- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
How to reach the Palo Alto management interface form my internal network
- LIVEcommunity
- Discussions
- General Topics
- Re: How to reach the Palo Alto management interface form my internal network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-18-2020 10:25 AM
Hi,
I'm fairly new to Palo Alto firewalls and just set up a home lab, but I have a problem accessing the management interface from my local network.
I have 4 network devices in my network:
- Modem/Router
- Palo Alto PA-500 (PAN-OS 7.1)
- Cisco 2960 switch
- Cisco 1602 AP
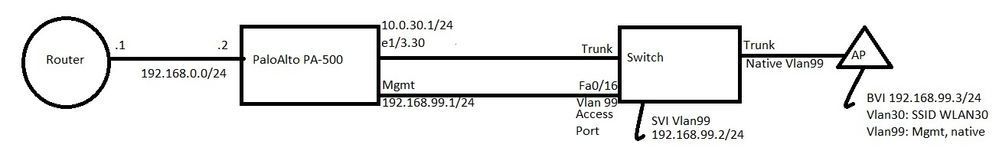
I'll try to explain how everything is connected, but I also added a picture of the topology which probably makes more sense then my explanation.
Router --> Palo Alto --> Switch --> AP
Router --> Palo Alto: 192.168.0.0/24 subnet. Router is .1 and Palo Alto is .2
Palo Alto --> switch: One physical interface on the Palo Alto that has one subinterface (10.0.30.1/24) which is configured as a DHCP server for wireless clients in VLAN 30). The switch side of this connection is configured as a trunk with all VLANS allowed.
The Palo Alto also has a (physical, dedicatec) management interface which has the 192.168.99.1/24 address.
I also connected a cable from the Palo Alto's dedicated management interface to the switch. The switch port is an access port in VLAN99 (management).
Switch --> AP: The switchport is configured as a trunk with all VLANS allowed. The switch has an SVI named VLAN99 with IP address 192.168.99.2
The AP has 3 VLANS: 1 (unused), 30 (for wireless clients), 99 (Management VLAN and also native VLAN).
The BVI interface on the AP is configured with IP address 192.168.99.3
As you probably already guessed, I'd like to use VLAN99 (subnet 192.168.99.0/24) as my management VLAN throughout my network.
Most of the things in my network are working fine. I can connect to the SSID associated with VLAN30, receive an IP address via DHCP and connect to the internet using my "wireless to outside" policy.
However, I'm struggling with setting up the dedicated management interface correctly.
Here's what I want to do: when I connect with my laptop to the SSID associated with VLAN30, I also want to be able to reach the management interface of the Palo Alto. So, packets need to be routed from the subinterface of VLAN30 to the management interface.
This is not what's happening now. In the logs I see that packets from 10.0.30.5 (laptop) to 192.168.99.1 (mgmt interface of palo alto) are hitting the policy "wireless to outside". The mgmt interface address is seen as an outside address.
Can anyone tell me how I can fix this. Maybe I configured my network all wrong, but can someone the please tell me what the best setup would be?
Thanks in advance for your ideas/help.
Steven
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2020 11:52 AM
@decosterstevenThere you go. It will never work if you keep that port in vlan99 as subnet 10.0.30.x is not part of vlan99. You need to keep it as trunk as you have multiple sub-interfaces configured on 1/3.
Mayur
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-18-2020 10:53 AM
Please check below few points -
1. Network Configuration on the PA interface where subnet 192.168.0.0/24. If it is properly configured or there is some mis-configuration in subnet mask as you have management segment in 192.168.x.x.
2. Make sure on Management interface, you have enabled services like 443, ICMP etc to enable these services on MGMT interface. Also see permitted IP Addresses field.
As there is incorrect zone, please verity first point. I am suspecting issue with this. Also check what is gateway configured for MGMT interface and subnet mask.
Mayur
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-18-2020 11:13 AM
Hi Mayur,
Thank you for your reply.
I changed the default subnet of the management interface from 192.168.1.1 to 192.168.99.1/24
As default gateway I used 192.168.0.2, which is the outside interface of my palo alto that connects to my router. I also configured a default static route 0.0.0.0/0 to 192.168.0.1 (my router).
