- Access exclusive content
- Connect with peers
- Share your expertise
- Find support resources
Click Preferences to customize your cookie settings.
Unlock your full community experience!
Microsoft Intune Autopilot Problems
- LIVEcommunity
- Discussions
- General Topics
- Re: Microsoft Intune Autopilot Problems
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-20-2021 03:15 PM
We have this Intune process that our team goes through every time a new PC is issued to the user. Essentially this is an autopilot program that after the client is wiped, it starts downloading programs that are pre defined in our Intune configuration package. Once all of these programs are installed the Intune process is completed successfully.
The problem we're seeing is that every time we run this process behind a palo alto firewall the downloading of the programs hangs. It gets stuck at installing 1 of 20 or 2 of 20 and after a while it eventually times out.
To get passed this, I have followed the guidance from Microsoft on whitelisting IPs and FQDNs that are used by the Intune process.
https://docs.microsoft.com/en-us/mem/intune/fundamentals/intune-endpoints
I have also whitelisted all IPs and FQDNs from Office 365:
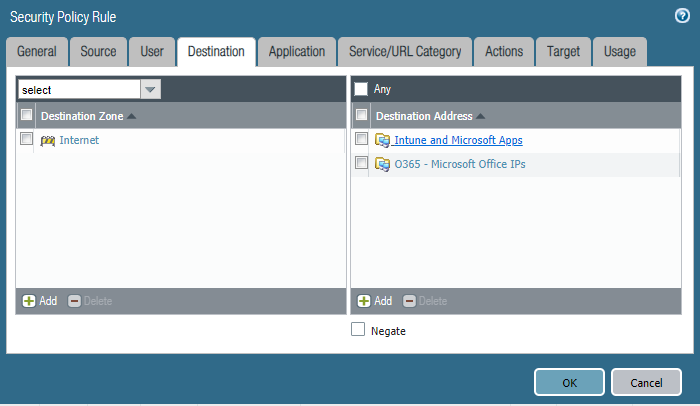
The way I am applying these rules is that I am allowing all communication to the IP's that I grabbed from the above mentioned URLs, and allowed all communication to go through those IPs with no app-id or security profile restriction.
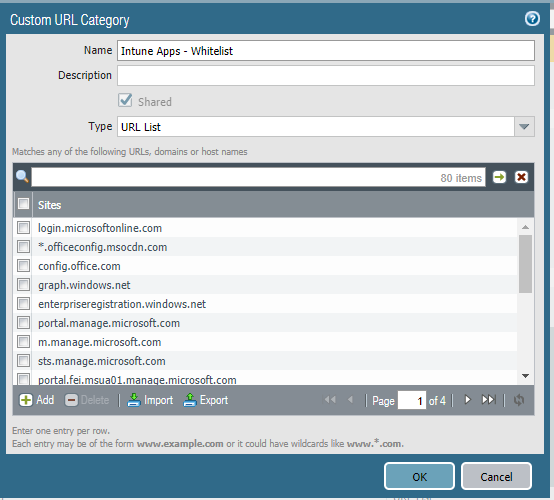
I also whitelisted all FQDNs (including wildcards) and I inserted them in the Service/URL Category in a separate policy. Same thing for this policy as well, no app-id or security profile restriction applied.
The order that these policies are applied:
1. Unrestricted Microsoft/Office 365 IP Whitelist
2. Restricted Policy for General use (Through app-id and security profiles)
3. Unrestricted Microsoft FQDN and Wildcard Whitelist.
The reason why I left Microsoft FQDN and Wildcard Whitelist last is because those Wildcards (specifically) sometimes resolve to AWS, Google, and Akamai IPs and I don't like that traffic being unprotected.
Note that for testing purposes I have moved the third policy that whitelists wildcards above the general internet policy, and I have experienced the same intuning issues.
I just wanted to see if other people are experiencing the same intune problems and what they've done to resolve it. The firewall policy that's in the middle of the screenshot below is where the traffic gets to be restricted through app-id and security profiles (including URL filtering that is blocking 20 different categories).
