- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
IPSec Tunnel fails after 1 packet
- LIVEcommunity
- Discussions
- General Topics
- Re: IPSec Tunnel fails after 1 packet
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
IPSec Tunnel fails after 1 packet
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-30-2022 02:15 AM
Hi Guys,
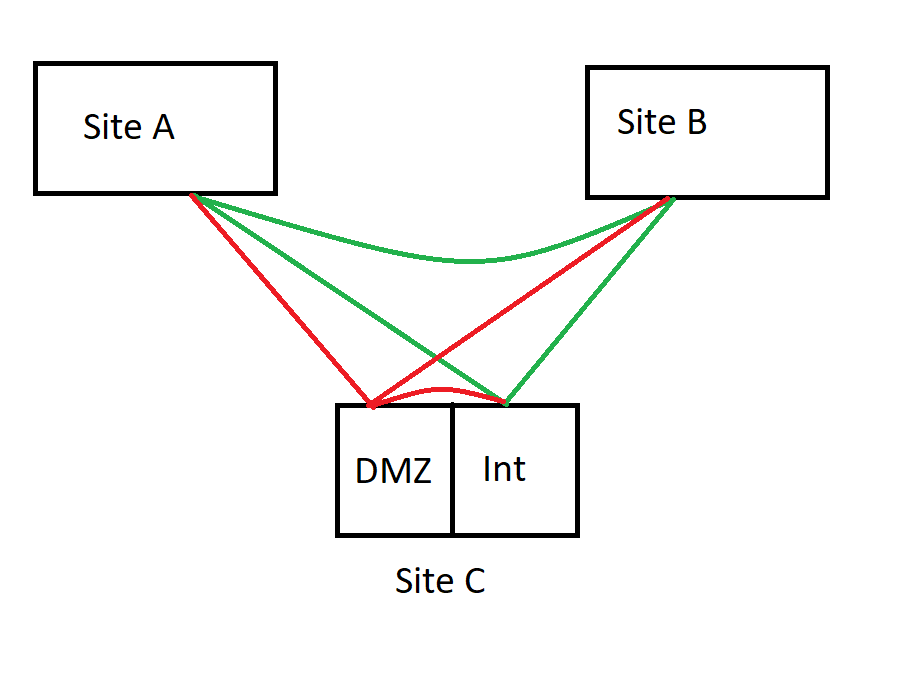
We have a number of Palo Alto firewalls at our satellite sites configured in a Mesh VPN.
Site A, Site B, and Site C (Internal) all work successfully.
Site C DMZ can establish a tunnel to all the other sites, however as soon as the VPN is used, it immediately stops working.
Site C Internal and Site C DMZ are different Virtual Routers running on the same vsys.
Testing the VPN from SiteA to DMZ works
admin@SiteA(active)> test vpn ike-sa gateway DMZ
Start time: Jun.30 16:48:21
Initiate 1 IKE SA.
Sending a ping across the tunnel works for a single packet.
admin@SiteA(active)> ping source 10.1.1.1 host 100.1.1.1
PING 100.1.1.1 (100.1.1.1) from 10.1.1.1 : 56(84) bytes of data.
64 bytes from 100.1.1.1: icmp_seq=1 ttl=64 time=2.09 ms
^C
--- 100.1.1.1 ping statistics ---
5 packets transmitted, 1 received, 80% packet loss, time 4058ms
rtt min/avg/max/mdev = 2.099/2.099/2.099/0.000 ms
Testing another separate ping fails
admin@SiteA(active)> ping source 10.1.1.1 host 100.1.1.1
PING 100.1.1.1 (100.1.1.1) from 10.1.1.1 : 56(84) bytes of data.
^C
--- 100.1.1.1 ping statistics ---
2 packets transmitted, 0 received, 100% packet loss, time 1018ms
Using TEST VPN to reinitiate some keys
admin@SiteA(active)> test vpn ike-sa gateway DMZ
Start time: Jun.30 16:48:51
Initiate 1 IKE SA.
Ping works for 1 packet.
admin@SiteA(active)> ping source 10.1.1.1 host 100.1.1.1
PING 100.1.1.1 (100.1.1.1) from 10.1.1.1 : 56(84) bytes of data.
64 bytes from 100.1.1.1: icmp_seq=1 ttl=64 time=2.31 ms
^C
--- 100.1.1.1 ping statistics ---
5 packets transmitted, 1 received, 80% packet loss, time 4082ms
rtt min/avg/max/mdev = 2.310/2.310/2.310/0.000 ms
We are seeing the exact same behaviour from
Site A -> Site C DMZ
Site B -> Site C DMZ
Site C Internal -> Site C DMZ
Some additional info:
- This Mesh VPN was working prior to a cutover to Palo Alto firewalls. No Rules/Routing was changed, only the firewall devices. No blocks being seen on any devices between these firewalls.
- DH groups, keys, etc have been checked. The VPN establishes successfully.
- There is no Maximum Lifesize set on the tunnels.
- Checked all the static routes. Traffic is going through the correct tunnels. Traffic in the logs looks correct
- Have tried to change IPSec crypto suites
Has anyone seen similar behaviour before or have any suggestions on what we can check next? Only thing I can think is that the Palo Alto doesn't like the 2 VPNs being created on the same vsys, despite different Virtual Routers, but would have thought other people would be doing this?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-30-2022 07:23 AM
Hello,
How is routing handled, is it static or a dynamic protocol?
Regards,
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-30-2022 01:21 PM
Additionally to what @OtakarKlier mentioned, are we dealing with only PAN firewalls here? SiteA is a PAN clearly, but what firewall vendor are we working with on SiteB or SiteC?
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-30-2022 06:39 PM
@OtakarKlier - All the tunnel routing has been added statically. We also have a default route so traffic not destined for the tunnel can go out.
@BPry - All 3 are PAN firewalls
Site A - PA 3220
Site B - PA 850
Site C - PA 3250
- 2699 Views
- 3 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- S2S IPsec VPN with Multiple Domain Encryption in General Topics
- Question on PA-440 Failover in General Topics
- No ping response from AAD in Next-Generation Firewall Discussions
- Azure to OnPrem Connectivity issue in Next-Generation Firewall Discussions
- I have concern in SDWAN, Kindly help out this. in Advanced SD-WAN for NGFW Discussions