:51 PM
Hi folks,
I went and bought another used PA 200 from Ebay to go along with my existing one to test my first IPSec VPN connection.
Neither have a support or threat license at all and not registered.
PA 200 #1 has PANOS 7.0.5-H2 and PA 200 #2 has PANOS 7.1.9.
I am using PA administrator's guides and other material to create an IPSec Tunnel, but still RED for me so far.
I am using the same IKE crypto and IPSec Crypto settings (default and custom). Double checked Peer and local ip address. Tried with and without proxy ID, tried with and without NAT traversal, with and without Local/Peer identification (IP address), but still RED. Created respective Tunnel interfaces and included a static route for the remote subnet in each virtual router.
I created a separate respective VPN zone for each and security rule to allow any access both ways to my Trust-L3 zone. Do I need to set anything for Untrust-L3?
I am able to ping each others respective external IP from each firewall (static IPs assigned to me from ISP in the same subnet).
Posting this in case anyone sees something obvious that I may be missing?
Does the PANOS have to be the same or licensed?
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2017 06:25 AM
Thank you. Using the test vpn command for ike and ipsec tunnel, and everything is green now on both sides for IPsec and IKE!
However, I am not able to ping or communicate with the internal subnets on the other side, even though I've input static routes respectively.
Working on this now. 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2017 06:41 AM
Check traffic log Monitor > Traffic.
Add Ingress/Egress interface columns and check if traffic is sent towards tunnel interface and is permitted.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2017 07:07 AM
Yep, looks like I did not have my security rule proper. I just changed my one rule to source and destination to include my IPSecVPN zone and Trust interfaces only. I removed reference to Untrust, which is consistent with how our IPSec tunnels are configured at my job, but not consistent with the youtube video referenced earlier.
I am still pondering how it works in my test and at work without a VPN zone permission to Untrust directly. I have the Trust zone permission to Untrust of course for my internet access. My tunnel interfaces that I static route to are members of my IPSecVPN zone, as recommended. I will have to post my configuration and accept solutions to end this thread.
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-01-2017 07:16 AM
It is bad-bad practice to place VPN into untrust zone. VPN has always have to have dedicated zone. I don't know why so many documentations suggest to place VPN into untrust zone.
Palo Alto Networks certified from 2011
- Mark as New
- Subscribe to RSS Feed
- Permalink
09-04-2017 06:38 AM
Thanks folks for all the feedback. I now understand better and can see where I was confused a lot.
First, I did not understand that I was in the context of the management interface using SSH when I was unable to ping my public IP and needed a gateway entry there. Which is totally separate and unrelated to the IPSec tunnel being up or down. I needed to run the test vpn commands to generate the interesting traffic. You guys were trying to tell me that, and I was not getting it yet.
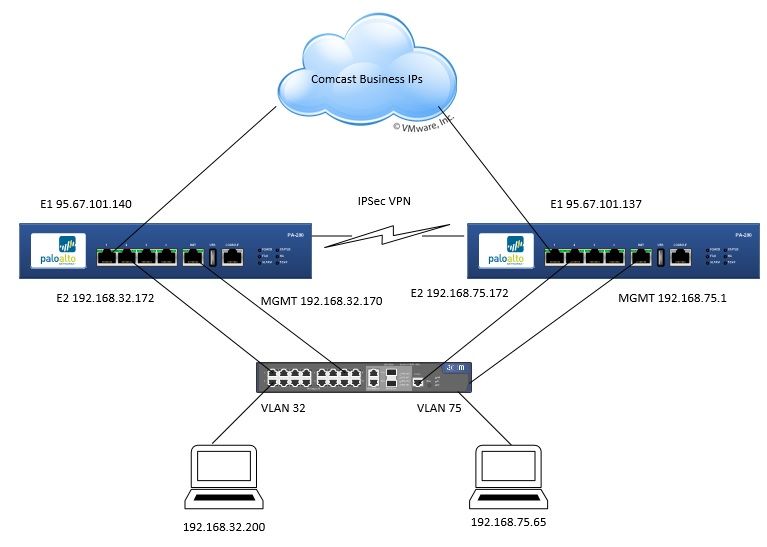
I am attaching my diagram for now and close this thread. I may come back and attach my firewall config.
- 15138 Views
- 19 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Problem with downloading PAN OS in General Topics
- Tunnel Monitoring in Next-Generation Firewall Discussions
- Need quote for Firewall PA 440 in Next-Generation Firewall Discussions
- HA GlobalProtect firewalls in Azure in VM-Series in the Public Cloud
- Inquiry Regarding Publishing Custom Third-Party IOC Feed via EDL Hosting Service in Next-Generation Firewall Discussions