Accepted Solutions
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2021 09:16 AM
Have you turned off the Content ID piece that permits partial downloads?
We are discovering that this blocks the Delivery Optimization capability of WIn10 and Autopilot/Intune. Turn it back on and build is magic and quick. PAN technote says that this is best practice to be off to prevent malware doing partial download to evade detection but it also breaks legitimate services and ideally should be managable on a per rule basis.
Interestingly i have found if you turn off all profiles even wtih that Content-ID setting as On the build in my environment works just fine
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-20-2021 11:55 PM
Hi @CCullhaj ,
Your approach seems correct.
Have you identified why the process hangs ? I mean, is there anything being blocked or dropped at the time ?
If you don't see anything in traffic/threat logs, then I'd recommend checking the global counters for drop counters.
Cheers,
-Kiwi.
Cheers,
Kiwi
Please help out other users and “Accept as Solution” if a post helps solve your problem !
Read more about how and why to accept solutions.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04-21-2021 07:41 AM
Thanks for your reply. That's correct, I do not see any drops or denies.
I will have to check the global counters thought. My thinking is that all these CDNs and Proxy requests that could be going during the download process the firewall is blocking them somehow.
If the global counters show that requests are being blocked, what is the next step that you would recommend?
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-20-2021 06:07 AM
Have you made any progress on this? We are having similar issues.
- Mark as New
- Subscribe to RSS Feed
- Permalink
05-20-2021 07:00 AM
Not really, I am still testing different security policies. When I disabled file blocking, and wild fire the intune process went through. But then after I enabled them again I got mixed results.
What I did was a packet capture during the intune process. I noticed that host was making DNS queries to hosts that are not listed in the Microsoft's documentation to be whitelisted. However, since I know those DNS queries were done during the intune process I extracted them from the packet capture and added them to the whitelist.
End result, still having problems. I in the middle of confirming now if the list of FQDNS and IP whitelisting are not enough and there are additional or if the security profiles are messing up the traffic. I am sharing with you the list of FQDNs that I got from the packet capture, Microsoft documentation and different blogs. I don't know if it's going to be handy to you but worth trying:
login.microsoftonline.com
*.officeconfig.msocdn.com
config.office.com
graph.windows.net
enterpriseregistration.windows.net
portal.manage.microsoft.com
m.manage.microsoft.com
sts.manage.microsoft.com
portal.fei.msua01.manage.microsoft.com
m.fei.msua01.manage.microsoft.com
portal.fei.amsua0102.manage.microsoft.com
m.fei.amsua0102.manage.microsoft.com
portal.fei.msua02.manage.microsoft.com
m.fei.msua02.manage.microsoft.com
portal.fei.msua04.manage.microsoft.com
m.fei.msua04.manage.microsoft.com
portal.fei.msua05.manage.microsoft.com
m.fei.msua05.manage.microsoft.com
portal.fei.amsua0502.manage.microsoft.com
m.fei.amsua0502.manage.microsoft.com
portal.fei.msua06.manage.microsoft.com
m.fei.msua06.manage.microsoft.com
portal.fei.amsua0602.manage.microsoft.com
m.fei.amsua0602.manage.microsoft.com
fei.amsua0202.manage.microsoft.com
portal.fei.amsua0202.manage.microsoft.com
m.fei.amsua0202.manage.microsoft.com
portal.fei.amsua0402.manage.microsoft.com
m.fei.amsua0402.manage.microsoft.com
portal.fei.msua07.manage.microsoft.com
