- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to Implement Certificates Issued from Microsoft Certificate Services?
- LIVEcommunity
- Discussions
- General Topics
- Re: How to Implement Certificates Issued from Microsoft Certificate Services?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-05-2017 02:53 PM
Hi folks,
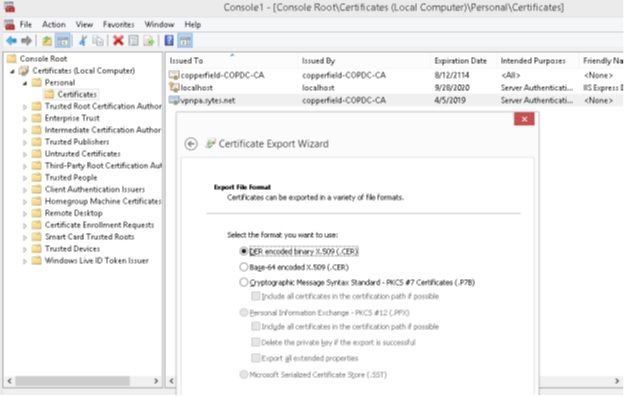
I am starting my journey to configure Global Protect VPN. First I am trying to create/install a SSL certificate from my internal Microsoft CA. I see articles for subordinate, but I do not have that. Just a stand alone Microsoft CA.
This article indicates that I need to eventually export the certificate (after submitting csr to CA and downloading) in .pfx format to then convert to .pem format, before installing on the Palo Alto.
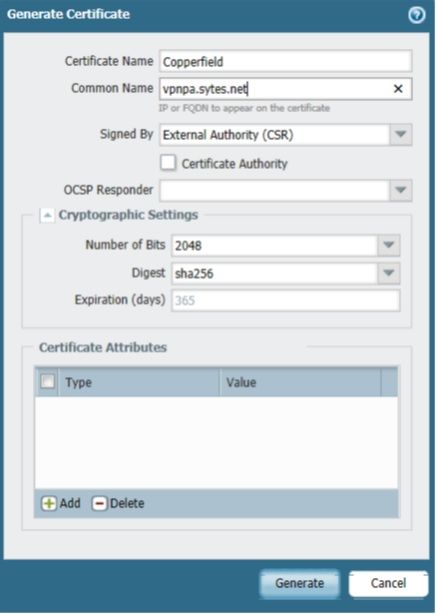
I've generated the CSR on my PA 200 and submitted to my CA, but do not have the options to export the private key and save in .pfx format. I've attached my process. Anyone have suggestions?
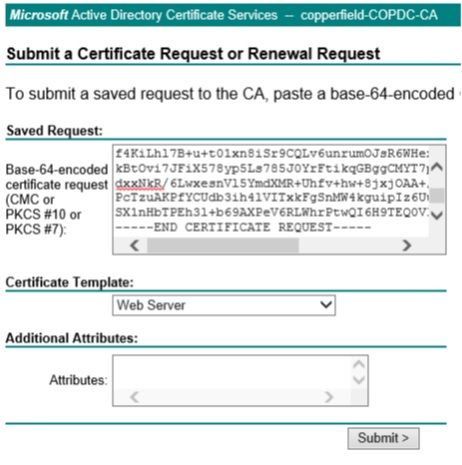
Pasted to Microsoft CA using Web Server template.
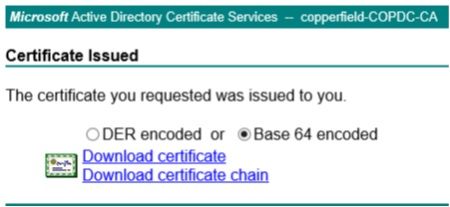
Download certificate chain.
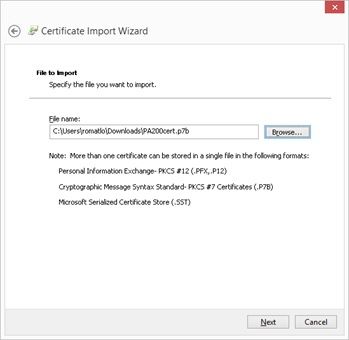
Import .p7b to a sample Windows server so that I may then export immediately after as .pfx.
After import, export immediately to .pfx. But not able, greyed out.
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2017 06:59 AM
I guess I will try a self signed certificate for now and try again later. Thanks again for the responses.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-05-2017 07:27 PM
Hi OMatlock,
Why are you creating sub-CA? You can just create a simple CSR on the PA, export it, get it signed by your Microsft CA. Then, download that signed certificate in Base64 format. Import it on the firewall (use the same name as in the CSR). Create a SSL/TLS profile and use this certificate in it and select this SSL/TLS profile in the portal and gateway.
I am not sure about the steps you mentioned, they seem unnecessary. Sub-CA can be useful for decryption or you can create more certificates signed by that sub-CA (but why?).
Regards,
Anurag
ACE 7.0, 8.0, PCNSE 7
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2017 02:48 AM - edited 04-06-2017 02:49 AM
heavily agree. the subordinate CA certificate is only of benefit if you are performing SSL decryption and using it as your forward trust/untrust cert, not for global protect.
all you need to do is generate the CSR on the PA, approve it on your CA, then import the resulting signed certificate into your PA (under the same name).
but I also need to point out that it really appears that you didn't even follow the link you offered which could only add to the confusion. that link you used shows how to do _everything_ on the CA itself, there's no CSR being generated on the Palo Alto in that case, so handling the private and public keys is very different (as generating the CSR means the private key is already on the device, so you just need the cert from the CA).
CCNA Security, PCNSE7
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2017 07:25 AM
Thanks for the feedback. I am not using or configuring a Sub-CA. The article I am referencing is based on a Sub-CA since I did not find an article that is just a stand alone CA.
Like you say, I am just generating the CSR, signing it, downloading the certificate chain (.p7b), then trying to convert it to .pfx, then .pem.
Is it not necessary to convert it to .pem format? Maybe I am not doing something right. I will review again today and see if I can get it working.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-06-2017 07:30 AM - edited 04-06-2017 07:31 AM
it needs to be in PEM format, but that's what the CA will give you as a response. as I mentioned, when you create the CSR on the Palo Alto itself, it already has the private key, so you don't need to obtain it and combine it, just import the signed PEM file from the CA. there is no conversion process necessary and you shouldn't even have the private key to create the pfx.
I gave you a link above that explains the process.
CCNA Security, PCNSE7
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2017 12:31 PM
Thanks for the link and feedback. It sounds so easy! 🙂
However, the link really skips over the details of the steps at the CA (Microsoft in my case).
I am following the steps above in my initial screenshots above.
I don't see a way yet to create/download the certificate from the MS CA as .pem format.
I know I must being doing something dumb wrong. If any thoughts, I here. Thanks again.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-11-2017 01:27 PM
unfortunately I have no practical experience with MS CA myself, but the Base64 option should basically equal PEM format
you should get what amounts to a text file that resembles the original CSR, though it's the actual cert.
CCNA Security, PCNSE7
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-13-2017 06:59 AM
I guess I will try a self signed certificate for now and try again later. Thanks again for the responses.
- 1 accepted solution
- 14822 Views
- 7 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Error log ": MLAV Server certificate validation failed. " received in Next-Generation Firewall Discussions
- Evasion Technique - 1244315488 in Cortex XDR Discussions
- "PANDB Cloud Agent Server certificate validation failed. Dest Addr: , Reason: unable to get local issuer certificate" in General Topics
- No "certificate used by" field when generating certs for SSL forward trust and untrust? in General Topics
- service certificate push from panorama to managed firewalls eg: vpn in Panorama Discussions