- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Is the PA-3020 adequate for SSL Decryption (and other features)?
- LIVEcommunity
- Discussions
- General Topics
- Re: Is the PA-3020 adequate for SSL Decryption (and other features)?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
Is the PA-3020 adequate for SSL Decryption (and other features)?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2019 10:17 AM
My company has 2 PA-3020 firewalls in Active/Passive configuration. They were purchased way before I started working here, so I had no input on the model that was selected. We have about 500 users in our network, and about 800 devices.
In our environment, these firewalls sit at the perimeter edge, and there are no internal firewalls (for network segmentation). We are not running ACI or VMware NSX either.
Up until about a year ago, the company was using this as a state full firewall, but had purchased all of the licenses. Since I've been here, we've been tacking on more things to the firewall such as Network Segmentation (16 security zones), and GlobalProtect VPN (for about 5 users).
We would like to start using some of the IPS features such as WildFire, Zone Based Protection, and last but not least, SSL decryption. I've been told from one source that the PA-3020's are not great at SSL decryption, and I would like to ask You, The Palo Alto community, if you think that is the case. I would like to know if getting a beff-ier firewall would be best, or if we can still use the PA-3020. Any insight you can offer would be greatly appreciated.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2019 10:39 AM
What's the current BW throughput on the firewalls? What's your average sessions per second? Can you run an ACC "SSL" application query and see how much SSL you're doing daily?
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2019 12:28 PM
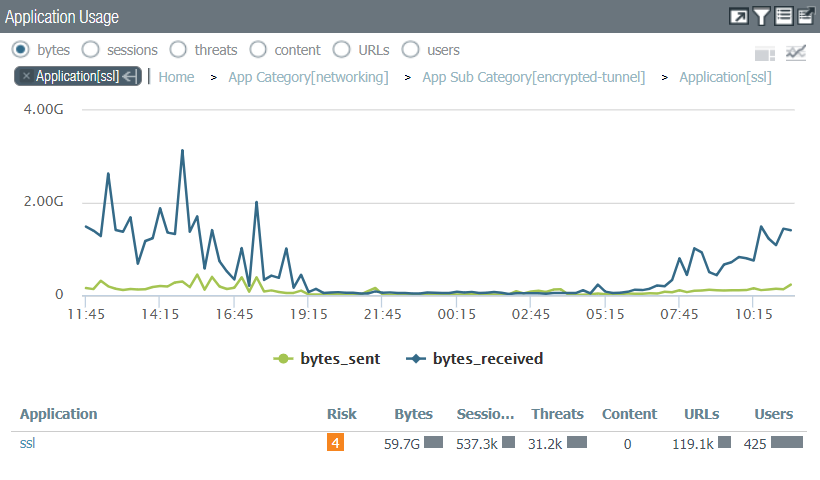
I'd say the total sessions average is somewhere between 6-10K sessions concurrently.
This is from the last 24 hours:
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-19-2019 01:36 PM
Looks like you had a little over 3GB of traffic...Now I'm not sure how much of that you'd actually decrypt...If you can try to find that number (would it match your proposed decryption policy). Given how much other throughput is probably going through your appliance and everything else you'd want to do, it might be best not to decrypt SSL.
That being said I think more needs to be done to investigate fully.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-20-2019 01:47 PM
Hello,
I would say go ahead and enable it, but be ready to disable it if needed. The 3020 is a stout box and it doenst look like you have a lot of sessions.
Hope that helps.
- Mark as New
- Subscribe to RSS Feed
- Permalink
03-20-2019 04:23 PM
While the ACC graph gives a rough idea of what your stats look like over a time period, it doesn't give us the full picture needed to really make the determination for you at all. For example, if those spikes were long-running sessions closing it doesn't actually give us an insight into what your peak is at all.
Overall you need to look at a number of criteria across your firewall and determine if that's in-line with what the PA-3020 can actually handle. We would need a bunch more numbers to make this call on your behalf. One option of course is to enable it selectively for a small group of people and scale up from their.
Keep in mind that your PA-3020 is only able to push 2 Gbps with App-ID enabled, and can only do 1 Gbps with threat prevention enabled. The 3020 as a whole can only support 7,936 concurrent decrypted sessions.
One place to start would be the show system statistics session and show system statistics application CLI commands. The first will tell you the number of active sessions, a breakout of session type, current throughput, and what your packet rate is. The second will display the top 20 applications currently on the firewall. Look for ssl and monitor both throughout the day to see if your 3020 will handle your traffic flow.
- 7140 Views
- 5 replies
- 0 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Use of SSL Decryption. in Next-Generation Firewall Discussions
- No SSL Decyrption with content Inspection Enabled. in Next-Generation Firewall Discussions
- Should Advanced Threat Prevention ( Inline ML ) and Wildfire Analysis be enabled if we dont have a decryption policy enabled ? in Next-Generation Firewall Discussions
- What are the capabilities of Cortex XDR without endpoint agents and just with PANOS firewall integration like an NDR solution? in Cortex XDR Discussions
- Debug Dataplane Help in General Topics