- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to properly disable 3DES encryption algorithm?
- LIVEcommunity
- Discussions
- General Topics
- How to properly disable 3DES encryption algorithm?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-25-2016 03:27 AM - edited 10-25-2016 03:27 AM
We are currently being required to disable 3DES in order to pass PCI compliance (due to the Sweet32 exploit).
We have a decryption profile for all incoming traffic hitting our firewall and services behind it, where I have tried disabling 3DES.
However, the firewall will still accept 3DES after doing a commit. When opening the decryption profile again. 3DES will be shown as enabled again.
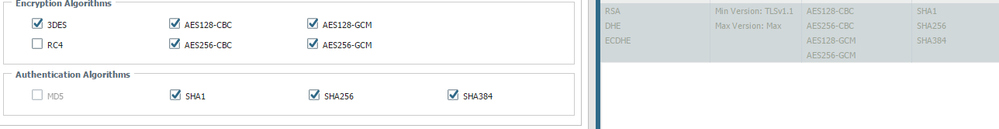
As you can see in the picture, 3DES seems to be disabled in the decryption profile list, but when opening the specified decryption profile it shows up as enabled.
Does anyone know how to properly disable 3DES on PANOS 7.1.x?
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2016 12:40 AM
I finally managed to disable 3DES, but it was not as straight forward as disabling 3DES on the decryption profile for inbound SSL.
To make this work, I set min. protocol version of the decryption profile to TLS 1.2, and then I had to do the same for the SSL/TLS Service Profile for each of the certificates used for inbound SSL inspection.
Now the firewall will only use TLS 1.2 and 3DES is disabled across the board.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-25-2016 03:44 AM - edited 10-25-2016 03:45 AM
Hello,
Seems odd, can you try changing this via the CLI?
>configure
#edit profiles decryption "name of decryption profile" ssl-protocol-settings
#set enc-algo-3des no
#commit
let us know if this resolves the issue.
Ben
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-25-2016 04:20 AM
Hi Ben,
This did not resolve the issue, but it should be disabled.
The firewall still provides TLS_RSA_WITH_3DES_EDE_CBC_SHA for clients.
Here's the output from show of ssl-protocol-settings for the decryption profile:
(active)# show
ssl-protocol-settings {
keyxchg-algo-dhe yes;
keyxchg-algo-ecdhe yes;
min-version tls1-1;
keyxchg-algo-rsa yes;
enc-algo-3des no;
enc-algo-rc4 no;
enc-algo-aes-128-cbc yes;
enc-algo-aes-256-cbc yes;
enc-algo-aes-128-gcm yes;
enc-algo-aes-256-gcm yes;
auth-algo-sha1 yes;
auth-algo-sha256 yes;
auth-algo-sha384 yes;
}
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-25-2016 04:29 AM
Hi,
I see the same thing in my lab (running PAN-OS 7.1.3 on a VM-100).
It might just be a cosmetic bug because the CLI command indicates it is disabled :
admin@PA-VM# show profiles decryption test ssl-protocol-settings
ssl-protocol-settings {
enc-algo-3des no;
enc-algo-rc4 no;
}
I'd recommend to open a bug report with support so they can get this GUI bug fixed.
Cheers,
-Kim.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-25-2016 05:08 AM
Hi,
Yes, the GUI is showing it as disabled, yet the firewall will still offer 3DES to clients, so this is not just a cosmetic issue.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2016 12:37 AM
Kim This command is working on 6.0 ?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-27-2016 12:40 AM
I finally managed to disable 3DES, but it was not as straight forward as disabling 3DES on the decryption profile for inbound SSL.
To make this work, I set min. protocol version of the decryption profile to TLS 1.2, and then I had to do the same for the SSL/TLS Service Profile for each of the certificates used for inbound SSL inspection.
Now the firewall will only use TLS 1.2 and 3DES is disabled across the board.
- 1 accepted solution
- 15628 Views
- 6 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- VPN issues with 3 ISPs in General Topics
- Way to dual-boot MacOS without violating encryption requirements for GlobalProtect? in GlobalProtect Discussions
- Best Practices Question in AIOps for NGFW Discussions
- Issues with phase 1 of ipsec in General Topics
- Bitlocker + Intune + XDR in Cortex XDR Discussions