portal.fei.amsua0702.manage.microsoft.com
portal.fei.amsua0801.manage.microsoft.com
portal.fei.msua08.manage.microsoft.com
m.fei.msua07.manage.microsoft.com
m.fei.amsua0702.manage.microsoft.com
m.fei.msua08.manage.microsoft.com
m.fei.amsua0801.manage.microsoft.com
portal.fei.msub01.manage.microsoft.com
m.fei.msub01.manage.microsoft.com
portal.fei.amsub0102.manage.microsoft.com
m.fei.amsub0102.manage.microsoft.com
portal.fei.msub02.manage.microsoft.com
m.fei.msub02.manage.microsoft.com
portal.fei.msub03.manage.microsoft.com
m.fei.msub03.manage.microsoft.com
portal.fei.msub05.manage.microsoft.com
m.fei.msub05.manage.microsoft.com
portal.fei.amsub0202.manage.microsoft.com
m.fei.amsub0202.manage.microsoft.com
portal.fei.amsub0302.manage.microsoft.com
m.fei.amsub0302.manage.microsoft.com
portal.fei.amsub0502.manage.microsoft.com
m.fei.amsub0502.manage.microsoft.com
portal.fei.amsub0601.manage.microsoft.com
m.fei.amsub0601.manage.microsoft.com
portal.fei.msuc01.manage.microsoft.com
m.fei.msuc01.manage.microsoft.com
portal.fei.msuc02.manage.microsoft.com
m.fei.msuc02.manage.microsoft.com
portal.fei.msuc03.manage.microsoft.com
m.fei.msuc03.manage.microsoft.com
portal.fei.msuc05.manage.microsoft.com
m.fei.msuc05.manage.microsoft.com
portal.fei.amsud0101.manage.microsoft.com
m.fei.amsud0101.manage.microsoft.com
fef.msuc03.manage.microsoft.com
Admin.manage.microsoft.com
wip.mam.manage.microsoft.com
mam.manage.microsoft.com
*.manage.microsoft.com
*.do.dsp.mp.microsoft.com
*.dl.delivery.mp.microsoft.com
*.emdl.ws.microsoft.com
*.download.windowsupdate.com
*.delivery.mp.microsoft.com
*.notify.windows.com
*.wns.windows.com
*.notify.live.net
login.live.com
*.microsoftaik.azure.net
*.c-msedge.net
*.akamai.net
*.azure.com
*.microsoft.com
*.harvest.int
*.onehs.us
*.sfd.local
*.windows.com
*.windowsupdate.com
*.cloudfront.net
*.deepinstinctweb.com
*.hpanalytics.net
*.hpdaas.com
*.akamaiedge.net
*.intel.com
*.live.com
*.azure.net
*.edgesuite.net
*.cloudapp.net
*.akadns.net
*.kappacdn.net
*.fb-t-msedge.net
*.trafficmanager.net
*.msftconnecttest.com
*.msedge.net
*.prod.do.dsp.mp.microsoft.com
cs9.wac.phicdn.net
emdl.ws.microsoft.com
.windowsupdate.com
*.update.microsoft.com
tsfe.trafficshaping.dsp.mp.microsoft.com
cy2.settings.data.microsoft.com.akadns.net
settings.data.microsoft.com
settings-win.data.microsoft.com
*.e-msedge.net
*.s-msedge.net
nexusrules.officeapps.live.com
ocos-office365-s2s.msedge.net
officeclient.microsoft.com
outlook.office365.com
client-office365-tas.msedge.net
www.office.com
onecollector.cloudapp.aria
v10.events.data.microsoft.com
self.events.data.microsoft.com
to-do.microsoft.com
wdcp.microsoft.com
definitionupdates.microsoft.com
go.microsoft.com
*.smartscreen.microsoft.com
smartscreen-sn3p.smartscreen.microsoft.com
unitedstates.smartscreen-prod.microsoft.com
storecatalogrevocation.storequality.microsoft.com
store-images.microsoft.com
md.mp.microsoft.com
*.displaycatalog.mp.microsoft.com
displaycatalog.mp.microsoft.com
pti.store.microsoft.com
storeedgefd.dsx.mp.microsoft.com
markets.books.microsoft.com
share.microsoft.com
dmd.metaservices.microsoft.com
v10.vortex-win.data.microsoft.com
www.microsoft.com
co4.telecommand.telemetry.microsoft.com
cs11.wpc.v0cdn.net
cs1137.wpc.gammacdn.net
modern.watson.data.microsoft.com
watson.telemetry.microsoft.com
licensing.mp.microsoft.com
wd-prod-fe.cloudapp.azure.com
ris-prod-atm.trafficmanager.net
validation-v2.sls.trafficmanager.net
ctldl.windowsupdate.com
inference.location.live.net
location-inference-westus.cloudapp.net
login.msa.akadns6.net
us.configsvc1.live.com.akadns.net
*.search.msn.com
arc.msn.com
g.msn.com
query.prod.cms.rt.microsoft.com
ris.api.iris.microsoft.com
browser.pipe.aria.microsoft.com
config.edge.skype.com
s2s.config.skype.com