Can the management interface be put in a zone? I tried to configure this, but I cannot select the mgmt interface.
Steven
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-18-2020 11:28 AM
You can't configure security zone on MGMT interface. As you have configure MGMT IP as 192.168.99.1/24, make sure you have also configure proper gateway to this. Also enable services given in my earlier post. Now you should be good to go.
Hope it resolves your issue now!
Mayur
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-18-2020 12:04 PM
Hi Mayur,
I see that I wrote a mistake in my previous post.
I ment that my default gateway under the management settings is 192.168.0.1 (router) and not 192.168.0.2.
So, what you are saying is that the ip address of my management interface should be in the same subnet as that of the link between my router and the palo alto (192.168.0.0/24 in this case) ?
Steven
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-18-2020 12:21 PM
There is confusion here. Let me put everything here,
1. Your default route under Virtual Router should be towards 192.168.0.1
2. Under Management interface settings, configure below points,
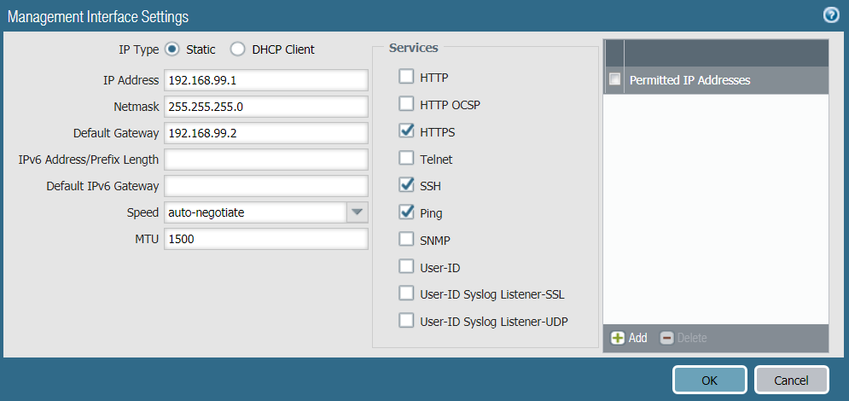
IP Address - 192.168.99.1
Subnet Mask - 255.255.255.0
Default gateway - 192.168.99.2
Here your default route and Default Gateway for Management interface are separate configs and used for separate traffic. Default Route under Virtual Router is applicable for DATA Plane traffc. And Default gateway configured under Management interface settings is used for MGMT Plane or Management interface traffic.
Hope it is clear now!
Mayur
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-18-2020 12:40 PM
Thanks for the explanation Mayur. This was very helpful!
I'll give it a try tomorrow and let you know if it worked.
Steven
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2020 06:55 AM
Hi Mayur,
I think everything is configured now the way you explained it, but I still have some issues.
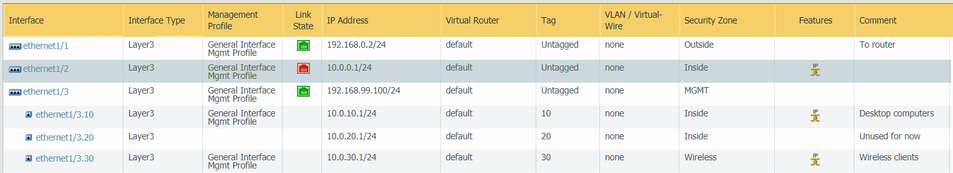
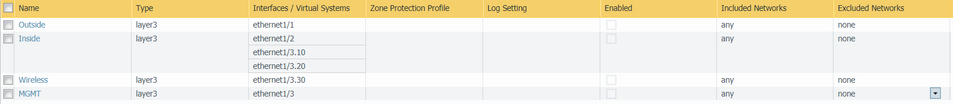
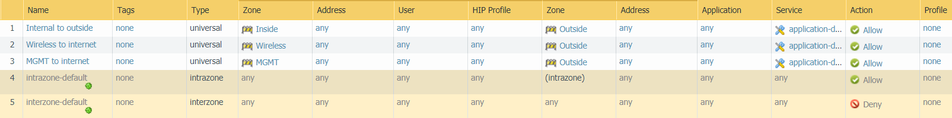
Just to make sure that we are on the same page configuration wise, I'll post some screenshots of the actual config of my Palo Alto:
Interfaces:
Zones:
Security policies:
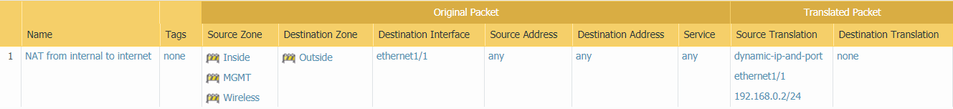
NAT policies:
Management interface (connected to switch):
Also note that my switch is a L2 switch.
