- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
I found message from scan secutity on Palo alto 850 "Insecure Transport: Weak SSL Cipher ( 11285 )"
- LIVEcommunity
- Discussions
- General Topics
- Re: I found message from scan secutity on Palo alto 850 "Insecure Transport: Weak SSL Cipher ( 11285 )"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
I found message from scan secutity on Palo alto 850 "Insecure Transport: Weak SSL Cipher ( 11285 )"
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-21-2021 01:36 AM
Hi All
I found message from scan secutity on Palo alto 850 "Insecure Transport: Weak SSL Cipher ( 11285 )"
I did configuration command like in document. but the message it still show after scan again.
anyone have idea
for SSL/TLS to disable weak Algorithm-
set shared ssl-tls-service-profile web-gui protocol-settings auth-algo-sha1 no
set shared ssl-tls-service-profile web-gui protocol-settings enc-algo-3des no
set shared ssl-tls-service-profile web-gui protocol-settings enc-algo-rc4 no
set shared ssl-tls-service-profile web-gui protocol-settings keyxchg-algo-rsa no
I am reading on document it reccomend to do this anyone can reccomend command
thank you
Disable support for weak ciphers on the server. Weak ciphers are generally defined as:
· Any cipher with key length less than 128 bits
· Export-class cipher suites
· NULL ciphers
· Ciphers that support unauthenticated modes
· Ciphers assessed at security strengths below 112 bits
· All RC4 ciphers
· All CBC mode ciphers due to POODLE, Zombie POODLE, GOLDENDOODLE, 0-Length OpenSSL, and Sleeping POODLE
vulnerabilities
· All 64-bit block ciphers
· All ciphers using MD5 and SHA1 for cryptographic hash functions
The following ciphers supported by the server are weak and should be disabled:
· TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x39)
· TLS_DHE_RSA_WITH_AES_128_CBC_SHA (0x33)
· TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d)
· TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c)
· TLS_RSA_WITH_AES_128_CBC_SHA (0x2f)
· TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014)
· TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013)
- Mark as New
- Subscribe to RSS Feed
- Permalink
08-05-2021 06:52 AM
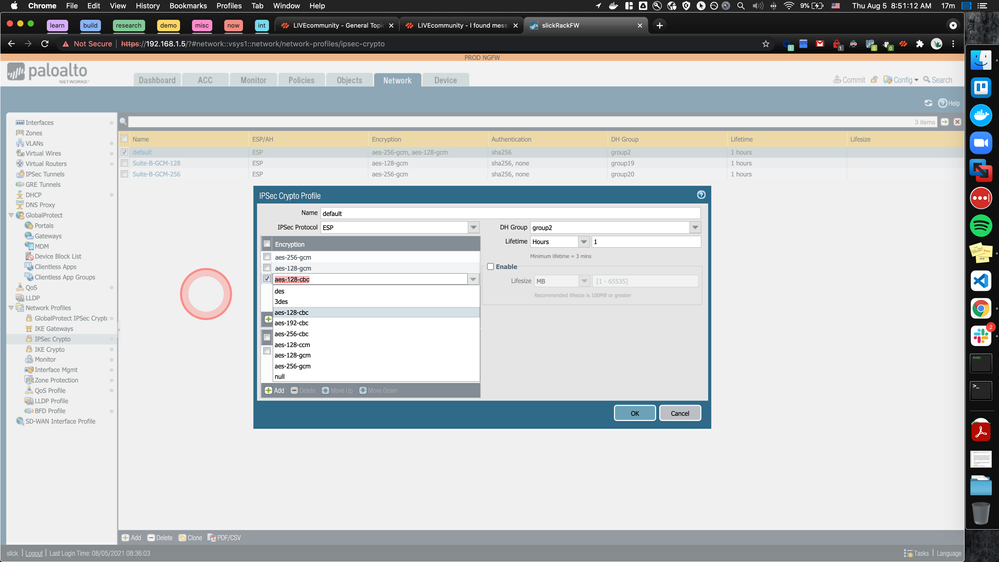
Are you able to confirm in your network tab, under IPSec Crypto profile, that your objects do not include any of the above?
AES-GCM-128 and 256 with SHA256 (in my screenshot) will work.
- 2991 Views
- 1 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- GRPC status UNAVAILABLE in intelligent offload in VM-Series in the Private Cloud
- SDWAN recommendations in Prisma SD-WAN Discussions
- Configure SDWAN with only one transport (FTTH) in General Topics
- Threat ID: 31671 - SCADA ICCP Unauthorized COTP Connection Established in Advanced Threat Prevention Discussions
- Threat ID 31671 - SCADA ICCP Unauthorized COTP Connection Established in Advanced Threat Prevention Discussions