- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IPS - new signature's action set to default instead of the action specified in rule
- LIVEcommunity
- Discussions
- General Topics
- IPS - new signature's action set to default instead of the action specified in rule
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-09-2014 12:48 AM
Hello.
I have a general IPS profile with a rule (named block-crit,high) which includes all signatures with severity 'critical' and 'high'. Action for the rule is set to 'block'. I have automatic updates on for IPS signatures. Yesterday a new signature (OpenSSL SSL/TLS MITM vulnerability) was released with severity critical. When I checked my IPS profile today i noticed that signature was correctly included in above rule (block-crit,high) but the action for this signature was set to 'default (alert)' despite the action for rule being 'block'.
Is this expected behaviour? Are all new signatures set to default action? Can you set new signatures to block?
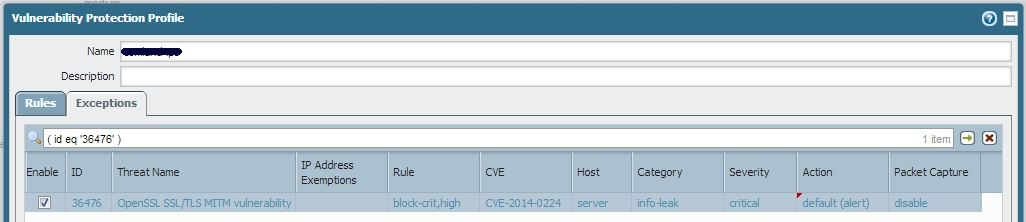
Best regards,
Simon Antonic
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
11-03-2014 06:11 AM
We did some testing and we found out that rule order does matter in IPS profile. So if a signature matches 2 rules, the action will be set by first rule it hits, matching the rules from top to bottom.
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-09-2014 04:11 AM
Hi
According to my knoweladge this is OK IF your "rules" section of this profiles looks like my:
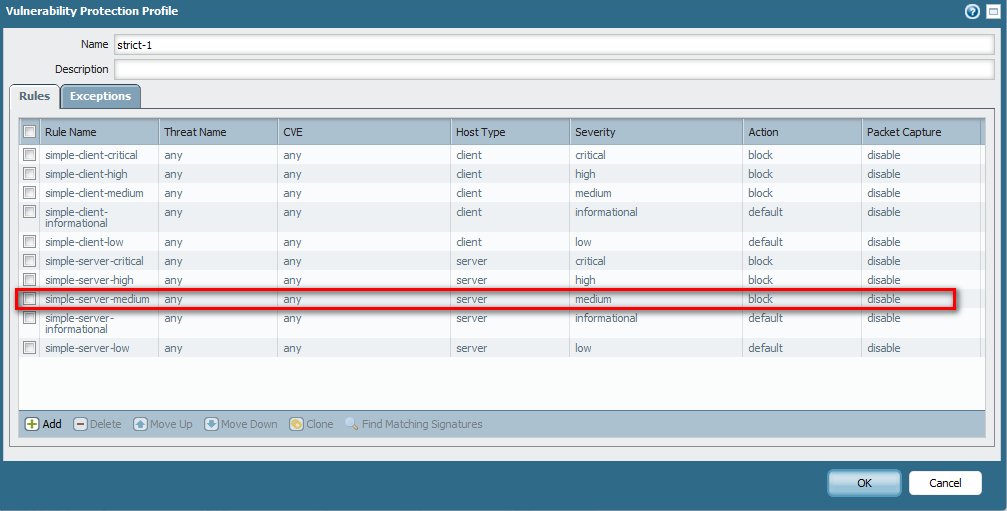
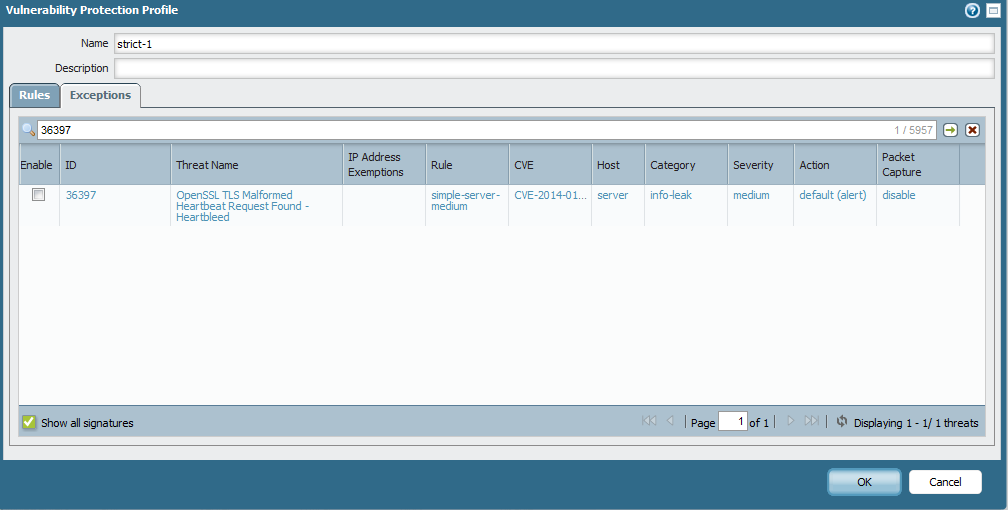
This is example with Heartbleed because is easy to verify ![]()
My thread log have a lot of entries like:
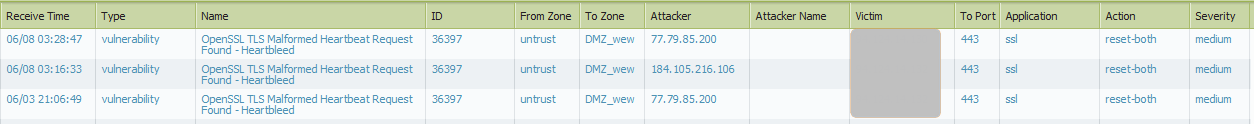
So this is proof that is working.