skypeecs-prod-usw-0-b.cloudapp.net
blob.weather.microsoft.com
tile-service.weather.microsoft.com
cdn.onenote.net
twimg.com
candycrushsoda.king.com
evoke-windowsservices-tas.msedge.net
wallet.microsoft.com
mediaredirect.microsoft.com
int.whiteboard.microsoft.com
wbd.ms
whiteboard.microsoft.com
whiteboard.ms
www.bing.com
exo-ring.msedge.net
fp.msedge.net
fp-vp.azureedge.net
odinvzc.azureedge.net
spo-ring.msedge.net
*.g.akamaiedge.net
maps.windows.com
g.akamaiedge.net
iecvlist.microsoft.com
www.msftconnecttest.com
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-18-2021 09:16 AM
Have you turned off the Content ID piece that permits partial downloads?
We are discovering that this blocks the Delivery Optimization capability of WIn10 and Autopilot/Intune. Turn it back on and build is magic and quick. PAN technote says that this is best practice to be off to prevent malware doing partial download to evade detection but it also breaks legitimate services and ideally should be managable on a per rule basis.
Interestingly i have found if you turn off all profiles even wtih that Content-ID setting as On the build in my environment works just fine
- Mark as New
- Subscribe to RSS Feed
- Permalink
06-25-2021 07:06 PM
Very interesting, I've never heard about this previously. I will give this a try and let you know how it goes. Thanks for your reply.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-07-2021 03:01 PM
Ok so I too your suggestion and enabled the HTTP partial response, and I got to say that in my first Intune try I did see instant positive results!
Worth saying that the Intune process still failed, but just by enabled HTTP partial response I got to install 8/9 of apps and then the process failed at the last app and eventually intune timed out.
This was only through the partial response option, I had disabled all the aforementioned IP/FQDN whitelisting. Maybe by combining the IP/FQDN whitelisting and HTTP Partial response I should get it to work. That's going to be my next try!
I'll keep you posted on my results.
- Mark as New
- Subscribe to RSS Feed
- Permalink
07-14-2021 03:31 PM
Thank you very much for the tip Mathew! Your solution worked like a charm! As soon as I enabled HTTP partial response, the intune autopilot process went through in no time.
I do have to also mention that I had to also use the whitelist that I have posted above, due to the URL filtering restrictions. Before I enabled the HTTP partial response, it didn't matter how many URL's I whitelisted or how much I tweaked the actual policies, nothing was working. But now everything is good.
Cheers!
- 1 accepted solution
- 28326 Views
- 8 replies
- 2 Likes
Show your appreciation!
Click Accept as Solution to acknowledge that the answer to your question has been provided.
The button appears next to the replies on topics you’ve started. The member who gave the solution and all future visitors to this topic will appreciate it!
These simple actions take just seconds of your time, but go a long way in showing appreciation for community members and the LIVEcommunity as a whole!
The LIVEcommunity thanks you for your participation!
- Global Protect being interrupted by Copilot? in GlobalProtect Discussions
- The user information linked in the CIE does not match the match criteria in the GP's application settings. in Prisma Access Discussions
- Microsoft Intune and Autopilot Hybrid AD Join via Prisma in Prisma Access Discussions
- Cortex 8.2.1 gives problems with Windows 11 24h2 on my laptop. Microsoft Office apps won't start in Cortex XDR Discussions
- Problem bei Installation eines Cortex XDR Clients 8.0.1.33809 (Win, 64 Bit, msi) auf Microsoft Surface Pro 9 5G ,Prozessor: Microsoft SQ3 (ARM64) in Cortex XDR Discussions