From my laptop I can ping 192.168.99.100, but not 192.168.99.1 (palo alto mgmt) and 192.168.99.2 (switch mgmt)
Froom the palo alto, I can ping all devices.
I'm not even sure if this is the correct way to setup a network.
Thanks again for your input.
Steven
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2020 07:12 AM
One last thing I forgot to mention: the default gateway configured on my switch is 192.168.99.100, which is the IP address assigned to the e1/3 main interface of the palo alto.
From the switch I can reach all network devices.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2020 07:48 AM
@decosterstevenWhy are you using same subnet i.e. 192.168.99.x for other interfaces on Palo Alto? Also why IP is configured on Eth1/3 as it is already configured as sub-interface? If you want to forward normal traffic/LAN traffic towards firewall, you can use Eth1/2 and then out default route towards it on switch.
Mayur
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2020 08:44 AM
Hi Mayur,
I configured the 192.168.99.100 address on the main interface of e1/3 because I read this in some article. In this article (I don't remember the source) it was configured like this. I'm using this address as the default gateway on my switch.
If I remove this 192.168.99.100 ip address, what should I use then as default gateway on the switch? I do need a default gateway on the switch, right? I mean, if I want to ping from the switch to an external address it needs to send it to it's default gateway.
Steven
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2020 08:58 AM
Yes, you can use interface 1/2 of PA for this. And use that IP as a default gateway on switch. 1/2 can be act as Inside interface on PA.
Mayur
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2020 09:03 AM
But why interface e1/2 of the palo alto? It is currently not in use. No cable is connected to this port. On the palo alto, I only have a cable connected to port e1/1 (to the router), e1/3 (to the switch) and the mgmt interface (to the switch).
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2020 09:38 AM
I'm not insisting to use 1/2 for LAN traffic. You have used 192.168.99.x on 1/3 which is overlapping with MGMT interface subnet. So Either change this subnet or use 1/2 as your LAN interface.
I think due to this overlapping, when you try to connect to MGMT interface, the traffic is going on interface 1/3 (can you check logs for this). Actually your MGMT traffic should to directly via MGMT connectivity.
Mayur
Check out my YouTube channel - https://www.youtube.com/@NetworkTalks
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2020 10:08 AM
I removed the overlapping ip address from interface e1/3. So, now only the mgmt interface on the palo alto is in the 192.168.99.x subnet.
The problem I'm facing now is that I cannot reach any address on the internet anymore form my switch. This is because it doesn't have a default gateway anymore. What do you propose to use as default gateway on the switch? I tried one of the subinterfaces (10.0.30.1), but that doesn't work either.
I'm really confused.
- 1 accepted solution
- 34562 Views
- 23 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Palo Alto firewall management Interface Home Lab in General Topics
- Unable to reach Palo Alto - Global Protect Portal. in GlobalProtect Discussions
- PAN-OS 10.2.17 HA A/P - Mgt interface reported as duplicate IP of data interface in Next-Generation Firewall Discussions
- Issues with SSH and Telnet access only on the passive firewall. GUI access is working fine. in Next-Generation Firewall Discussions
- Newsletter: Cloud Delivered Security Services, Oct-2025 in Advanced Threat Prevention Discussions