Regards
SLawek
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-09-2014 06:37 AM
Thank you for your response.
Yep, action in rule is on 'block'. I just wasn't 'lucky' enough to find an event triggered by this signature in logs to verify how it works.
Still a way to check current response for certain signature would be useful.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2014 01:07 AM
Ok, I've come across the same problem again and still haven't found a solution for it.
How do you check what is the set action for certain signature? I couldn't find a CLI command for it and in GUI when you check 'show all signatures' every signature is listed with the default action and not with the action set by rule.
I believe this is a very important feature and I'd really need a way to check set actions for signatures in certain profile. Waiting for an attempt of exploit which would trigger that signature to happen and checking logs afterwards is not an answer.
Am i gettting a 'contact your SE for feature request' answer next? ![]()
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2014 07:20 AM
are you using the built in ips profiles?
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-01-2014 06:41 PM
Santonic,
The action set in the vulnerability Rules are coherent with the default action set with individual signatures. In the exceptions tab, you just add an exception for an individual vulnerability signature and change the action according
to you requirements saying that exempt the action set in the Rule for this signature.
To see the default action set on a vulnerability signature, open the profile and navigate to exceptions tab. Check the show all signatures option which shows all the signatures with the default action associated with them.
Hope this is helpful and not confusing.........:)
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-02-2014 03:57 AM
Hi Simon,
You are right and that is the expected behavior.
When you create a rule and choose the action for that rule to "block" for the severities "critical and high" and have chosen "Any" in the CVE and Vendor-ID column, then any CVE (even CVE whose default action is alert) will be blocked. The vulnerabilities rules and the corresponding action in that rule (for any CVE/Vendor-ID OR for specified CVE/Vendor-ID) take precedence over the default threat ID actions. Again, the rule must be matched correctly for the corresponding action to take place.
You can change the default action for threat IDs. Click the "Exceptions" tab and then click "Show all signatures". Enter the threat ID in the search bar and click on the action to see the dropdown. Now choose the required action and ensure to check the "Enable" box.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-02-2014 04:53 AM
Yes, I understand how it works (I think). The problem is that you can't see neither in GUI nor in CLI what is the current action for certain signature. Yes, you can see the rules, you can see in which rules the signature is included, and you can figure out what the action is.
But there is no view which would list the signature with the current set action, unless you make it an exception.
I know it's only a view missing and not functionality, but it would be really nice to see signature(s) listed with its current action for certain security profile like all the IPS systems have. I'd be happy already with a CLI command to check response, maybe something like "show policy security-profile 'profile_name' AlertID 'ID_number' " and the output is signature name and set action for that profile.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-03-2014 03:52 AM
Hi Simon,
As of now, the options to view the default action is by checking "Show all signatures" in the Exceptions tab. You can also use the following CLI commands to view all the threats and their associated default action.
> configure
# show predefined threats ---> displays all the threats. Use forward slash followed by the threat ID to search for a specific threat ID (/36729)
# show predefined threats vulnerability <threatID>
You may find https://threatvault.paloaltonetworks.com/ to also be helpful as it provides more information Click the magnifying icon to view the default action.
You can contact SE to place any feature requests.
Hope this helps.
Thanks
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-06-2014 12:40 AM
Yes, seeing the default action is easy.
But seeing the current set action for certain signature (in specified profile) is impossible. You can only see in which rule it is included and then check the action for that rule. But I already had customers asking: "ok, show me that this signature is indeed in blocking mode for this profile".
I'll open a feature request. And hopefully some of the readers here will help me with same requests ![]()
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-06-2014 12:53 AM
Please share FR number so that we'll also vote for...
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-06-2014 01:03 AM
Hmmm, another question.
What happens if signature is included in multiple rules with different set actions? Does it work like security policy, top down and first rule that hits?
Example:
rule that sets all critical signatures to default
rule which sets all signatures which have 'bash remote' to block.
What is the response now for signature ID 36729 which is 'critical' severity, includes words 'bash remote' and default action is alert?
In such case the ability to see signature response would come in handy ![]()
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-06-2014 01:07 AM
yes; rules inside profile works from top to bottom.
for the example, it is alert.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10-06-2014 02:55 PM
Rules inside vulnerability profile do not get checked from top to bottom. These rules are defined based on criteria's such as host type and severity.
For example: Threat ID 36729 has following criteria's :
Host type : Server
Severity : Critical
thus it matches the rule highlighted below:
In this case, the action will be block for threat signature 36729.
hshah has given a clear idea as to how the profile gets matched. It depends on which security rule the traffic matches and the profile attached to that rule.
Hope this helps.
Thanks
- 1 accepted solution
- 14304 Views
- 19 replies
- 1 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- New articles about how to create signatures without or with AI (ChatGPT/OpenAI) in Custom Signatures
- Threat Protection Coverage for LockBit 5.0 in General Topics
- DNS req/res does not work with "transaction" scope in Custom Signatures
- Cisco ASA Recent CVE News in Custom Signatures
- Newsletter: Cloud Delivered Security Services, Aug-Sep, 2025 in Advanced WildFire Discussions



