- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to force GlobalProtect user to always connect to portal
- LIVEcommunity
- Discussions
- General Topics
- How to force GlobalProtect user to always connect to portal
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
How to force GlobalProtect user to always connect to portal
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-17-2020 11:37 PM
Hi Guys,
For couple of reasons, recently I started to think - Is there a way to force the users to always connect to the GP portal first and don't use saved gateway config?
I have noticed that we have lots of users connecting straight to the GP gateway and haven't been connected to GP Portal for days. I am trying to figure out a way to force the users to always connect to portal first, get the latest config and after that to connect to gateway, and I am not able think of anything.
I will appreciate any ideas!
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-18-2020 01:54 AM
Hi Alexander,
Did you make sure to disable your portal/gateway cookie authentication?
Network > GlobalProtect > Portals > Portal Profile (your profile name) > Agent tab > Agent config > Disable "Generate cookie for authentication override" or set the timer to 8 hours or so
Once the users authenticates to the Portal it should pull the new gpconfig file and use that to connect to the Gateway
Let me know if you have this setup already?
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-18-2020 04:35 AM
Hi @Sarc845 ,
Thank you for the suggestion, but it doesn't seems to be related to the auth cookie...
Yes we do use auth cookie, but from the below log (all of the logs are related to one user - my filter is "description contains 'name: <user>'") you can see:
- that first agant is trying to authenticate with the cookie, but it has already expired.
- So the gp agent will follow the authentication process (the authentication profile) configured under GP portal:
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-19-2020 09:14 PM
What's the reason to try and force them to connect to the Portal at every connection? They'll already be doing an app config refresh at a whatever interval you've configured, and if the cached gateway can't be connected they'll go back through the complete authentication process.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-20-2020 09:30 AM
Hey @BPry ,
We recently switched allow agent upgrade from disallow to allow transparently, meanwhile the config refresh is set to four hours. I was looking at the logs to see how many users have already been upgraded and noticed that lots of users are still not upgraded, because they haven't updated their config from the portal.
I was looking at some logs and I am staring to believe that the timer for the config refresh is restarted on each reconnect. A user connects directly the gateway in the morning, after few hours (less then four) it has reconnect (laptop sleep or wifi switch or something similar) again directly to the gateway. And this could happend one or twice a day and that way user will never reach the config refresh interval.
I actually noticed few users still using 4.1 version and looking at the logs for one of them it seems because he haven't contacted the portal for the last few months.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-21-2020 03:42 PM
I would look at your PanGPS.log and see if your agents are actually communicating to the portal or not. You don't have to have an authentication event on the portal for the agent to actually be refreshing the configuration. To the best of my knowledge you can't disable the configuration refresh outright, so if you aren't seeing that communication something is broke.
You should be seeing periodic msg type = refresh-configuration in the logs according to your configured configuration refresh interval anytime your agent is connected to the gateway. You don't necessarily see an authentication event with update. The downside to you being on a release pre-9.1 is that GlobalProtect logging on the firewall leaves a bit to be desired, like the portal-getconfig events.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-23-2020 04:05 AM
Hey @BPry ,
GlobalProtect logs are the main reason I want to upgrade to 9.1, but we were not sure if it stable enough yet.
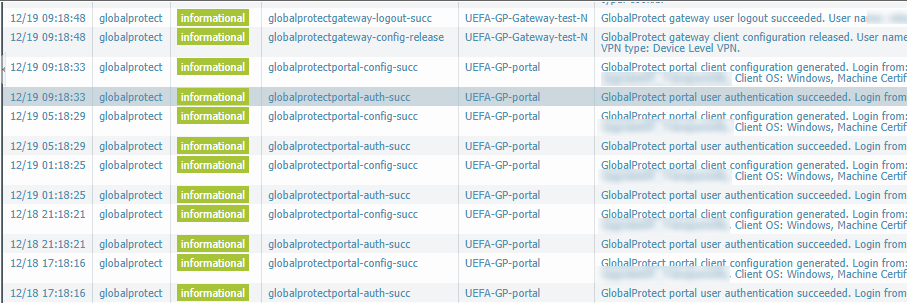
I am interested in what you say - "You don't necessarily see an authentication event with update". So far from the firewall logs I see actually the oposite. See below screenshot. These are system logs filtered with "(description contains '<username>') or (description contains '<user-public-ip>') , showing connected user that is updating its portal config every four hours (as per portal config).
These are logs from user that has been already upgraded to 5.1, I just wanted to point out that from all the logs I have seen so far every portal config refresh is led by portal authentication (in this case with auth cookie, that is why no logs from auth profile).
Going back to the users that are refusing to upgrade - I started looking at the PanGPS logs and something very strange got my attention - there is a entry saying "--Set state to OnDemand mode." . Our configuration is Pre-logon (Always On) and I can see in the registy the connection method is set to pre-logon. However at this exact moment the machine is online, but no GP was connection attempt was on 10th.
- Mark as New
- Subscribe to RSS Feed
- Permalink
12-24-2020 09:14 PM
Interesting. That could simply be that you're using cookie authentication where my deployments authenticate via certificate. I've got far more refresh-configuration events than I do authentication attempts on the portal via my firewall logs.
As for the state issue on the old 4.1 clients, I don't think that's really worth putting a lost of investigation into. The release of 4.1 that you have displayed in your logs is extremely old, and 4.1 is EoL. You'll need to have these users manually upgrade if they aren't contacting the portal to grab the new configuration that allows transparent updates and get them on a current version.
- 12183 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- PA Global Protect in GlobalProtect Discussions
- How to Patch Vulnerability - Plugin 43160 (CGI Generic SQL Injection) on GlobalProtect in Next-Generation Firewall Discussions
- Global Protect - Connection Issue in GlobalProtect Discussions
- [SOLVED] - NGFW The Connection To Global Protect On The IPads Times Out!! in GlobalProtect Discussions
- [Let me know reason & workaround] Global Protect Agent ver6.3.3 “PanPUAC_xxx.dat” does not work (auto create or renew, failed to open). in GlobalProtect Discussions